* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download virtual machine
Library (computing) wikipedia , lookup
Burroughs MCP wikipedia , lookup
Berkeley Software Distribution wikipedia , lookup
Mobile operating system wikipedia , lookup
Plan 9 from Bell Labs wikipedia , lookup
Distributed operating system wikipedia , lookup
Security-focused operating system wikipedia , lookup
Copland (operating system) wikipedia , lookup
Process management (computing) wikipedia , lookup
Spring (operating system) wikipedia , lookup
Chapter 2: Operating-System
Structures
Chapter 2: Operating-System
Structures
•
•
•
•
•
•
OS Services
The Interface
System Calls
Types of System Calls
System Programs
OS Design and
Implementation
•
•
•
•
OS Structure
Virtual Machines
OS Generation
System Boot
Objectives
• To describe the services an operating system
provides to users, processes, and other
systems
• To discuss the various ways of structuring an
operating system
• To explain how operating systems are installed
and customized and how they boot
Operating System Services
(an easy-to-use OS)
• User interface
• File-system
manipulation
– Command-Line (CLI),
Graphics User
Interface (GUI), Batch
• Program execution
– load a program, run
that program and end
execution (normally or
abnormally)
• I/O operations
– Including a file or an
I/O device
– read/write/create/del
ete files and
directories
– search them
– list file Information
– permission
management
Operating System Services (Cont.)
(an easy-to-use OS)
• Communications
– on the same computer or between computers
– shared memory or through message passing
• Error detection
– May occur in the CPU and memory hardware, in
I/O devices, in user program
– OS should take the appropriate action to ensure
correct and consistent computing
– OS should provide debugging facilities
Operating System Services (Cont.)
(for ensuring the efficient)
• Resource allocation
– When multiple programs running concurrently,
resources must be allocated to each of them
• Accounting
– To keep track of which users use how much and what
kinds of computer resources
• Protection and security
– Protection
• ensuring that all access to system resources is controlled
– Security
• outsiders requires user authentication
• defending external I/O devices from invalid access attempts
– A chain is only as strong as its weakest link.
User Operating System Interface - CLI
• Sometimes implemented in kernel,
sometimes by system programs
• Sometimes multiple flavors implemented –
shells
– Bash, csh… (Unix-like systems)
• Primarily fetches a command from user and
executes it
– Sometimes commands built-in, sometimes just
names of programs
– If the latter, adding new features doesn’t
require shell modification
CLI
MS-DOS
BusyBox (for embedded OS)
User Operating System Interface - GUI
• User-friendly desktop metaphor interface
– Usually mouse, keyboard, and monitor
– Icons represent files, programs, actions, etc
– Various mouse buttons over objects in the interface cause
various actions
– Invented at Xerox PARC
• Many systems now include both CLI and GUI interfaces
– Microsoft Windows
– Apple Mac OS X
– UNIX is CLI with optional GUI interfaces
• Touch programs
– HTC & Apple
GUI
HTC (WinCE + “HTC UI”)
Apple (Unix + “Apple UI”)
G-sensor + touch screen
GUI
Tablet PC (without keyboard)
Tablet PC (with keyboard)
System Calls
• Programming interface to the services provided
by the OS
– Typically written in a high-level language (C or C++)
– Mostly accessed by programs via a high-level
Application Program Interface (API) (e.g., libc)
• Three most common APIs
– Win32 API for Windows
– POSIX API
– Java API
• Why use APIs rather than system calls?
Linux 2.6.18 (unix-like, POSIX, ~300)
Example of System Calls
#include <stdio.h>
int main()
{
printf("hello world\n\n");
}
Example of System Calls
# gcc test.c --static
# strace ./a.out
Example of System Calls
execve("./a.out", ["./a.out"], [/* 25 vars */]) = 0
uname({sys="Linux", node="Lonux-svr", ...}) = 0
brk(0)
= 0x8408000
brk(0x8408cb0)
= 0x8408cb0
set_thread_area({entry_number:-1 -> 6, base_addr:0x8408830, limit:1048575,
seg_32bit:1, contents:0, read_exec_only:0, limit_in_pages:1,
seg_not_present:0, useable:1}) = 0
brk(0x8429cb0)
= 0x8429cb0
brk(0x842a000)
= 0x842a000
fstat64(1, {st_mode=S_IFCHR|0620, st_rdev=makedev(136, 1), ...}) = 0
mmap2(NULL, 4096, PROT_READ|PROT_WRITE,
MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0xb7fb5000
write(1, "hello world\n", 12hello world
)
= 12
write(1, "\n", 1
)
=1
exit_group(13)
=?
