Chapter 19 Java Data Structures
... implementations of the List interface. Which of the two classes you use depends on your specific needs. If you need to support random access through an index without inserting or removing elements from any place other than the end, ArrayList offers the most efficient collection. ...
... implementations of the List interface. Which of the two classes you use depends on your specific needs. If you need to support random access through an index without inserting or removing elements from any place other than the end, ArrayList offers the most efficient collection. ...
Kernel Estimation and Model Combination in A Bandit Problem with
... Let {Xn , n ≥ 1} be a sequence of independent covariates generated from an underlying probability distribution PX supported in [0, 1]d . At each time n ≥ 1, we need to apply a sequential allocation rule η to decide which arm to pull based on Xn and the previous observations. We denote the chosen arm ...
... Let {Xn , n ≥ 1} be a sequence of independent covariates generated from an underlying probability distribution PX supported in [0, 1]d . At each time n ≥ 1, we need to apply a sequential allocation rule η to decide which arm to pull based on Xn and the previous observations. We denote the chosen arm ...
Best Keyword Cover Search
... In keyword-NNE algorithm, the best-first browsing strategy is applied like BF-baseline but large memory requirement is avoided. For the better explanation, we can imagine all candidate keyword covers generated in BF-baseline algorithm are grouped into independent groups. Each group is associated wit ...
... In keyword-NNE algorithm, the best-first browsing strategy is applied like BF-baseline but large memory requirement is avoided. For the better explanation, we can imagine all candidate keyword covers generated in BF-baseline algorithm are grouped into independent groups. Each group is associated wit ...
26 Optimal Bounds for Johnson-Lindenstrauss
... Johnson and Lindenstrauss, it has been shown [Achlioptas 2003; Arriaga and Vempala 1999; Dasgupta and Gupta 2003; Indyk and Motwani 1998] that the projection matrix could be constructed element-wise using the standard Gaussian distribution or even uniform ±1 variables [Achlioptas 2003]. By setting t ...
... Johnson and Lindenstrauss, it has been shown [Achlioptas 2003; Arriaga and Vempala 1999; Dasgupta and Gupta 2003; Indyk and Motwani 1998] that the projection matrix could be constructed element-wise using the standard Gaussian distribution or even uniform ±1 variables [Achlioptas 2003]. By setting t ...
Enhanced form of solving real coded numerical optimization
... value is calculated for both the algorithms with each 4 benchmark function. In the tables the bold readings are improved result over the ABC with linear crossover. Obtained results indicated in tables that ABC with crossover provides better results than original ABC algorithm. Here we also observed ...
... value is calculated for both the algorithms with each 4 benchmark function. In the tables the bold readings are improved result over the ABC with linear crossover. Obtained results indicated in tables that ABC with crossover provides better results than original ABC algorithm. Here we also observed ...
Longest Common Substring with Approximately k Mismatches
... In this section we give an overview of the main ideas needed to prove Theorem 1. The classic solution to the longest common substring problem is based on two observations. The first observation is that the longest common substring of T1 and T2 is in fact the longest common prefix of some suffix of T ...
... In this section we give an overview of the main ideas needed to prove Theorem 1. The classic solution to the longest common substring problem is based on two observations. The first observation is that the longest common substring of T1 and T2 is in fact the longest common prefix of some suffix of T ...
Shortest Paths in Directed Planar Graphs with Negative Lengths: a
... size Ω(n log n) for an n-node graph. The first phase of their algorithm computes this structure in O(n log3 n) time. The second phase uses the structure to compute distances from a node to all other nodes, also in O(n log3 n) time. The structure of our algorithm is different—it is a simple divide-an ...
... size Ω(n log n) for an n-node graph. The first phase of their algorithm computes this structure in O(n log3 n) time. The second phase uses the structure to compute distances from a node to all other nodes, also in O(n log3 n) time. The structure of our algorithm is different—it is a simple divide-an ...
4 per page - esslli 2016
... EXPTIME-membership We start with an EXPTIME upper bound for concept satisfiability in ALC relative to TBoxes. ...
... EXPTIME-membership We start with an EXPTIME upper bound for concept satisfiability in ALC relative to TBoxes. ...
1 managing long linked lists using lock free techniques
... These three pointers are obtained by traversing the linked list. Each node in the linked list consists of four fields; a data field, two pointer fields, and a count field. One of the pointers (PTR) is used to maintain an upto-date linked list. These pointers never point to a node that has been delet ...
