07 Exceptions
... • If possible and appropriate, try to recover from the exception ‒ depends on the problem spec, nature of the exception ...
... • If possible and appropriate, try to recover from the exception ‒ depends on the problem spec, nature of the exception ...
Statistical Models for Steganography - uni
... Larger the cover message – Easier to hide message ...
... Larger the cover message – Easier to hide message ...
Java Exception Handling Presentation
... provide its own error handling methodology. In the previous example we chose the first strategy. ...
... provide its own error handling methodology. In the previous example we chose the first strategy. ...
Data layout transformation exploiting memory-level
... allowing usages relying on the default layout such as addressing logically adjacent elements through hard-coded pointer arithmetic. Therefore, programmers opting to use automatic transformations on arrays must be subject to more stringent interfaces that insulate the source code from changes in the ...
... allowing usages relying on the default layout such as addressing logically adjacent elements through hard-coded pointer arithmetic. Therefore, programmers opting to use automatic transformations on arrays must be subject to more stringent interfaces that insulate the source code from changes in the ...
Integrating High-Performance Polynomial Arithmetic into Maple
... degree of any of the input polynomials. The Maple code of this solver (which is specialized in solving two equations in two variables) is relatively short, about 100 lines. From modpn, it makes use of its basic polynomial operations, such as polynomial GCD, evaluation and interpolation. One can see ...
... degree of any of the input polynomials. The Maple code of this solver (which is specialized in solving two equations in two variables) is relatively short, about 100 lines. From modpn, it makes use of its basic polynomial operations, such as polynomial GCD, evaluation and interpolation. One can see ...
A Note on the Dispersion of Network Problems
... splitting the generating matrix into two sub-matrices (one for each user). The sum of codewords is indistinguishable from a codeword of the single-user code with R = R1 + R2 . This leads to the following proposition. Proposition 3 ( [9]): Consider a linear MAC channel. Any error probability which is ...
... splitting the generating matrix into two sub-matrices (one for each user). The sum of codewords is indistinguishable from a codeword of the single-user code with R = R1 + R2 . This leads to the following proposition. Proposition 3 ( [9]): Consider a linear MAC channel. Any error probability which is ...
Software Release Notes
... The Sign button moves next to Print button to make it easier to click the Sign button after navigating within the attachment. iKnowMed now prefetches PDFs to speed up viewing attachments. When prefetching a PDF, a prompt may appear asking, "Do you want to load ActiveX content?" To permanently dismis ...
... The Sign button moves next to Print button to make it easier to click the Sign button after navigating within the attachment. iKnowMed now prefetches PDFs to speed up viewing attachments. When prefetching a PDF, a prompt may appear asking, "Do you want to load ActiveX content?" To permanently dismis ...
PyStream: Compiling Python onto the GPU
... GPU architectures: memory bandwidth. GPUs pack enough functional units into a single chip that overall performance can easily be limited by the memory subsystem’s ability to feed data to the functional units. Ease of programming is not the only issue when using GPU-specific languages. These language ...
... GPU architectures: memory bandwidth. GPUs pack enough functional units into a single chip that overall performance can easily be limited by the memory subsystem’s ability to feed data to the functional units. Ease of programming is not the only issue when using GPU-specific languages. These language ...
Slide 1
... 1. Our goal was to answer the question: Are correlations important for decoding? 2.We developed a quantitative information-theoretic measure, DI, which is an upper bound on the information loss associated with ignoring correlations. 3. For pairs of neurons, DI/I is small, < 12%, except in the LGN wh ...
... 1. Our goal was to answer the question: Are correlations important for decoding? 2.We developed a quantitative information-theoretic measure, DI, which is an upper bound on the information loss associated with ignoring correlations. 3. For pairs of neurons, DI/I is small, < 12%, except in the LGN wh ...
Succinct Data Structure
... Davoodi et al. showed how to support select-inorder for binary tree We simply plug our compression into this framework Need to support two additional operations: is_chain_prefix/suffix Decompress fingerprints, use lookup tables: tree + inorder position ...
... Davoodi et al. showed how to support select-inorder for binary tree We simply plug our compression into this framework Need to support two additional operations: is_chain_prefix/suffix Decompress fingerprints, use lookup tables: tree + inorder position ...
Network Coding: An Overview
... received a+c at first and received a after a certain period of time, c is delayed and cannot be recovered until all the information necessary to recover are received (i.e. a) [5]. Synchronization is a problem that needs to be considered when network coding will be implemented in computer or satellit ...
... received a+c at first and received a after a certain period of time, c is delayed and cannot be recovered until all the information necessary to recover are received (i.e. a) [5]. Synchronization is a problem that needs to be considered when network coding will be implemented in computer or satellit ...
here - DocuTrac
... Add appt_status field to Retrive Appointment Details screen to assist therapist in selection of correct appt for note Enhancement – QDE/ AccuMed When writing a note: If a client has two appointments in AccuMed for the day (one cancelled, one arrived), Retrieve Appointment Details brings back two a ...
... Add appt_status field to Retrive Appointment Details screen to assist therapist in selection of correct appt for note Enhancement – QDE/ AccuMed When writing a note: If a client has two appointments in AccuMed for the day (one cancelled, one arrived), Retrieve Appointment Details brings back two a ...
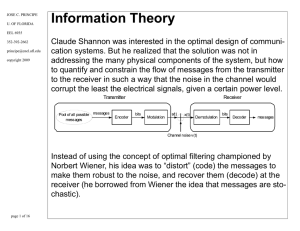
Information Theory
... • How do you select the best transmission rate? • How do you optimal recover signals corrupted by noise? Shannon presented answers to ALL of the above: • He derived entropy to describe the uncertainty in a message set • From entropy he enunciated the Source Coding theorem • He proposed Mutual inform ...
