Software Engineering Syllabus
... Batch processing – the execution of jobs by collecting them in a single _____, then executing them _______ further _________ with the user ...
... Batch processing – the execution of jobs by collecting them in a single _____, then executing them _______ further _________ with the user ...
Software Engineering Syllabus
... Batch processing – the execution of jobs by collecting them in a single _____, then executing them _______ further _________ with the user ...
... Batch processing – the execution of jobs by collecting them in a single _____, then executing them _______ further _________ with the user ...
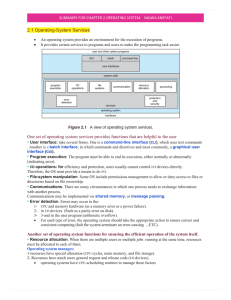
Summary for chapter 2 OPERATING SYSTEM nAJWA kNEFATI
... perhaps to reset them. File attributes include the file name, file type, protection codes, accounting information, and so on. At least two system calls, get file attributes () and set file attributes (), are required for this function. Some operating systems provide move () and copy (). 2.4.3 De ...
... perhaps to reset them. File attributes include the file name, file type, protection codes, accounting information, and so on. At least two system calls, get file attributes () and set file attributes (), are required for this function. Some operating systems provide move () and copy (). 2.4.3 De ...
Lecture Notes - UCLA Computer Science
... Timesharing (multitasking) is logical extension in which CPU switches jobs so frequently that users can interact with each job while it is running, creating interactive computing z ...
... Timesharing (multitasking) is logical extension in which CPU switches jobs so frequently that users can interact with each job while it is running, creating interactive computing z ...
Interrupts - Matthew L. Wright
... drives and other block-oriented devices. – Commands include read(), write(), and seek() – Applications don’t have to deal with the low-level operation of the devices. – OS may let application access device directly, without buffering or locking—this is raw I/O or direct I/O. • Character-stream inter ...
... drives and other block-oriented devices. – Commands include read(), write(), and seek() – Applications don’t have to deal with the low-level operation of the devices. – OS may let application access device directly, without buffering or locking—this is raw I/O or direct I/O. • Character-stream inter ...
Operating System
... Further more, actual system calls can ofter be more detailed and difficult to work with than the API available to an application programmer. NOTE: There often exists a strong correlation between a function in the API and its associated system call within the kernel. In fact, many of the POSIX and Wi ...
... Further more, actual system calls can ofter be more detailed and difficult to work with than the API available to an application programmer. NOTE: There often exists a strong correlation between a function in the API and its associated system call within the kernel. In fact, many of the POSIX and Wi ...
OS and Computer Architecture
... allocate memory space for processes, deallocate memory space, maintain the mappings from virtual to physical memory (page tables), decide how much memory to allocate to each process, and when a process should be removed from memory (policies). ...
... allocate memory space for processes, deallocate memory space, maintain the mappings from virtual to physical memory (page tables), decide how much memory to allocate to each process, and when a process should be removed from memory (policies). ...
Introduction - USC Upstate: Faculty
... that is, a library such as the C library (libc), • provide an interface that allows applications to use a predefined series of APIs that define the functions for communicating with the kernel. • Examples of system calls: – performing file I/O (open, close, read, write) – running application programs ...
... that is, a library such as the C library (libc), • provide an interface that allows applications to use a predefined series of APIs that define the functions for communicating with the kernel. • Examples of system calls: – performing file I/O (open, close, read, write) – running application programs ...
UNIX-like Operating Systems
... user had sole use of the machine, program was loaded into the machine and the machine set to work, task is responsible for everything, task totaly determines behavior of computer. machines came with libraries of support code which were linked to the user’s program to assist in operations such as inp ...
... user had sole use of the machine, program was loaded into the machine and the machine set to work, task is responsible for everything, task totaly determines behavior of computer. machines came with libraries of support code which were linked to the user’s program to assist in operations such as inp ...
CPS120: Introduction to Computer Science
... • The operating system is the piece of software that controls the computer and its resources. An operating system keeps track of users, filenames and their location, and manages the computer's memory. • Other operating system functions include the allocation and monitoring of all devices and schedul ...
... • The operating system is the piece of software that controls the computer and its resources. An operating system keeps track of users, filenames and their location, and manages the computer's memory. • Other operating system functions include the allocation and monitoring of all devices and schedul ...
operating systems structures
... I/O Operations: A running program may require I/O, which may involve a file or an I/O device. For efficiency and protection user usually cannot control I/O devices directly. The OS provides a means to do I/O. ƒ File System Manipulation: Programs need to read, write files. Also they should be able to ...
... I/O Operations: A running program may require I/O, which may involve a file or an I/O device. For efficiency and protection user usually cannot control I/O devices directly. The OS provides a means to do I/O. ƒ File System Manipulation: Programs need to read, write files. Also they should be able to ...
Lecture 1 - Concepts of the UNIX Operating System
... 1. Many UNIX commands (called filters) possess an unusual property in that the output of one command can be connected to the input of another. In this way, pipelines of two or more commands can be set up to handle complex text manipulation tasks. You can’t have a pipeline of interactive commands. 2. ...
... 1. Many UNIX commands (called filters) possess an unusual property in that the output of one command can be connected to the input of another. In this way, pipelines of two or more commands can be set up to handle complex text manipulation tasks. You can’t have a pipeline of interactive commands. 2. ...