... These three pointers are obtained by traversing the linked list. Each node in the linked list consists of four fields; a data field, two pointer fields, and a count field. One of the pointers (PTR) is used to maintain an upto-date linked list. These pointers never point to a node that has been delet ...
Cost-effective Outbreak Detection in Networks Jure Leskovec Andreas Krause Carlos Guestrin
... that, perhaps counterintuitively, a more cost-effective solution can be obtained, by reading smaller, but higher quality, blogs, which our algorithm can find. There are several possible criteria one may want to optimize in outbreak detection. For example, one criterion seeks to minimize detection time ...
... that, perhaps counterintuitively, a more cost-effective solution can be obtained, by reading smaller, but higher quality, blogs, which our algorithm can find. There are several possible criteria one may want to optimize in outbreak detection. For example, one criterion seeks to minimize detection time ...
W. Dean. Algorithms and the mathematical foundations of computer
... can be justified by a supplemental mathematical proof that the algorithm is correct (i.e. that it computes the function that it is claimed to). I will refer to the view expressed by (A) as algorithmic realism.3 Although it is often not identified as a thesis requiring an explicit statement and defen ...
... can be justified by a supplemental mathematical proof that the algorithm is correct (i.e. that it computes the function that it is claimed to). I will refer to the view expressed by (A) as algorithmic realism.3 Although it is often not identified as a thesis requiring an explicit statement and defen ...
Performance and Scalability of Parallel Systems
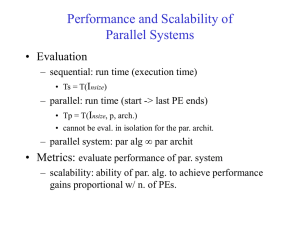
... • Determines the easy with which a parallel system can maintain a constant efficiency and thus, achieve speedups increasing in proportion to the number of processors • A small isoefficiency function means that small increments in the problem size are sufficient for the efficient utilization of an in ...
... • Determines the easy with which a parallel system can maintain a constant efficiency and thus, achieve speedups increasing in proportion to the number of processors • A small isoefficiency function means that small increments in the problem size are sufficient for the efficient utilization of an in ...
A Nonlinear Programming Algorithm for Solving Semidefinite
... advantage over (1), but this benefit has a corresponding cost: the objective function and constraints are no longer linear—but instead quadratic and in general nonconvex. Is it practical to optimize (2) in place of (1)? The answer is certainly not an immediate “yes” as there are several important qu ...
... advantage over (1), but this benefit has a corresponding cost: the objective function and constraints are no longer linear—but instead quadratic and in general nonconvex. Is it practical to optimize (2) in place of (1)? The answer is certainly not an immediate “yes” as there are several important qu ...
Constant-Time LCA Retrieval
... We can instead apply Procedure I to each of these loglogn subset which would total the space and time complexity of the whole algorithm to O( nloglogn ). If we choose to further partition these subset into subsets of size logloglogn, we would reach O(nlogloglogn). We can continue in this fashion for ...
... We can instead apply Procedure I to each of these loglogn subset which would total the space and time complexity of the whole algorithm to O( nloglogn ). If we choose to further partition these subset into subsets of size logloglogn, we would reach O(nlogloglogn). We can continue in this fashion for ...
3. Keyword Cover Search Module
... In keyword-NNE algorithm, the best-first browsing strategy is applied like BF-baseline but large memory requirement is avoided. For the better explanation, we can imagine all candidate keyword covers generated in BF-baseline algorithm are grouped into independent groups. Each group is associated wi ...
... In keyword-NNE algorithm, the best-first browsing strategy is applied like BF-baseline but large memory requirement is avoided. For the better explanation, we can imagine all candidate keyword covers generated in BF-baseline algorithm are grouped into independent groups. Each group is associated wi ...
Evolving Neural Networks using Ant Colony Optimization with
... at work without heuristic bias ACO leads in very poor results”. The use of heuristic information is very important for ACO and has a great impact to the overall performance of the algorithm. For example, at the initial stage of training an ANN, the pheromone trails in all tables assigned to each con ...
... at work without heuristic bias ACO leads in very poor results”. The use of heuristic information is very important for ACO and has a great impact to the overall performance of the algorithm. For example, at the initial stage of training an ANN, the pheromone trails in all tables assigned to each con ...