Example of System Calls
# strace -c ./a.out
hello world
#include <stdio.h>
int main()
{
printf("hello world\n\n");
}
% time seconds usecs/call calls errors syscall
------ ----------- ----------- --------- --------- ---------------nan 0.000000
0
2
write
nan 0.000000
0
1
execve
nan 0.000000
0
4
brk
nan 0.000000
0
1
uname
nan 0.000000
0
1
mmap2
nan 0.000000
0
1
fstat64
nan 0.000000
0
1
set_thread_area
------ ----------- ----------- --------- --------- ---------------100.00 0.000000
11
total
System Call Implementation
• Typically, a number associated with each system call
– System-call interface maintains a table indexed according
to these numbers
• The system call interface invokes intended system call
in OS kernel and returns status of the system call and
any return values
• The caller need know nothing about how the system
call is implemented
– Just needs to understand what OS will do
– Most details of OS interface hidden from programmer by
API
• printf, scanf,… (libc) for example
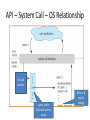
API – System Call – OS Relationship
Sys call
handler
jump_table
(function pointer
array)
Return &
modechange
System Call Parameter Passing
• Often, more information is required than
simply identity of desired system call
• Three general methods used to pass
parameters to the OS
– Simplest: pass the parameters in registers
– Parameters stored in a block, or table, in memory,
and address of block passed as a parameter in a
register
– Parameters placed, or pushed, onto the stack by
the program and popped off the stack by the
operating system
Types of System Calls
• Process control
• File management
• Device management
• Information maintenance
• Communications
MS-DOS execution
(a) At system startup (b) running a program
FreeBSD Running Multiple Programs
Solaris 10 dtrace Following System Call
Linux: systemtap
http://sourceware.org/systemtap/getinvolved.html
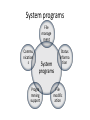
System programs
File
manage
ment
Commu
nication
s
System
programs
Progra
mming
support
Status
informa
tion
File
modific
ation
Operating System Design and Implementation
• Design and Implementation of OS not “solvable”, but
some approaches have proven successful
• Internal structure of different Operating Systems can
vary widely
• Start by defining goals and specifications
• Affected by choice of hardware, type of system
• User goals and System goals
– User goals – operating system should be convenient to use,
easy to learn, reliable, safe, and fast
– System goals – operating system should be easy to design,
implement, and maintain, as well as flexible, reliable,
error-free, and efficient
Operating System Design and Implementation (Cont.)
• Important principle to separate
Policy: What will be done?
Mechanism: How to do it?
• Mechanisms determine how to do something,
policies decide what will be done
• The separation of policy from mechanism is a
very important principle, it allows maximum
flexibility if policy decisions are to be changed
later
Simple Structure
• MS-DOS – written to provide the most
functionality in the least space
– Not divided into modules
– Although MS-DOS has some structure, its
interfaces and levels of functionality are not well
separated
MS-DOS Layer Structure
Layered Approach
• The operating system is divided into a number
of layers (levels), each built on top of lower
layers. The bottom layer (layer 0), is the
hardware; the highest (layer N) is the user
interface.
• With modularity, layers are selected such that
each uses functions (operations) and services
of only lower-level layers
Layered Operating System
UNIX
• UNIX – limited by hardware functionality, the
original UNIX operating system had limited
structuring.
