* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download ppt
Survey
Document related concepts
Transcript
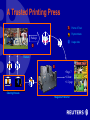
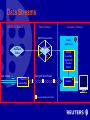
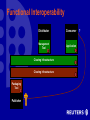
W3C Workshop on Digital Rights Management Dr David Parrott Sophia Antipolis, January 2001 Reuters Customer a straw-man sketch • • • • • A business A professional consumer of data A manager of networked systems A user of automated processes A discerning owner of infrastructure • Example Customers: – – – – – Banks Newspapers Corporate Treasuries Farmers’ Cooperatives Broadcasters • Example Processes: – – – Printing and Publishing Financial Trading Audio/Video Editing Reuters Products • Information – – – – – multimedia news (including: text, still pictures, audio/video) financial data transactional data editorial content research reports • Electronic Delivery Modes – – – – – discrete content files continuous streams of discrete updates in real-time historical data searches transaction processing proprietary networks and Internet delivery Some Reasons why Reuters needs to “Permission” its Data • The data is inherently valuable • Service offerings contain lots of “slice and dice” • Broadcast mode delivery is required in many cases for scalability; permissioning restricts access to just those parts paid for • Distribution channels are flexible and varied (e.g., proprietary networks, satellite broadcast, public Internet) • Third party content is fundamental and comes with complex and exacting rules for distribution (regulatory) • Data flows are multi-directional and permissions also cover contribution rights Problems with Today’s DRM • Heavy bias towards “Eyes and Ears” • Total Lack of Interoperability – Rights Mark-up – Operational / functional • Concentration on prevention of copyright theft – nothing done about detection or action after the event • No real support for B2B / business customers • “Fair Use” / other complex models not supported Eyes and Ears… Title: BRU04:BELGIUM-OWL:ANTWERP,BELGIUM,18FEB97 Author: nk/Photo by Nathalie Koulischer REUTERS Description: A nine-day-old Burrowing Owl chick is fed water through a syringe by a zoo keeper February 18 at Antwerp zoo. It is the first time that a Burrowing Owl chick has been hatched at the zoo. The chick, a native of North America, weighed 8.3 grammes when it came out of the egg and now weighs 24.6g. Machines are Consumers too! A Trusted Printing Press T Points of Trust Payment data Package i Usage data T Reuters i T • Page 7 • Colour i T T i • 1/2 page Clearing Houses Magazine Publisher Machines are Consumers too! Automatic Position-Keeping Market Data Automatic Trading Data Streams Publisher’s Domain Public Domain DRM-Protected Rules Business Rules T Data Stream Trusted T Stream-filter Customer’s Domain Trusted Application System Associates Rights with Encoded Stream Encrypted Data Stream Decoder Encoded Identification Packet T T Interoperability • Rights Markup • Functional Interoperability A Typical Closed Trust System Publisher Distributor Packaging Tool Management Tool T Consumer Application T T Clearing Infrastructure T • Closed Authentication • Bespoke applications • Closed Crypto Keys/Management – Components • Interoperability not required – Taking content “out of the box” • Proprietary Rights Markup Interoperable Rights Markup • ODRL – IPRSystems • XrML – ContentGuard • … • Work still to do… – Extensibility – Fair Use – Generalised contractual obligation – B2B – Generalised credential management – … Functional Interoperability Distributor Management Tool T Clearing Infrastructure Clearing Infrastructure Packaging Tool T Publisher Consumer Application T T T ? Interoperable Data Containers Control Data Rights/Rules Content • crypto • trust links • registration • etc. • XML • rules: • XML • components • data types • etc. payments access ctls • clearing • apps • etc. What part, if any, might PKI play? • Authentication – – – – Users Credentials Applications Infrastructure components • Transaction protocols – Non-repudiation/Audit trails between clearing infrastructures • Session-key management protocols • PKI-style networks of trust (TTPs?) Today’s DRM Prevention Only Prevention Detection Action Detection (Traitor Tracing) Consumer Application T Adds Watermark (“fingerprint”) Action (using the law) Source: http://www.wired.com Revisit the Reuters Customer Centralised staff admin Well-defined Cost Centres Tight control over infrastructure (RDBMS, PKI, Desktop apps, DRM solutions,… ) DB The Server Special Applications A Future for DRM? • Reuters needs Permissioning – DRM is one possible solution among many – In its current form DRM is inadequate • Open Standards / Interoperability required – In “rules” (XML) and for operational interfaces • Additional technologies – PKI, Smartcards (trust on the card), Digital Watermarking, Traitor Tracing techniques (detection vs. prevention) Thank you for listening Any questions?