a medical automation system using li-fi technology and
... Before this above mentioned technology, there was many issues related to wireless transmission protocols. It consist of many issues related limited range, high power consumption, limited bandwidth of transmission of data. Reduces in performance of data transmission process. It can be easily hacked b ...
... Before this above mentioned technology, there was many issues related to wireless transmission protocols. It consist of many issues related limited range, high power consumption, limited bandwidth of transmission of data. Reduces in performance of data transmission process. It can be easily hacked b ...
The Soundex Indexing System
... PROBLEM: Interested in your genealogy? Trying to find a long lost friend? To search large databases such as the US Census records, you need to use the Soundex Indexing System. The soundex is a coded surname (last name) index based on the way a surname sounds rather than the way it is spelled. Surnam ...
... PROBLEM: Interested in your genealogy? Trying to find a long lost friend? To search large databases such as the US Census records, you need to use the Soundex Indexing System. The soundex is a coded surname (last name) index based on the way a surname sounds rather than the way it is spelled. Surnam ...
Index Symbol Type
... – Better performance • Most decisions are done at compile time (eg. memory references) • Compile once, execute may times ...
... – Better performance • Most decisions are done at compile time (eg. memory references) • Compile once, execute may times ...
ELJO SYS 8K
... The frequency range of 868MHZ-870 MHZ is applied for high-frequency systems for industrial, scientific, medical, domestic and similar purposes (ISM). A protection against interferences caused by the devices and radio remote control systems mentioned above cannot be guaranteed when operating in this ...
... The frequency range of 868MHZ-870 MHZ is applied for high-frequency systems for industrial, scientific, medical, domestic and similar purposes (ISM). A protection against interferences caused by the devices and radio remote control systems mentioned above cannot be guaranteed when operating in this ...
IST722 Data Warehousing
... • Some ETL tool assist with processing this logic. • Degenerate dimensions can be used ex: transaction number in order summary • A combination of dimension keys ex: StudentKey and ClassKey for grade processing. ...
... • Some ETL tool assist with processing this logic. • Degenerate dimensions can be used ex: transaction number in order summary • A combination of dimension keys ex: StudentKey and ClassKey for grade processing. ...
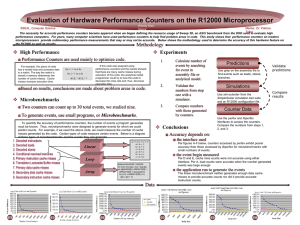
Evaluation of Hardware Performance Counters on the R12000
... performance computers. For years, many computer scientists have used performance counters to help find problem areas in code. This study shows that performance counters on modern microprocessors provide rudimentary performance measurements that may or may not be accurate. Below shows the methodology ...
... performance computers. For years, many computer scientists have used performance counters to help find problem areas in code. This study shows that performance counters on modern microprocessors provide rudimentary performance measurements that may or may not be accurate. Below shows the methodology ...
Source Document Source Data
... Define some experimental terms: Blinding/Randomization/Breaking Blind Retention of Samples: condition for storage, re use of the sample, how long, destruction after completion of the trial ...
... Define some experimental terms: Blinding/Randomization/Breaking Blind Retention of Samples: condition for storage, re use of the sample, how long, destruction after completion of the trial ...
Stand Up For Your Beliefs
... Precisely because right versus right is harder than right versus wrong ...
... Precisely because right versus right is harder than right versus wrong ...
pulse modulation
... approximation mq(t) can't follow closely the actual curve of the message signal m(t ). In contrast to slope-overload distortion, granular noise occurs when is too large relative to the local slope characteristics of m(t). granular noise is similar to quantization noise in PCM. •It seems that a lar ...
... approximation mq(t) can't follow closely the actual curve of the message signal m(t ). In contrast to slope-overload distortion, granular noise occurs when is too large relative to the local slope characteristics of m(t). granular noise is similar to quantization noise in PCM. •It seems that a lar ...
Mathematical Programming in Data Mining
... the simplest model to describe the essence of a phenomenon Binary classification problem: – discriminating between two given point sets A and B in the n-dimensional real space Rn by using as few of the ndimensions of the space as possible ...
... the simplest model to describe the essence of a phenomenon Binary classification problem: – discriminating between two given point sets A and B in the n-dimensional real space Rn by using as few of the ndimensions of the space as possible ...