• The UNIX OS consists of two separable parts
– Systems programs
– The kernel
• Consists of everything below the system-call interface and
above the physical hardware
• Provides the file system, CPU scheduling, memory
management, and other operating-system functions; a large
number of functions for one level
UNIX System Structure
Microkernel System Structure
• Moves as much from the kernel into “user” space
• Communication takes place between user modules
using message passing
• Benefits:
–
–
–
–
Easier to extend a microkernel
Easier to port the operating system to new architectures
More reliable (less code is running in kernel mode)
More secure
• Detriments:
– Performance overhead of user space to kernel space
communication
Mac OS X Structure
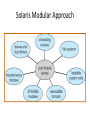
Modules
• Most modern operating systems implement
kernel modules
– Uses object-oriented approach
– Each core component is separate
– Each talks to the others over known interfaces
– Each is loadable as needed within the kernel
• Overall, similar to layers but with more flexible
Solaris Modular Approach
Virtual Machines
• A virtual machine takes the layered approach
to its logical conclusion. It treats hardware
and the operating system kernel as though
they were all hardware
• A virtual machine provides an interface
identical to the underlying bare hardware
• The operating system creates the illusion of
multiple processes, each executing on its own
processor with its own (virtual) memory
Virtual Machines (Cont.)
• The resources of the physical computer are
shared to create the virtual machines
– CPU scheduling can create the appearance that
users have their own processor
– Spooling and a file system can provide virtual card
readers and virtual line printers
– A normal user time-sharing terminal serves as the
virtual machine operator’s console
Virtual Machines (Cont.)
Virtual Machines (Cont.)
• The virtual-machine concept provides
complete protection of system resources
• A virtual-machine system is a perfect vehicle
for operating-systems research and
development.
• The virtual machine concept is difficult to
implement due to the effort required to
provide an exact duplicate to the underlying
machine. (???)
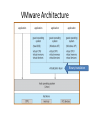
VMware Architecture
Binary translation
x86 virtualization
• Software techniques
– Virtualization software (e.g., VMWare) for the x86
must employ binary translation techniques to
trap and virtualize the execution of certain
instructions.
– Paravirtualization does not implement the hardto-virtualize parts of the actual x86 instruction set.
• Operating systems are ported to run on the resulting
virtual machine
x86 virtualization
• Hardware support
– Intel Virtualization Technology (IVT)
– AMD virtualization (AMD-V)
X86
Monitor mode
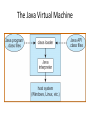
The Java Virtual Machine
Operating System Generation
• Operating systems are designed to run on any of
a class of machines; the system must be
configured for each specific computer site
• SYSGEN program obtains information concerning
the specific configuration of the hardware system
• Booting – starting a computer by loading the
kernel
• Bootstrap program – code stored in ROM that is
able to locate the kernel, load it into memory,
and start its execution
System Boot
• Operating system must be made available to
hardware so hardware can start it
– Small piece of code – bootstrap loader, locates
the kernel, loads it into memory, and starts it
– Sometimes two-step process where boot block at
fixed location loads bootstrap loader
– When power initialized on system, execution
starts at a fixed memory location
• Firmware used to hold initial boot code
Virtual machines
• Equivalence
A program running under the VMM should exhibit a behavior essentially
identical to that demonstrated when running on an equivalent
machine directly.
• Resource control
The VMM must be in complete control of the virtualized resources.
• Efficiency
A statistically dominant fraction of machine instructions must be
executed without VMM intervention.
ISA & VM
• Privileged instructions
– Those that trap if the processor is in user mode and do not trap if it is
in system mode.
• Control sensitive instructions
– Those that attempt to change the configuration of resources in the
system.
• Behavior sensitive instructions
– Those whose behavior or result depends on the configuration of
resources (the content of the relocation register or the processor's
mode).
ISA & VM
Theorem:
For any conventional third generation computer,
a VMM may be constructed if the set of
sensitive instructions for that computer is a
subset of the set of privileged instructions.
ISA & VM
• critical instructions
– sensitive but unprivileged instructions
– dynamic recompilation
– Paravirtualization
• a virtualization technique that presents a software
interface to virtual machines that is similar but not
identical to that of the underlying hardware