... • How do you select the best transmission rate? • How do you optimal recover signals corrupted by noise? Shannon presented answers to ALL of the above: • He derived entropy to describe the uncertainty in a message set • From entropy he enunciated the Source Coding theorem • He proposed Mutual inform ...
PIDA Bar Code, Label, and Information Compliance
... PIDA Bar Code, Label, and Information Compliance Program The goal is to provide up-to-date and useful information to PIDA members in an easy to understand format so the entire supply chain can become more efficient. One of the greatest inefficiencies is found on the receiving dock. Executives and ma ...
... PIDA Bar Code, Label, and Information Compliance Program The goal is to provide up-to-date and useful information to PIDA members in an easy to understand format so the entire supply chain can become more efficient. One of the greatest inefficiencies is found on the receiving dock. Executives and ma ...
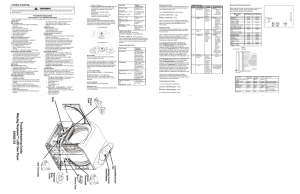
Troubleshooting Guide Maytag Neptune™ LED Gas Dryer 6390 2110
... keys for 2 seconds, will start a Membrane Pad Switch Test. To exit the test at any point, press the same keys again for 2 seconds or press the OFF key to exit Service Mode. Diagnostic Codes The Diagnostic Codes are identified when the severity level of the abnormality detected is higher and service ...
... keys for 2 seconds, will start a Membrane Pad Switch Test. To exit the test at any point, press the same keys again for 2 seconds or press the OFF key to exit Service Mode. Diagnostic Codes The Diagnostic Codes are identified when the severity level of the abnormality detected is higher and service ...
Gastrointestinal stromal tumors icd 10
... Cytogenet Oncol Haematol. ON THIS PAGE: You will learn about the different ways doctors use to treat people with this type of tumor. To see other pages, use the menu on the side of your screen. ON THIS PAGE: You will find out more about body changes and other things that can signal a problem that ma ...
... Cytogenet Oncol Haematol. ON THIS PAGE: You will learn about the different ways doctors use to treat people with this type of tumor. To see other pages, use the menu on the side of your screen. ON THIS PAGE: You will find out more about body changes and other things that can signal a problem that ma ...
Self-Adaptive Niching Differential Evolution and Its Application
... Compared to other niching algorithms, the advantage of NCjDE is free from control parameter adjustment. This paper also focuses on the problem of semi-fragile watermarking for two-dimensional (2D) color barcodes in which the appropriate barcode colors and watermark are unknown. Over the last two or ...
... Compared to other niching algorithms, the advantage of NCjDE is free from control parameter adjustment. This paper also focuses on the problem of semi-fragile watermarking for two-dimensional (2D) color barcodes in which the appropriate barcode colors and watermark are unknown. Over the last two or ...
Programming of Handheld and Mobile Devices
... • Several tools are available that help you build, test, and debug Palm OS applications: • see http://www.palmos.com/dev/tools/ for information about your development language and tool options. • The book Palm OS Programming Development Tools Guide describes the PalmSource-provided debugging tools a ...
... • Several tools are available that help you build, test, and debug Palm OS applications: • see http://www.palmos.com/dev/tools/ for information about your development language and tool options. • The book Palm OS Programming Development Tools Guide describes the PalmSource-provided debugging tools a ...
Data Warehousing/Mining
... – In practice, use rules of thumb – Tool: DBDSGN [IBM Almaden], RDT for System R ...
... – In practice, use rules of thumb – Tool: DBDSGN [IBM Almaden], RDT for System R ...
PythonTEX Quickstart
... 100 lines of template code—and basic support can Customizing typesetting require less than 20 lines. If you would like support for a new language, please open an issue at GitHub. PythonTEX typesets code using the fancyvrb packThe main documentation also contains a summary of age and the fvextra pack ...
... 100 lines of template code—and basic support can Customizing typesetting require less than 20 lines. If you would like support for a new language, please open an issue at GitHub. PythonTEX typesets code using the fancyvrb packThe main documentation also contains a summary of age and the fvextra pack ...
Computer Architecture at Berkeley
... • Computation spread over globe – initial conditions never same! – Even writers of software surprised by behavior ...
... • Computation spread over globe – initial conditions never same! – Even writers of software surprised by behavior ...
Coding theory

Coding theory is the study of the properties of codes and their fitness for a specific application. Codes are used for data compression, cryptography, error-correction and more recently also for network coding. Codes are studied by various scientific disciplines—such as information theory, electrical engineering, mathematics, and computer science—for the purpose of designing efficient and reliable data transmission methods. This typically involves the removal of redundancy and the correction (or detection) of errors in the transmitted data.There are four types of coding: Data compression (or, source coding) Error correction (or channel coding) Cryptographic coding Line codingData compression and error correction may be studied in combination.Source encoding attempts to compress the data from a source in order to transmit it more efficiently. This practice is found every day on the Internet where the common Zip data compression is used to reduce the network load and make files smaller.The second, channel encoding, adds extra data bits to make the transmission of data more robust to disturbances present on the transmission channel. The ordinary user may not be aware of many applications using channel coding. A typical music CD uses the Reed-Solomon code to correct for scratches and dust. In this application the transmission channel is the CD itself. Cell phones also use coding techniques to correct for the fading and noise of high frequency radio transmission. Data modems, telephone transmissions, and NASA all employ channel coding techniques to get the bits through, for example the turbo code and LDPC codes.