Understanding and Installing Firewalls
... Clifford Stoll's discovery of German spies tampering with his system. Bill Cheswick's "Evening with Berferd" 1992 in which he set up a simple electronic jail to observe an attacker. In 1988, an employee at the NASA Ames Research Center in California sent a memo by email to his colleagues [2] that re ...
... Clifford Stoll's discovery of German spies tampering with his system. Bill Cheswick's "Evening with Berferd" 1992 in which he set up a simple electronic jail to observe an attacker. In 1988, an employee at the NASA Ames Research Center in California sent a memo by email to his colleagues [2] that re ...
Security Risks - Bannerman High School
... • They can even pretend to be someone who wants to give you money, but first you have to give them your bank details.. Then they steal from you! ...
... • They can even pretend to be someone who wants to give you money, but first you have to give them your bank details.. Then they steal from you! ...
PowerPoint Presentation - Lead
... unauthorized users from accessing any part of your computer system. • Detection helps you to determine whether or not someone attempted to break into your system, if they were successful, and what they may have done. ...
... unauthorized users from accessing any part of your computer system. • Detection helps you to determine whether or not someone attempted to break into your system, if they were successful, and what they may have done. ...
Computer GEEK - Ideas
... could be a new out of the box computer or a previously used computer that has been re-loaded. The biggest challenge is bringing over all the data and settings from their old computer. There does not seem to be any one solution for this and for many applications, settings and data locations are not w ...
... could be a new out of the box computer or a previously used computer that has been re-loaded. The biggest challenge is bringing over all the data and settings from their old computer. There does not seem to be any one solution for this and for many applications, settings and data locations are not w ...
Document
... Virus - Vital Information Resources Under Siege A computer virus is a specific type of malicious computer code that replicates itself or inserts copies or new versions of itself in other programs. Worm Worms are parasitic computer programs that replicate, but unlike viruses, do not infect other ...
... Virus - Vital Information Resources Under Siege A computer virus is a specific type of malicious computer code that replicates itself or inserts copies or new versions of itself in other programs. Worm Worms are parasitic computer programs that replicate, but unlike viruses, do not infect other ...
here - Penndel Mental Health Center
... The Information Technology Department shall monitor Internet use from all computers and devices connected to the corporate network. For all traffic the monitoring system must record the source IP Address, the date, the time, the protocol, and the destination site or server. Where possible, the syste ...
... The Information Technology Department shall monitor Internet use from all computers and devices connected to the corporate network. For all traffic the monitoring system must record the source IP Address, the date, the time, the protocol, and the destination site or server. Where possible, the syste ...
網路犯罪案例 Cyber crime Case
... Network Packet Forensics Analysis Training The knowledge of network packet analysis is important for Forensic Investigators and Lawful Enforcement Agency (LEA) to carry out their daily duty. Network Packet Forensics Analysis Training (NPFAT) provides useful and sufficient knowledge required to anal ...
... Network Packet Forensics Analysis Training The knowledge of network packet analysis is important for Forensic Investigators and Lawful Enforcement Agency (LEA) to carry out their daily duty. Network Packet Forensics Analysis Training (NPFAT) provides useful and sufficient knowledge required to anal ...
Security Resume - Kirubha Shankar Murugesan
... Constructed a network topology with firewalls, switches, VLANS and routers with proper subnet masking and IP addressing for a small firm consisting of four departments. Experience with networking protocols such as BGP, OSPF, etc. Network Security Tools and Algorithms(Python): Jan 2016 - Apr 2016 ...
... Constructed a network topology with firewalls, switches, VLANS and routers with proper subnet masking and IP addressing for a small firm consisting of four departments. Experience with networking protocols such as BGP, OSPF, etc. Network Security Tools and Algorithms(Python): Jan 2016 - Apr 2016 ...
Computer Security Presentation
... The Gartner Group estimates that in the last year, 57 million U.S. adults received phishing e-mails, of which 11 million clicked on the provided links, and 1.78 million provided passwords and other sensitive personal information. In total, the scams resulted in fraud losses of $2.4 billion. [Gartner ...
... The Gartner Group estimates that in the last year, 57 million U.S. adults received phishing e-mails, of which 11 million clicked on the provided links, and 1.78 million provided passwords and other sensitive personal information. In total, the scams resulted in fraud losses of $2.4 billion. [Gartner ...
- Scholarly Commons
... Inheritance powder is the name that was given to poisons, especially arsenic, that were commonly used in the 17th and early 18th centuries to hasten the death of the elderly. For most of the 17th century, arsenic was deadly but undetectable, making it nearly impossible to prove that someone had been ...
... Inheritance powder is the name that was given to poisons, especially arsenic, that were commonly used in the 17th and early 18th centuries to hasten the death of the elderly. For most of the 17th century, arsenic was deadly but undetectable, making it nearly impossible to prove that someone had been ...
Chap013
... Cyber Theft – many computer crimes involve theft of money; many firms do not reveal that they’ve been victims due to bad publicity Cyber-terrorism – causing physical, real-world harm or severe disruption of infrastructure ...
... Cyber Theft – many computer crimes involve theft of money; many firms do not reveal that they’ve been victims due to bad publicity Cyber-terrorism – causing physical, real-world harm or severe disruption of infrastructure ...
