* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Knowledge Management in Defense
Data vault modeling wikipedia , lookup
Expense and cost recovery system (ECRS) wikipedia , lookup
Information security wikipedia , lookup
Computer security wikipedia , lookup
Enterprise content management wikipedia , lookup
Information privacy law wikipedia , lookup
Open data in the United Kingdom wikipedia , lookup
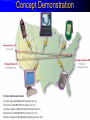
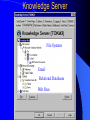
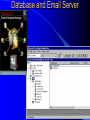
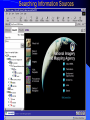
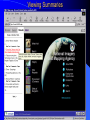
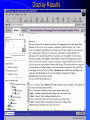
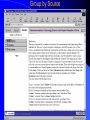
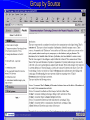
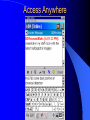
Knowledge Management in Defense Workshop October 29, 2001 1pm - 4pm Jeffrey A. Goldman, Ph.D. Senior KM Strategist Dennis M. Scanlon General Dynamics Advanced Information Systems Lockheed Martin Vice President, West Region Randall Jackson District Sales Manager Verity Panel Discussion (3pm) What are the greatest hurdles plaguing the adoption of Knowledge Management in the Defense community as compared to commercial industry and how can they be overcome? Knowledge Management Center of Excellence Jeffrey A. Goldman, Ph.D. Thanh Diep, Ph.D. Howie Fleck Randall Jackson Kai Dai, Ph.D. GENERAL DYNAMICS Information Systems & Technology Aerospace Systems Combat Systems Advanced Marine Systems Information Systems Network Systems C4 Systems Decision Systems General Dynamics UK LTD. Knowledge Management Similarities of the Corporate world versus Defense We are in the business of selling products/services Capture corporate knowledge Collaborate with partners Filter the information and tools relevant to my job Security breach = lost sales How do I sell more widgets? We are in the business of information superiority Capture analyst knowledge Collaborate with other agencies Filter & synthesize the information relevant to my job Security breach = lost battles Where is the next most likely terrorist activity going to take place? Additional Defense Requirements Compartmentalized and multi-level security Satellite imagery analysis Geo-spatial referenced data Foreign language analysis Knowledge Management Scenarios Signals Intelligence (Commercial) – Ultimately be able to monitor multiple public information sources for “suspicious activity” – Automatically cue reports from private data sources – Data is mostly text Intelligence Operations – Detect operational centers that the enemy uses – Signal data Imagery Operations – Ultimately be able to monitor multiple public information sources for “suspicious activity” – Data is mostly satellite imagery Vendors Started with more than 200 products identified – Grows with each group meeting and conference attended Focused attention on fifty-seven products Products supplied by forty-three different vendors Demonstrations and/or phone conferences with seventeen vendors Products evaluated against functional requirements Requirement process 1.1.1.1 The natural language mining request input function allows the users to input a generic request that may require both data retrieval and data mining to be resolved. The actual data retrieval and data mining required will be resolved by the profiles maintain by the knowledge marting function. Vendor review Technical functionality Business model Financial risk and stability Cost Compatibility Knowledge Management Challenges No single end-to-end solution Individual vendors provide only a 10-60% solution Overlap in functionality Limited API’s and modularity Limited defense community oriented solutions (e-commerce) Products change in internet time (they’ve already changed!) Products are not mature A true enterprise information and application portal is not yet available Capabilities Portal - Customized to User/Mission (tools, presentation, etc.) Access/Search – User driven requests against multiple databases of disparate format – Contextual retrieval of content Collaboration Dissemination (tasking, reports) Knowledge transfer/process persistence Application integration Concept Demonstration Portal Server Customized web pages & applications Screen real-estate Application navigation Portal Server Portal Server Knowledge Server File Systems Email Relational Databases Web Sites Database and Email Server Searching Information Sources Viewing Summaries Display Results Group by Source Group by Source Access Anywhere Customer Benefits Unified/personalized/consolidated view of information, tools, and assets Ability to access distributed and heterogeneous data sources – Backward compatibility to existing data sources – Upward compatibility of future data sources Ability to contextually search large volumes of data Ability to capture both products and production process Improved customer/analyst feedback and product refinement Value added by General Dynamics Internet/Intranet market understanding KM domain knowledge KM tool knowledge Integration of KM tools into an end-to-end solution Ongoing research and commitment General Dynamics Branding Customer & Community knowledge – SIGINT, IO, IMINT, MASINT, ELINT – NIMA, PHD, NSA, CIA Intelligence community security approach What are the greatest hurdles plaguing the adoption of Knowledge Management in the Defense community as compared to commercial industry and how can they be overcome? Culture and Security Commercial Build my empire A few multi-level security, inter/intra different levels, networks, customer access, partner access Defense Build my information silo agency, coalition, separate “splinternets”