Mesaje de eroare
... 749 N/A Invalid phone number. 750 N/A Invalid authentication attempt. 751 Fix ...
... 749 N/A Invalid phone number. 750 N/A Invalid authentication attempt. 751 Fix ...
Chapter 11
... – Includes an integrated circuit • Contains some non-volatile memory and a simple microprocessor ...
... – Includes an integrated circuit • Contains some non-volatile memory and a simple microprocessor ...
Smart Wireless THUM Adapter
... The THUM Adapter communicates and derives power from a standard 4-20 mA/HART loop. The THUM Adapter causes a small voltage drop on the loop which is linear from 2.25 V at 3.5 mA to 1.2 V at 25 mA. Under fault conditions, the maximum voltage drop is 2.5 V. The THUM Adapter will not affect the 4-20 mA ...
... The THUM Adapter communicates and derives power from a standard 4-20 mA/HART loop. The THUM Adapter causes a small voltage drop on the loop which is linear from 2.25 V at 3.5 mA to 1.2 V at 25 mA. Under fault conditions, the maximum voltage drop is 2.5 V. The THUM Adapter will not affect the 4-20 mA ...
List of 40 Websites That Offer Phone Records
... claims, "This report is for informational purposes only. This is not for use in court. If you need the records for court, you will need to subpoena the records directly from the carrier." Additionally, the site attempts to disclaim knowledge of illegal activities in obtaining records: "Non-Internet ...
... claims, "This report is for informational purposes only. This is not for use in court. If you need the records for court, you will need to subpoena the records directly from the carrier." Additionally, the site attempts to disclaim knowledge of illegal activities in obtaining records: "Non-Internet ...
01 - Quick Heal
... 2013 saw constant innovation from malware authors. While Internet becomes ubiquitous with its need in business, and private life, cybercrime and espionage adapt to new methods. The growing acceptance of the “Internet of things” has created new attack platforms and critical infrastructure vulnerabili ...
... 2013 saw constant innovation from malware authors. While Internet becomes ubiquitous with its need in business, and private life, cybercrime and espionage adapt to new methods. The growing acceptance of the “Internet of things” has created new attack platforms and critical infrastructure vulnerabili ...
Manual: Smart Wireless THUM™ Adapter
... The THUM Adapter communicates and derives power from a standard 4-20 mA/HART loop. The THUM Adapter causes a small voltage drop on the loop which is linear from 2.25 V at 3.5 mA to 1.2 V at 25 mA. Under fault conditions, the maximum voltage drop is 2.5 V. The THUM Adapter will not affect the 4-20 mA ...
... The THUM Adapter communicates and derives power from a standard 4-20 mA/HART loop. The THUM Adapter causes a small voltage drop on the loop which is linear from 2.25 V at 3.5 mA to 1.2 V at 25 mA. Under fault conditions, the maximum voltage drop is 2.5 V. The THUM Adapter will not affect the 4-20 mA ...
Application research and analysis based on Bitlocker
... then Windows 7 operating system uses of Bitlocker encryption system boot disk in the case of without installingtrusted platform module of TPM1.2 version. Encryption started, open the desktop icon, select the system disk (C:), click the right key and chooseBitlocker (B), requires the startup key when ...
... then Windows 7 operating system uses of Bitlocker encryption system boot disk in the case of without installingtrusted platform module of TPM1.2 version. Encryption started, open the desktop icon, select the system disk (C:), click the right key and chooseBitlocker (B), requires the startup key when ...
Project proposal
... What is a Bluetooth stack? • In short, to get any functionality out of a Bluetooth device, one needs to implement pretty high stack of protocol layers, quite similar to OSI referent model • If you buy a Bluetooth device, you get that stack already implemented, and it exposes profiles(services) to t ...
... What is a Bluetooth stack? • In short, to get any functionality out of a Bluetooth device, one needs to implement pretty high stack of protocol layers, quite similar to OSI referent model • If you buy a Bluetooth device, you get that stack already implemented, and it exposes profiles(services) to t ...
Foundation Fieldbus
... patible with H1, a number of H1 devices, such as temperature multiplexers, are taking advantage of the MAI block. The most novel of the new blocks, however, is the Fully Flexible Function Block (FFB), as it is able to be fully programmed by the end user, using any of the IEC 61131-1 programming lan ...