CSCI6268L24
... Moral of the Story • The amount of cleverness we haven’t even thought of yet is scary – We’re probably never going to have completely secure computers and networks – The most we can hope for is “best effort” from those we trust and from ourselves – It’s going to be an eternal battle between us and ...
... Moral of the Story • The amount of cleverness we haven’t even thought of yet is scary – We’re probably never going to have completely secure computers and networks – The most we can hope for is “best effort” from those we trust and from ourselves – It’s going to be an eternal battle between us and ...
Lecture Notes
... about the operations you will perform on it about data structures you will use to represent it about how to structure all the parts of your program so as to achieve abstraction and encapsulation ...
... about the operations you will perform on it about data structures you will use to represent it about how to structure all the parts of your program so as to achieve abstraction and encapsulation ...
Programming “Safety” - The Software Enterprise at ASU
... What simple programming practices can we adopt at a low-level to improve the correctness and robustness of our source code? • One-half of this (or more) is in personal quality practices such as unit testing, code reviews, and coding standards • Other half is in the approach to coding itself (today’s ...
... What simple programming practices can we adopt at a low-level to improve the correctness and robustness of our source code? • One-half of this (or more) is in personal quality practices such as unit testing, code reviews, and coding standards • Other half is in the approach to coding itself (today’s ...
Physical layer
... 1. the action of conveying electrical or optical signals from 1 point to 1 or more other points in space 2. the process of sending information from 1 point to another things necessary for transmission systems path for signal transfer (medium) transform signal to appropriate from (code) launc ...
... 1. the action of conveying electrical or optical signals from 1 point to 1 or more other points in space 2. the process of sending information from 1 point to another things necessary for transmission systems path for signal transfer (medium) transform signal to appropriate from (code) launc ...
GSN06 - CSE
... The frequent sets or sequences represent the hot areas or roads which repeat many times in the moving object database and should be represented in a more efficient way. ...
... The frequent sets or sequences represent the hot areas or roads which repeat many times in the moving object database and should be represented in a more efficient way. ...
Slides
... about the operations you will perform on it about data structures you will use to represent it about how to structure all the parts of your program so as to achieve abstraction and encapsulation ...
... about the operations you will perform on it about data structures you will use to represent it about how to structure all the parts of your program so as to achieve abstraction and encapsulation ...
Principles of Program Design
... (rather than copied). Example: DAG tree representations. Objects subject to mutation cannot be used in contexts that depend on immutable values such as hash table keys. In multi-threaded programs, access to immutable data does not need not be synchronized ...
... (rather than copied). Example: DAG tree representations. Objects subject to mutation cannot be used in contexts that depend on immutable values such as hash table keys. In multi-threaded programs, access to immutable data does not need not be synchronized ...
Apr 20 - 24 Lesson Plan
... (C) articulate the concept of data representation Students will be able to design a software application plan Understand Swing Event listeners Use the JCheckbox, ButtonGroup, and JComboBox classes ...
... (C) articulate the concept of data representation Students will be able to design a software application plan Understand Swing Event listeners Use the JCheckbox, ButtonGroup, and JComboBox classes ...
Coding theory

Coding theory is the study of the properties of codes and their fitness for a specific application. Codes are used for data compression, cryptography, error-correction and more recently also for network coding. Codes are studied by various scientific disciplines—such as information theory, electrical engineering, mathematics, and computer science—for the purpose of designing efficient and reliable data transmission methods. This typically involves the removal of redundancy and the correction (or detection) of errors in the transmitted data.There are four types of coding: Data compression (or, source coding) Error correction (or channel coding) Cryptographic coding Line codingData compression and error correction may be studied in combination.Source encoding attempts to compress the data from a source in order to transmit it more efficiently. This practice is found every day on the Internet where the common Zip data compression is used to reduce the network load and make files smaller.The second, channel encoding, adds extra data bits to make the transmission of data more robust to disturbances present on the transmission channel. The ordinary user may not be aware of many applications using channel coding. A typical music CD uses the Reed-Solomon code to correct for scratches and dust. In this application the transmission channel is the CD itself. Cell phones also use coding techniques to correct for the fading and noise of high frequency radio transmission. Data modems, telephone transmissions, and NASA all employ channel coding techniques to get the bits through, for example the turbo code and LDPC codes.