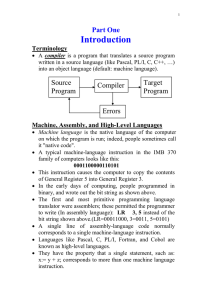
Writing a Compiler
... Error handling implements the compiler's response to errors in the code it is compiling. When an error is detected, the error handler must tell the user about it (what kind and where it occurred). It might also apply some makeshift fix-up (fixing the error during the compilation process to move ...
... Error handling implements the compiler's response to errors in the code it is compiling. When an error is detected, the error handler must tell the user about it (what kind and where it occurred). It might also apply some makeshift fix-up (fixing the error during the compilation process to move ...
Machine-Level Programming
... Instruction Set Architecture Software Architecture vs. Hardware Architecture Common Architecture Classifications ...
... Instruction Set Architecture Software Architecture vs. Hardware Architecture Common Architecture Classifications ...
euler.slu.edu
... Instruction Set Architecture Software Architecture vs. Hardware Architecture Common Architecture Classifications ...
... Instruction Set Architecture Software Architecture vs. Hardware Architecture Common Architecture Classifications ...
Characteristics of virtualized environment
... That can be used without interfering with other tasks because they do not access shared resources. Ex. Arithmetic , floating & fixed point. ...
... That can be used without interfering with other tasks because they do not access shared resources. Ex. Arithmetic , floating & fixed point. ...
PeachPy: A Python Framework for Developing High-Performance Assembly Kernels Marat Dukhan
... tools and support for a wider range of usecases. For instance, PeachPy makes it easier to write software pipelined code and to emulate newer instruction sets using older instructions. Another important PeachPy-enabled use-case is creating fat binaries with versions for multiple instruction sets or m ...
... tools and support for a wider range of usecases. For instance, PeachPy makes it easier to write software pipelined code and to emulate newer instruction sets using older instructions. Another important PeachPy-enabled use-case is creating fat binaries with versions for multiple instruction sets or m ...
Computer architecture anc instruction set design
... This implies an advantage to choosing the latter architecture, since programs coded on it should be generally smaller than those coded on the other architecture (see the IBM 1130/META 4A benchmark in a later section for a specific example). One of the most probable misconceptions in evaluating speed ...
... This implies an advantage to choosing the latter architecture, since programs coded on it should be generally smaller than those coded on the other architecture (see the IBM 1130/META 4A benchmark in a later section for a specific example). One of the most probable misconceptions in evaluating speed ...
05~Chapter 5_Target_..
... • This set of operations is referred to as the fetchexecute cycle – The computer runs this cycle at a furious pace, never stopping, regardless of the meaning of the instructions • You can point a processor's instruction fetch logic at a long string of floating point numbers and it will blithely begi ...
... • This set of operations is referred to as the fetchexecute cycle – The computer runs this cycle at a furious pace, never stopping, regardless of the meaning of the instructions • You can point a processor's instruction fetch logic at a long string of floating point numbers and it will blithely begi ...
Chapter 5
... • This set of operations is referred to as the fetchexecute cycle – The computer runs this cycle at a furious pace, never stopping, regardless of the meaning of the instructions • You can point a processor's instruction fetch logic at a long string of floating point numbers and it will blithely begi ...
... • This set of operations is referred to as the fetchexecute cycle – The computer runs this cycle at a furious pace, never stopping, regardless of the meaning of the instructions • You can point a processor's instruction fetch logic at a long string of floating point numbers and it will blithely begi ...
Machine language
... data are logically the same and can be stored in the same place • Store, retrieve, and process are actions that the computer can perform on data ...
... data are logically the same and can be stored in the same place • Store, retrieve, and process are actions that the computer can perform on data ...
Instruction Set Principles
... Design, especially ISA appropriate for compilers • 1990s: Computer Architecture Course = Design of CPU, memory system, I/O system, Multiprocessors ...
... Design, especially ISA appropriate for compilers • 1990s: Computer Architecture Course = Design of CPU, memory system, I/O system, Multiprocessors ...