... patible with H1, a number of H1 devices, such as temperature multiplexers, are taking advantage of the MAI block. The most novel of the new blocks, however, is the Fully Flexible Function Block (FFB), as it is able to be fully programmed by the end user, using any of the IEC 61131-1 programming lan ...
Protecting the FPGA Design From Common Threats
... Though the definition of zeroization involves a clear plus verification that all data was cleared, most applications will benefit from a zeroization which clears all memory cells of the FPGA. The Cyclone III LS zeroization solution breaks out the clear function and the verification function to provi ...
... Though the definition of zeroization involves a clear plus verification that all data was cleared, most applications will benefit from a zeroization which clears all memory cells of the FPGA. The Cyclone III LS zeroization solution breaks out the clear function and the verification function to provi ...
Cryptanalysis of Stream Cipher
... No security reduction but easy to analyze Not resistant to nonce reuse No incremental tags Flexible implementation sizes: 128/256 Performance: speed/size ...
... No security reduction but easy to analyze Not resistant to nonce reuse No incremental tags Flexible implementation sizes: 128/256 Performance: speed/size ...
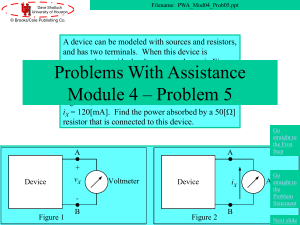
PWA_Mod04_Prob05_v05
... the device has two terminals, and it A device can be modeled with sources and resistors, is made up of sources and resistors. and has two terminals. When this device is Thus, we can use Norton’s theorem connected to an ideal voltmeter, as shown in Figure to model the device. Once we have the Norton ...
... the device has two terminals, and it A device can be modeled with sources and resistors, is made up of sources and resistors. and has two terminals. When this device is Thus, we can use Norton’s theorem connected to an ideal voltmeter, as shown in Figure to model the device. Once we have the Norton ...
LED and Button Descriptions Powerline 500 (2
... security button on one of the other AV adapters in your existing network for 2 seconds. Both buttons must be pressed within 2 minutes. Note: The Security button does not work in power saving mode (see “Power LED is amber” in the Troubleshooting Tips table). Press the Reset button for 1 second, then ...
... security button on one of the other AV adapters in your existing network for 2 seconds. Both buttons must be pressed within 2 minutes. Note: The Security button does not work in power saving mode (see “Power LED is amber” in the Troubleshooting Tips table). Press the Reset button for 1 second, then ...
Devireddy
... which includes destination IP address, he can flip relevant bits to make the destination system to send the packet to his own system and transmit it using some mobile station. attacking using table of appropriate initialization vectors. Here the attacker can build table of IVs, if he knows the pla ...
... which includes destination IP address, he can flip relevant bits to make the destination system to send the packet to his own system and transmit it using some mobile station. attacking using table of appropriate initialization vectors. Here the attacker can build table of IVs, if he knows the pla ...
Mobile Communications
... Many research efforts in mobile computing and wireless networks try to hide the fact that the network access has been changed or that a wireless link is more error prone than a wired one. Examples: Mobile IP tries to hide that fact of changing access points by redirecting packets but keeping the sam ...
... Many research efforts in mobile computing and wireless networks try to hide the fact that the network access has been changed or that a wireless link is more error prone than a wired one. Examples: Mobile IP tries to hide that fact of changing access points by redirecting packets but keeping the sam ...
Apply encryption to network and system security
... There may be key management issues – numerous key pairs required, digital signatures and CA (certificate authority) required. Implementation will be determined by the business or organisation needs and requirements. Most operating systems and storage systems have inbuilt encryption facilities. Imple ...
... There may be key management issues – numerous key pairs required, digital signatures and CA (certificate authority) required. Implementation will be determined by the business or organisation needs and requirements. Most operating systems and storage systems have inbuilt encryption facilities. Imple ...
Slides
... getting the status of devices (routers, switches, network file servers, etc.). When stuff is configured, SNMP sets are done to write the correct values to the MIBs on the devices. E.g., you could change the default route on all routers with a set of SNMP set requests. Or clear all ARP caches. ...
... getting the status of devices (routers, switches, network file servers, etc.). When stuff is configured, SNMP sets are done to write the correct values to the MIBs on the devices. E.g., you could change the default route on all routers with a set of SNMP set requests. Or clear all ARP caches. ...
