Policy Template
... data including, but not limited to, mainframes, servers, personal computers, notebook computers, hand-held computers, personal digital assistant (PDA), pagers, distributed processing systems, network attached and computer controlled medical and laboratory equipment (i.e. embedded technology), ...
... data including, but not limited to, mainframes, servers, personal computers, notebook computers, hand-held computers, personal digital assistant (PDA), pagers, distributed processing systems, network attached and computer controlled medical and laboratory equipment (i.e. embedded technology), ...
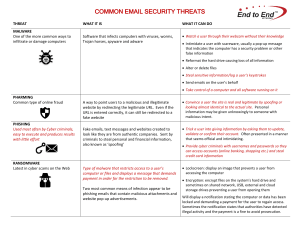
COMMON EMAIL SECURITY THREATS
... that indicates the computer has a security problem or other false information Reformat the hard drive causing loss of all information Alter or delete files Steal sensitive information/log a user’s keystrokes Send emails on the user’s behalf Take control of a computer and all software runni ...
... that indicates the computer has a security problem or other false information Reformat the hard drive causing loss of all information Alter or delete files Steal sensitive information/log a user’s keystrokes Send emails on the user’s behalf Take control of a computer and all software runni ...
C.2. Vulnerabilities
... Institute, has reported that universities often run systems with vulnerabilities and little monitoring or management. Consider that the typical university research or teaching lab is managed by a faculty member who has many other responsibilities or by a student manager who may have had little train ...
... Institute, has reported that universities often run systems with vulnerabilities and little monitoring or management. Consider that the typical university research or teaching lab is managed by a faculty member who has many other responsibilities or by a student manager who may have had little train ...
module 2 network security unit 1
... or suspend services of a host connected to the Internet. • A distributed denial-of-service (DDoS) attack occurs when multiple systems flood the bandwidth or resources of a targeted system, usually one or more web servers. ...
... or suspend services of a host connected to the Internet. • A distributed denial-of-service (DDoS) attack occurs when multiple systems flood the bandwidth or resources of a targeted system, usually one or more web servers. ...
Security Requirements
... “The tribunal in Fiji could not prove the integrity of an email message claimed to be originated from a government employee which stated that one of Fiji’s former Finance Minister ( Mr. Ah Koy) was one of the people behind the Fiji coup in 2000.” ...
... “The tribunal in Fiji could not prove the integrity of an email message claimed to be originated from a government employee which stated that one of Fiji’s former Finance Minister ( Mr. Ah Koy) was one of the people behind the Fiji coup in 2000.” ...
Taxonomy of Computer Security Incidents
... • Operating System, including version, patches, etc. • System Function (e.g., DNS/web server, workstation, etc.) • Antivirus software installed, including version, and latest updates • Location of the system(s) involved in the incident (e.g. Clemson) • Method used to identify the incident (e.g., IDS ...
... • Operating System, including version, patches, etc. • System Function (e.g., DNS/web server, workstation, etc.) • Antivirus software installed, including version, and latest updates • Location of the system(s) involved in the incident (e.g. Clemson) • Method used to identify the incident (e.g., IDS ...
Discovering Computers Fundamentals 4th Edition
... Identify ways to safeguard against computer viruses, worms, Trojan horses, botnets, denial of service attacks, back doors, and spoofing Discuss techniques to prevent unauthorized computer access and use Identify safeguards against hardware theft and vandalism Explain the ways to protect against soft ...
... Identify ways to safeguard against computer viruses, worms, Trojan horses, botnets, denial of service attacks, back doors, and spoofing Discuss techniques to prevent unauthorized computer access and use Identify safeguards against hardware theft and vandalism Explain the ways to protect against soft ...
Computer Security, Ethics, and Privacy
... Identify ways to safeguard against computer viruses, worms, Trojan horses, botnets, denial of service attacks, back doors, and spoofing Discuss techniques to prevent unauthorized computer access and use Identify safeguards against hardware theft and vandalism Explain the ways to protect against soft ...
... Identify ways to safeguard against computer viruses, worms, Trojan horses, botnets, denial of service attacks, back doors, and spoofing Discuss techniques to prevent unauthorized computer access and use Identify safeguards against hardware theft and vandalism Explain the ways to protect against soft ...
Computer Security-et..
... How can companies protect against hackers? Intrusion detection software analyzes network traffic, assesses system vulnerabilities, and identifies intrusions and suspicious behavior Access control defines who can access computer and what actions they can take ...
... How can companies protect against hackers? Intrusion detection software analyzes network traffic, assesses system vulnerabilities, and identifies intrusions and suspicious behavior Access control defines who can access computer and what actions they can take ...
Remote Access Policy
... for connecting to a company’s network from any host. These standards are designed to minimize the potential exposure to the company from damages which may result from unauthorized use of resources. Damages include the loss of sensitive or company confidential data, intellectual property, damage to p ...
