* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Machine language
Survey
Document related concepts
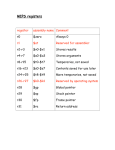
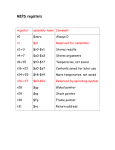
Transcript
Chapter 7 Low-Level Programming Languages Nell Dale • John Lewis Chapter Goals • List the operations that a computer can perform • Discuss the relationship between levels of abstraction and the determination of concrete algorithm steps • Describe the important features of the Pep/7 virtual machine • Distinguish between immediate mode addressing and direct addressing • Convert a simple algorithm into a machine-language program 7-2 Chapter Goals (cont.) • Distinguish between machine language and assembly language • Describe the steps in creating and running an assemblylanguage program • Convert a simple algorithm into an assembly-language program • Distinguish between instructions to the assembler and instructions to be translated • Describe two approaches to testing • Design and implement a test plan for a simple assemblylanguage program 7-3 Computer Operations • A computer is a programmable electronic device that can store, retrieve, and process data • Data and instructions to manipulate the data are logically the same and can be stored in the same place • Store, retrieve, and process are actions that the computer can perform on data 7-4 Machine Language • Machine language: the instructions built into the hardware of a particular computer • Initially, humans had no choice but to write programs in machine language because other programming languages had not yet been invented 7-5 Machine Language • Every processor type has its own set of specific machine instructions • The relationship between the processor and the instructions it can carry out is completely integrated • Each machine-language instruction does only one very low-level task 7-6 Pep/7: A Virtual Computer • A virtual computer is a hypothetical machine designed to contain the important features of real computers that we want to illustrated • Pep/7 – designed by Stanley Warford – has 32 machine-language instructions • We are only going to examine a few of these instructions 7-7 Features in Pep/7 • The memory unit is made up of 4,096 bytes of storage • Pep/7 has seven registers, three of which we focus on at this point – The program counter (PC) (contains the address of the next instruction to be executed) – The instruction register (IR) (contains a copy of the instruction being executed) – The accumulator (A register) • Pep/7 has four status bits, of which we examine two: – N: 1 if the A register is negative, 0 otherwise – Z: 1 if the A register is zero, 0 otherwise 7-8 Features in Pep/7 Figure 7.1 Pep/7’s architecture 7-9 Instruction Format • There are two parts to an instruction – The 8-bit instruction specifier – And optionally, the 16-bit operand specifier Figure 7.2 The Pep/7 instruction format 7-10 Instruction Format • The instruction specifier is made up of several sections – The operation code – The register specifier – The addressing-mode specifier 7-11 Instruction Format • The operation code specifies which instruction is to be carried out • The 1-bit register specifier is 0 if register A (the accumulator) is involved in the operation and 1 if register X (the index register) is involved. In the examples discussed in the textbook, The register specifier is always 0. • The 2-bit addressing-mode specifier says how to interpret the operand part of the instruction 7-12 Instruction Format Figure 7.3 Difference between immediate-mode and direct-mode addressing 7-13 Some Sample Instructions unary instruction Figure 7.3 Subset of Pep/7 instructions 7-14 Example Instructions • LOAD – 00001 0 00 (08) 0000 0000 0000 0111 (00 07) – 00001 0 01 (09) 0000 0000 0001 1111 (00 1F) • STORE – 00010 0 01 (11) 0000 0000 0000 1010 (00 0A) 7-15 Example Instructions • ADD – 00011 0 00 (18) 0000 0010 0000 1010 (02 0A) – 00011 0 01 (19) 0000 0010 0000 1010 (02 0A) • Character Input to operand – 11011 0 01 (D9) 0000 0000 0000 1010 (00 0A) • Character Output from operand – 11100 0 00 (E0) 0000 0000 0100 0001 (00 41) – 11100 0 01 (E1) 0000 0000 0000 1010 (00 0A) (65)10, 參考 第 3 章, A one byte 7-16 A Program Example • Let’s write "Hello" on the screen Page 211, 程式 Ch05/Pr0504.odc 7-17 Pep/7 Simulator • A program that behaves just like the Pep/7 virtual machine behaves • To run a program, we enter the hexadecimal code, byte by byte with blanks between each Page 202 7-18 Assembly Language • Assembly languages: assign mnemonic letter codes to each machine-language instruction – The programmer uses these letter codes in place of binary digits – A program called an assembler reads each of the instructions in mnemonic form and translates it into the machine-language equivalent 7-19 Pep/7 Assembly Language Page 216 7-20 Pseudo-Operations Pseudo-Op Operand Meaning .ASCII /…/ Store the characters between the / / into memory .BLOCK d#3 Generate three bytes of storage and set each byte to zero .WORD d#5 Generate a word with the decimal value 5 stored in it .WORD h#0105 Generate a word with the hexadecimal value 0105 stored in it .END Signals the end of the assemblylanguage program 7-21 Figure 7.5 Assembly Process 7-22 A New Program Page 219 類似程式 Ch05/Pr0512.odc 7-23 Our Completed Program Page 221 Status Bits • Status bits allow a program to make a choice – BRLT: if N is 1, then set the Program Counter (PC) to the operand (N is 1 means A register is less than 0) – BREQ: if Z is 1, then set the Program Counter (PC) to the operand (Z is 1 means A register is equal to 0) – Example program • Ch06/Pr0602.odc • Ch06/Pr0604.odc 7-25 Testing • Test plan: a document that specifies how many times and with what data the program must be run in order to thoroughly test the program • A code-coverage approach designs test cases to ensure that each statement in the program is executed. This is also called clear-box testing. • Data-coverage testing is another approach; it designs test cases to ensure that the limits of the allowable data are covered. This is also called black-box testing. 7-26 Ethical Issues: Software Piracy, Copyrighting • Research indicated that, globally, 11.5 billion dollars were lost in the year 2000 to pirated software • Advocates of open-source code believe that a program’s original source code should be in the public domain • Respecting the copyrights of software, if it is not open code, is important from a number of perspectives 7-27