MS Word file - Maricopa Community Colleges
... 5. The component at the lowest software level in the __________________ driver. 6. ____________________________ define the rules of communication between two computers and include TCP/IP and NWLINK. 7. The DOS command to display all the TCP/IP properties is ___________________________8. In the user ...
... 5. The component at the lowest software level in the __________________ driver. 6. ____________________________ define the rules of communication between two computers and include TCP/IP and NWLINK. 7. The DOS command to display all the TCP/IP properties is ___________________________8. In the user ...
Lesson 8
... The Linux partition used to install the Linux system on is called the root partition. The root partition ( indicated by a single slash, /) contains the main file system and user subdirectories. To access files on another file system, say a CD-ROM, you need to attach that file system to your main sys ...
... The Linux partition used to install the Linux system on is called the root partition. The root partition ( indicated by a single slash, /) contains the main file system and user subdirectories. To access files on another file system, say a CD-ROM, you need to attach that file system to your main sys ...
Chapter One
... Describe the options for connecting to a UNIX system Define the syntax used for entering UNIX commands ...
... Describe the options for connecting to a UNIX system Define the syntax used for entering UNIX commands ...
What is the Linux Kernel?
... PID,Program name Parent, youngest child, next sibling, previous sibling Process Times (start_time, utime, stime, cutime, cstime) Scheduling algorithm, priority, nice value, errno ...
... PID,Program name Parent, youngest child, next sibling, previous sibling Process Times (start_time, utime, stime, cutime, cstime) Scheduling algorithm, priority, nice value, errno ...
OS Basics
... Any Input /Output (I/O) devices present in the computer, such as keyboard, mouse, disk drives, USB devices, printers, displays, network adapters, etc. The kernel allocates requests from applications to perform I/O to an appropriate device (or subsection of a device, in the case of files on a disk ...
... Any Input /Output (I/O) devices present in the computer, such as keyboard, mouse, disk drives, USB devices, printers, displays, network adapters, etc. The kernel allocates requests from applications to perform I/O to an appropriate device (or subsection of a device, in the case of files on a disk ...
operating system
... programs (location in memory, stack pointer, program counter). When a program is run, the operating system converts it into a process. It is the process, rather than the simple program, that the processor executes. ...
... programs (location in memory, stack pointer, program counter). When a program is run, the operating system converts it into a process. It is the process, rather than the simple program, that the processor executes. ...
Exceptional Control Flow - Computer Systems: A Programmer`s
... where each ak is the address of some corresponding instruction Ik . Each transition from ak to ak+1 is called a control transfer. A sequence of such control transfers is called the flow of control, or control flow of the processor. The simplest kind of control flow is a “smooth” sequence where each ...
... where each ak is the address of some corresponding instruction Ik . Each transition from ak to ak+1 is called a control transfer. A sequence of such control transfers is called the flow of control, or control flow of the processor. The simplest kind of control flow is a “smooth” sequence where each ...
Role of OS
... • Silberschatz and Gavin: “An OS is similar to a government” • Coordinator and Traffic Cop: – Manages all resources – Settles conflicting requests for resources – Prevent errors and improper use of the computer ...
... • Silberschatz and Gavin: “An OS is similar to a government” • Coordinator and Traffic Cop: – Manages all resources – Settles conflicting requests for resources – Prevent errors and improper use of the computer ...
PPT
... CPU uses special instructions or writes to special memory addresses (memory mapped I/O) to initiate the I/O request Device will perform the request while the CPU does other work When the request is complete, the device will send an interrupt signal to the CPU via a shared bus Interrupt causes contro ...
... CPU uses special instructions or writes to special memory addresses (memory mapped I/O) to initiate the I/O request Device will perform the request while the CPU does other work When the request is complete, the device will send an interrupt signal to the CPU via a shared bus Interrupt causes contro ...
Operating System Concepts, Terminology, and History
... • Early operating systems provided poor support for these three features. – Running multiple programs, while possible, was done via a cooperative system which depended on each application program to release the CPU periodically to allow its peer processes to run. – Protection of system storage was l ...
... • Early operating systems provided poor support for these three features. – Running multiple programs, while possible, was done via a cooperative system which depended on each application program to release the CPU periodically to allow its peer processes to run. – Protection of system storage was l ...
Import Settings:
... 28. Describe how Mac OS X is considered a hybrid system. 29. Describe how Android uses a unique virtual machine for running Java programs. True/False 30. KDE and GNOME desktops are available under open-source licenses. 31. Many operating system merge I/O devices and files into a combined file becaus ...
... 28. Describe how Mac OS X is considered a hybrid system. 29. Describe how Android uses a unique virtual machine for running Java programs. True/False 30. KDE and GNOME desktops are available under open-source licenses. 31. Many operating system merge I/O devices and files into a combined file becaus ...
Slides - Dr. Choong
... Program vs. Process Program : a set of data and code that manipulate it Process : a program in execution States of a Process Running, Waiting, Ready, etc. Process “Tree” ...
... Program vs. Process Program : a set of data and code that manipulate it Process : a program in execution States of a Process Running, Waiting, Ready, etc. Process “Tree” ...
Windows File System
... • Windows offers two modes of I/O operation: – asynchronous and synchronous. ...
... • Windows offers two modes of I/O operation: – asynchronous and synchronous. ...