What Does It Mean when a Board Test Passes?
... many devices. A typical board test is made up of many simple and complex tests, the collection of which is intended to test as many potential defects as possible. This is called board test coverage (see section 4). At first it may seem appropriate to ask, “What does it mean when a test fails?” but t ...
... many devices. A typical board test is made up of many simple and complex tests, the collection of which is intended to test as many potential defects as possible. This is called board test coverage (see section 4). At first it may seem appropriate to ask, “What does it mean when a test fails?” but t ...
Slide 1
... A small software agent that runs on Windows PCs and monitors for wireless exposures and threats, and notifies the user and AirDefense Enterprise. Continuous anywhere monitoring for mobile users on the road or at their office Detects & notifies 50+ configuration, connectivity issues and attacks ...
... A small software agent that runs on Windows PCs and monitors for wireless exposures and threats, and notifies the user and AirDefense Enterprise. Continuous anywhere monitoring for mobile users on the road or at their office Detects & notifies 50+ configuration, connectivity issues and attacks ...
Packaging Information: Data Compression and
... not as efficient since they require longer keys and more computing in the encryption and decryption processes For sake of efficiency, sometimes secret key encryption is used and the secret key is communicated employing public key methods -the combination of a secret key encoded message and public ke ...
... not as efficient since they require longer keys and more computing in the encryption and decryption processes For sake of efficiency, sometimes secret key encryption is used and the secret key is communicated employing public key methods -the combination of a secret key encoded message and public ke ...
Heterogeneous Cellular Networks: From Theory to Practice
... than the threshold for that tier β i and the coverage probability is the complement. The outage and coverage p c are thus the CDF and complementary CDF of the SINR random variable, respectively. To be explicit, pc is the probability that the maximum SINR (x i ) over all base stations is greater than ...
... than the threshold for that tier β i and the coverage probability is the complement. The outage and coverage p c are thus the CDF and complementary CDF of the SINR random variable, respectively. To be explicit, pc is the probability that the maximum SINR (x i ) over all base stations is greater than ...
Three challenges with secret key encryption
... A brute -force attack is applying all possible value of a key to the algorithm until you succeed in deciphering the message. The longer the key space the more difficult is to learn the key in brute force attack. The issue of the number of bits required in a key to ensure secure encryption is controv ...
... A brute -force attack is applying all possible value of a key to the algorithm until you succeed in deciphering the message. The longer the key space the more difficult is to learn the key in brute force attack. The issue of the number of bits required in a key to ensure secure encryption is controv ...
Voltage Protection with Automatic Cell Balance For 2-Cell Li
... capacitance on the CD pin. Upon expiration of the internal timer, the OUT pin changes from a low to high state. 8.1.2 Cell Balancing If enabled, the bq2920x performs automatic cell-balance correction where the two cells are automatically corrected for voltage imbalance by loading the cell with the h ...
... capacitance on the CD pin. Upon expiration of the internal timer, the OUT pin changes from a low to high state. 8.1.2 Cell Balancing If enabled, the bq2920x performs automatic cell-balance correction where the two cells are automatically corrected for voltage imbalance by loading the cell with the h ...
MultiRack Setup Instruction
... console or I/O sample rate; this field cannot be edited. Ø Network Latency sets the network latency value. This field allows you to change SoundGrid network throughput latency. This value sets the buffering delay used by the processing engine(s) and affects SoundGrid’s end-to-end latency. Plugins t ...
... console or I/O sample rate; this field cannot be edited. Ø Network Latency sets the network latency value. This field allows you to change SoundGrid network throughput latency. This value sets the buffering delay used by the processing engine(s) and affects SoundGrid’s end-to-end latency. Plugins t ...
Guide to Firewalls and Network Security with Intrusion Detection and
... CPU resources and time Bastion host that hosts the firewall should be robust enough to manage encryption and other security functions Encrypted packets may need to be padded to uniform length to ensure that some algorithms work effectively Can result in slowdowns Monitoring can burden system adminis ...
... CPU resources and time Bastion host that hosts the firewall should be robust enough to manage encryption and other security functions Encrypted packets may need to be padded to uniform length to ensure that some algorithms work effectively Can result in slowdowns Monitoring can burden system adminis ...