... for connecting to a company’s network from any host. These standards are designed to minimize the potential exposure to the company from damages which may result from unauthorized use of resources. Damages include the loss of sensitive or company confidential data, intellectual property, damage to p ...
Hackers and Attackers
... • Script Kiddies – Wannabe hackers – Little knowledge of what they are doing – Exploits they use, have typically been written by others with more knowledge ...
... • Script Kiddies – Wannabe hackers – Little knowledge of what they are doing – Exploits they use, have typically been written by others with more knowledge ...
Document
... the question posed as well as stating the source document in which the answer is derived from. The research also presented a new approach in creating semantic Skolem Indexing matrix based on logical linguistic approach for automatically indexing multiple documents into single knowledge representatio ...
... the question posed as well as stating the source document in which the answer is derived from. The research also presented a new approach in creating semantic Skolem Indexing matrix based on logical linguistic approach for automatically indexing multiple documents into single knowledge representatio ...
The United States Secret Service - Federal Reserve Bank of San
... New York Electronic Crimes Task Force model, throughout the United States for the purpose of preventing, detecting, and investigating various forms of electronic crimes, including potential terrorist attacks against critical infrastructure and financial payment systems. ...
... New York Electronic Crimes Task Force model, throughout the United States for the purpose of preventing, detecting, and investigating various forms of electronic crimes, including potential terrorist attacks against critical infrastructure and financial payment systems. ...
Computer Security and Safety, Ethics, and Privacy
... of destroying data, stealing information, or other malicious actions. ◦ A script kiddie has the same intent as a cracker but does not have the technical skills and knowledge, using prewritten code to break into computers. ...
... of destroying data, stealing information, or other malicious actions. ◦ A script kiddie has the same intent as a cracker but does not have the technical skills and knowledge, using prewritten code to break into computers. ...
Port Scanning: Is it illegal
... ability to query remote computer ports to determine the service that is running and its compatibility with other computers, the Internet would cease to function. The county argued that port scanning for malicious purposes brings in the element of criminal intent. For example, many states have laws t ...
... ability to query remote computer ports to determine the service that is running and its compatibility with other computers, the Internet would cease to function. The county argued that port scanning for malicious purposes brings in the element of criminal intent. For example, many states have laws t ...
Document
... The IP address of your computer is : 213.177.129.120 your DNS address is : adsl-129-120.wanadoo.be We know you use : Microsoft Windows 98 Your navigator has the code: Mozilla/4.78 [en] (Win98; U) In fact it is: Netscape Communicator 4.x English ...
... The IP address of your computer is : 213.177.129.120 your DNS address is : adsl-129-120.wanadoo.be We know you use : Microsoft Windows 98 Your navigator has the code: Mozilla/4.78 [en] (Win98; U) In fact it is: Netscape Communicator 4.x English ...
Lect 1 - Intro
... These slides are not meant to be comprehensive lecture notes! They are only remarks and pointers. The material presented here is not sufficient for studying for the course. Your main sources for studying are the text and your own lecture notes ...
... These slides are not meant to be comprehensive lecture notes! They are only remarks and pointers. The material presented here is not sufficient for studying for the course. Your main sources for studying are the text and your own lecture notes ...
Computer Security: Principles and Practice, 1/e
... • 1 - The protection afforded to an automated information system in order to attain the applicable objectives of preserving the integrity, availability and confidentiality of information system resources (includes hardware, software, firmware, information/data, and telecommunications). • 3 - Passive ...
... • 1 - The protection afforded to an automated information system in order to attain the applicable objectives of preserving the integrity, availability and confidentiality of information system resources (includes hardware, software, firmware, information/data, and telecommunications). • 3 - Passive ...
Prevent Online Fraud and Identity Theft
... information from Identity Theft is crucial. There are many ways the unscrupulous can gain access to information such as your name, Social Security Number, credit card or bank account numbers, or other identifying information to commit fraud or other crimes. E-Mail Phishing - Involves you receiving a ...
... information from Identity Theft is crucial. There are many ways the unscrupulous can gain access to information such as your name, Social Security Number, credit card or bank account numbers, or other identifying information to commit fraud or other crimes. E-Mail Phishing - Involves you receiving a ...
Networking & Security
... possible is getting a map of IP addresses and the services each IP station is running). Open TCP ports can be spidered. Internet Control Message Protocol (ICMP) message types can be changed. Network can be flooded with junk. ...
... possible is getting a map of IP addresses and the services each IP station is running). Open TCP ports can be spidered. Internet Control Message Protocol (ICMP) message types can be changed. Network can be flooded with junk. ...
NetDay Cyber Security Kit for Schools
... copies of confidential student and staff data; in fact, local, state and federal laws require that these records be protected from unauthorized release. As districts begin to store confidential data electronically, these same laws apply – so electronic data security should be a top priority for admi ...
... copies of confidential student and staff data; in fact, local, state and federal laws require that these records be protected from unauthorized release. As districts begin to store confidential data electronically, these same laws apply – so electronic data security should be a top priority for admi ...