A New Non-oscillatory Numerical Approach for Structural Dynamics
... smoothed particle hydrodynamics (SPH) method and others. Many different numerical methods have been developed for the time integration of Eq. (1). However, for wave propagation problems, the integration of Eq. (1) leads to the appearance of spurious high-frequency oscillations. Both the spatial disc ...
... smoothed particle hydrodynamics (SPH) method and others. Many different numerical methods have been developed for the time integration of Eq. (1). However, for wave propagation problems, the integration of Eq. (1) leads to the appearance of spurious high-frequency oscillations. Both the spatial disc ...
On the Use of Non-Stationary Strategies for Solving Two
... their theoretical guarantees to the case of γdiscounted zero-sum Markov Games (MGs). As in the case of Markov Decision Processes (MDPs), non-stationary algorithms are shown to exhibit better performance bounds compared to their stationary counterparts. The obtained bounds are generically composed of ...
... their theoretical guarantees to the case of γdiscounted zero-sum Markov Games (MGs). As in the case of Markov Decision Processes (MDPs), non-stationary algorithms are shown to exhibit better performance bounds compared to their stationary counterparts. The obtained bounds are generically composed of ...
Algorithm GENITOR
... signals that reach the next Si stations. Note that Si is a r.v. dependent on power and availability of retransmitter amplifiers. The aim of the system is to provide propagation of a signal from transmitter to receiver. The LMCCS was first introduced by Hwang & Yao [1] as a generalization of linear ...
... signals that reach the next Si stations. Note that Si is a r.v. dependent on power and availability of retransmitter amplifiers. The aim of the system is to provide propagation of a signal from transmitter to receiver. The LMCCS was first introduced by Hwang & Yao [1] as a generalization of linear ...
High Dimensional Similarity Joins: Algorithms and Performance
... Multidimensional divide and conquer creates 2d partitions of the space and thus needs 2d output bu ers during the partitioning phase. In summary, we expect that such an approach might be suitable for low dimensionalities and data sets with similar statistical characteristics, but it is not promisin ...
... Multidimensional divide and conquer creates 2d partitions of the space and thus needs 2d output bu ers during the partitioning phase. In summary, we expect that such an approach might be suitable for low dimensionalities and data sets with similar statistical characteristics, but it is not promisin ...
Efficient Adaptation Text Design Based On The Kullback
... applications such as designing speaker adaptation text for ASR and speech synthesis. In speaker adaptation, the adaptation text is used to modify the speaker independent model to a specific user. Obviously, the less sentences the talker has to read the better. In some cases, unit (phoneme or subword ...
... applications such as designing speaker adaptation text for ASR and speech synthesis. In speaker adaptation, the adaptation text is used to modify the speaker independent model to a specific user. Obviously, the less sentences the talker has to read the better. In some cases, unit (phoneme or subword ...
Paper - George Karypis
... hand corner of the matrix will be idle for more time as the size of the matrix increases. But, the two dimensional cyclic mapping solves this problem by localizing the pipeline to a xed portion of the matrix independent of the size of the matrix. This is a very desirable property for achieving sca ...
... hand corner of the matrix will be idle for more time as the size of the matrix increases. But, the two dimensional cyclic mapping solves this problem by localizing the pipeline to a xed portion of the matrix independent of the size of the matrix. This is a very desirable property for achieving sca ...
A Simulation Approach to Optimal Stopping Under Partial Information
... programming computations are possible, see e.g. [38]. If the problem state is low-dimensional and Markov, one may alternatively use the quasi-variational formulation to obtain a free-boundary partial differential equation (pde) and then implement a (b) numerical pde solver for an efficient solution. ...
... programming computations are possible, see e.g. [38]. If the problem state is low-dimensional and Markov, one may alternatively use the quasi-variational formulation to obtain a free-boundary partial differential equation (pde) and then implement a (b) numerical pde solver for an efficient solution. ...
Rivest-Shamir
... • An algorithm whose time complexity is bounded by a polynomial is called a polynomial-time algorithm. – An algorithm is considered to be efficient if it runs in polynomial time. CS 450/650 Lecture 8: Algorithm Background ...
... • An algorithm whose time complexity is bounded by a polynomial is called a polynomial-time algorithm. – An algorithm is considered to be efficient if it runs in polynomial time. CS 450/650 Lecture 8: Algorithm Background ...