File
... Many dial-up users believe that other types of protection will protect them.They are feel that no one can break their security in the computer. Some dial-up users have victims of major attacks and they lost their files and also a lots of work. ...
... Many dial-up users believe that other types of protection will protect them.They are feel that no one can break their security in the computer. Some dial-up users have victims of major attacks and they lost their files and also a lots of work. ...
IIDPS: An Internal Intrusion Detection and
... Over the past several years, the Internet environment has become more complex and untrusted. Enterprise networked systems are inevitably exposed to the increasing threats posed by hackers as well as malicious users internal to a network. IDS technology is one of the important tools used now-a-days, ...
... Over the past several years, the Internet environment has become more complex and untrusted. Enterprise networked systems are inevitably exposed to the increasing threats posed by hackers as well as malicious users internal to a network. IDS technology is one of the important tools used now-a-days, ...
Chapter 2: Attackers and Their Attacks
... Certain types of local area networks (LANs), such as Ethernet, must also have another address, called the media access control (MAC) address, to move information around the network Computers on a network keep a table that links an IP address with the corresponding address In ARP spoofing, a hack ...
... Certain types of local area networks (LANs), such as Ethernet, must also have another address, called the media access control (MAC) address, to move information around the network Computers on a network keep a table that links an IP address with the corresponding address In ARP spoofing, a hack ...
Uniqua Consulting Gmbh - Data Mining Analyst
... Job Posted by the Graduate Career Office of the University of Pretoria ...
... Job Posted by the Graduate Career Office of the University of Pretoria ...
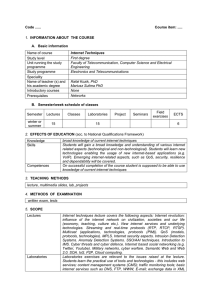
Internet Techniques
... IMS. Cyber threats and cyber defence. Internet based social networking (e.g. Twitter, Youtube). Military networks, cyber warfare. Semantic Web and Web 2.0. SOA. IoS. P2P. Cloud computing. Laboratories exercises are relevant to the issues raised at the lecture. Students learn the practical use of too ...
... IMS. Cyber threats and cyber defence. Internet based social networking (e.g. Twitter, Youtube). Military networks, cyber warfare. Semantic Web and Web 2.0. SOA. IoS. P2P. Cloud computing. Laboratories exercises are relevant to the issues raised at the lecture. Students learn the practical use of too ...
recr_presentation_oldest - Computer Science and Engineering
... – Uses advanced hardware and software design tools to achieve: • Better performance • Lower power requirements • Equipment that is less expensive to manufacture ...
... – Uses advanced hardware and software design tools to achieve: • Better performance • Lower power requirements • Equipment that is less expensive to manufacture ...
Slide 1 - IITK - Indian Institute of Technology Kanpur
... • Use Secure Portals and Payment Gateways :Banking transactions made on unsecured websites can lead to leaking of credit card details. These details can then be used to generate a card bearing the same data as the original credit card which can then be used fraudulently. It is imperative to use secu ...
... • Use Secure Portals and Payment Gateways :Banking transactions made on unsecured websites can lead to leaking of credit card details. These details can then be used to generate a card bearing the same data as the original credit card which can then be used fraudulently. It is imperative to use secu ...
View Report - PDF
... The Information Technology Department shall monitor Internet use from all computers and devices connected to the corporate network. For all traffic the monitoring system must record the source IP Address, the date, the time, the protocol, and the destination site or server. Where possible, the syste ...
... The Information Technology Department shall monitor Internet use from all computers and devices connected to the corporate network. For all traffic the monitoring system must record the source IP Address, the date, the time, the protocol, and the destination site or server. Where possible, the syste ...
The Role of Security in an Introductory Course
... • Depends • 2 or 4 year school • Course of study ...
... • Depends • 2 or 4 year school • Course of study ...
Chapter 1: Security Problems in Computing
... assessment, one asks what assets have value and should be protected. In some environments, such as banking there are many objects that have obvious value – big stacks of $100 bills, for example. As we saw in one of the stories above, there were also assets that had great value, although the value wa ...
... assessment, one asks what assets have value and should be protected. In some environments, such as banking there are many objects that have obvious value – big stacks of $100 bills, for example. As we saw in one of the stories above, there were also assets that had great value, although the value wa ...
Computer Components
... perform destructive activities. Spyware tracks a computer user’s Internet usage and send this data back to the company or person that create it. It is contained in other software. ...
... perform destructive activities. Spyware tracks a computer user’s Internet usage and send this data back to the company or person that create it. It is contained in other software. ...
Malicious Cryptography : Exposing Cryptovirology
... Foreword Terms such as cryptovirology, malware, kleptogram, or kleptography may be unfamiliar to the reader, but the basic concepts associated with them certainly are familiar. Everyone knows—often from sad experience—about viruses, Trojan horses, and worms and many have had a password “harvested” b ...
... Foreword Terms such as cryptovirology, malware, kleptogram, or kleptography may be unfamiliar to the reader, but the basic concepts associated with them certainly are familiar. Everyone knows—often from sad experience—about viruses, Trojan horses, and worms and many have had a password “harvested” b ...
Do you know someone may be watching you?
... Short for malicious software, consists of programming (code, scripts, active content, and other software) ...
... Short for malicious software, consists of programming (code, scripts, active content, and other software) ...