A Lesson on Instruction Set Architectures (ISAs)
... Registers are small and fast In future lessons, we’ll learn how main memory extends this storage ...
... Registers are small and fast In future lessons, we’ll learn how main memory extends this storage ...
Slide 1
... The purpose of parallel processing is to speed up the computer processing capability and increase its throughput, that is, the amount of processing that can be accomplished during a given interval of time. The amount of hardware increases with parallel processing, and with it, the cost of the system ...
... The purpose of parallel processing is to speed up the computer processing capability and increase its throughput, that is, the amount of processing that can be accomplished during a given interval of time. The amount of hardware increases with parallel processing, and with it, the cost of the system ...
PPT
... Additional logic for floating point registers, easily extended from what we have now. Memory rollback logic; this is more substantial, for we need to retire memory writes only on invariant confirmation. A program to generate the verifying program automatically. ...
... Additional logic for floating point registers, easily extended from what we have now. Memory rollback logic; this is more substantial, for we need to retire memory writes only on invariant confirmation. A program to generate the verifying program automatically. ...
Multicore, parallelism, and multithreading
... that its iterations can be executed on separate processors concurrently Identify dependences between references -independent actions can operate in parallel ...
... that its iterations can be executed on separate processors concurrently Identify dependences between references -independent actions can operate in parallel ...
Chapter 7 - McMaster Computing and Software
... times and with what data the program must be run in order to thoroughly test the program • A code-coverage approach designs test cases to ensure that each statement in the program is executed. • A data-coverage approach designs test cases to ensure that the limits of the allowable data are ...
... times and with what data the program must be run in order to thoroughly test the program • A code-coverage approach designs test cases to ensure that each statement in the program is executed. • A data-coverage approach designs test cases to ensure that the limits of the allowable data are ...
Chapter 7
... times and with what data the program must be run in order to thoroughly test the program • A code-coverage approach designs test cases to ensure that each statement in the program is executed. • A data-coverage approach designs test cases to ensure that the limits of the allowable data are ...
... times and with what data the program must be run in order to thoroughly test the program • A code-coverage approach designs test cases to ensure that each statement in the program is executed. • A data-coverage approach designs test cases to ensure that the limits of the allowable data are ...
Chapter 7: Low-Level Programming Languages
... times and with what data the program must be run in order to thoroughly test the program • A code-coverage approach designs test cases to ensure that each statement in the program is executed. • A data-coverage approach designs test cases to ensure that the limits of the allowable data are ...
... times and with what data the program must be run in order to thoroughly test the program • A code-coverage approach designs test cases to ensure that each statement in the program is executed. • A data-coverage approach designs test cases to ensure that the limits of the allowable data are ...
Low-Level Programming Languages
... data are logically the same and can be stored in the same place • Store, retrieve, and process are actions that the computer can perform on data ...
... data are logically the same and can be stored in the same place • Store, retrieve, and process are actions that the computer can perform on data ...
Chapter 9
... • Pipelining is an "assembly line–like" process for handling instruction execution. • See figure 9.12 ...
... • Pipelining is an "assembly line–like" process for handling instruction execution. • See figure 9.12 ...
EECS 252 Graduate Computer Architecture Lec 01
... • Make input and output easier than wiring circuit boards and reading lights • Make programming easier by developing higher level programming languages, so that users did not need to use binary machine code instructions – First compilers in late 1950’s, for Fortran and Cobol ...
... • Make input and output easier than wiring circuit boards and reading lights • Make programming easier by developing higher level programming languages, so that users did not need to use binary machine code instructions – First compilers in late 1950’s, for Fortran and Cobol ...
Assembly 1
... function of the instruction, so they are quite often referred to as mnemonics, meaning memory aids. 5. Instruction types The entire range of instructions available is called the Instruction Set. The programmer sees registers (by name) and memory (usually by byte address). The programmer sees the ALU ...
... function of the instruction, so they are quite often referred to as mnemonics, meaning memory aids. 5. Instruction types The entire range of instructions available is called the Instruction Set. The programmer sees registers (by name) and memory (usually by byte address). The programmer sees the ALU ...