Ch – 1 Introduction
... • The authentication service is concerned with assuring that a communication is authentic. • In the case of a single/ incoming message, such as a warning or alarm signal, the function of the authentication service is to assure the recipient that the message is from the source that it claims to be fr ...
... • The authentication service is concerned with assuring that a communication is authentic. • In the case of a single/ incoming message, such as a warning or alarm signal, the function of the authentication service is to assure the recipient that the message is from the source that it claims to be fr ...
How Organizations Are Using Fortscale`s User Behavior Analytics
... A unique aspect of Fortscale is the ability to provide rich context for the analyst by automatically labeling users and machines based on many observed behaviors, helping analysts to quickly prioritize events for investigation. One account label applied is “service” which indicates an account whose ...
... A unique aspect of Fortscale is the ability to provide rich context for the analyst by automatically labeling users and machines based on many observed behaviors, helping analysts to quickly prioritize events for investigation. One account label applied is “service” which indicates an account whose ...
NET 536Network Security
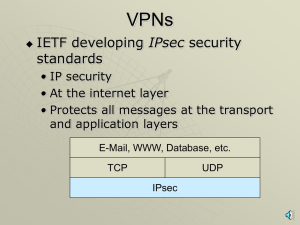
... IPSec protects the message passed down to IP from the transport layer. The message is processed by AH and /or ESP and the appropriate headers are added. IPSec in the transport mode does not protect the IP header; it only protects the information coming from the transport layer. The transport mode is ...
... IPSec protects the message passed down to IP from the transport layer. The message is processed by AH and /or ESP and the appropriate headers are added. IPSec in the transport mode does not protect the IP header; it only protects the information coming from the transport layer. The transport mode is ...
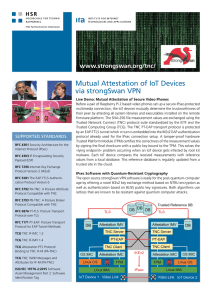
Mutual Attestation of IoT Devices via strongSwan VPN
... Before a pair of Raspberry Pi 2 based video phones set up a secure IPsec-protected multimedia connection, the IoT devices mutually determine the trustworthiness of their peer by attesting all system libraries and executables installed on the remote firmware platform. The SHA-256 file measurement val ...
... Before a pair of Raspberry Pi 2 based video phones set up a secure IPsec-protected multimedia connection, the IoT devices mutually determine the trustworthiness of their peer by attesting all system libraries and executables installed on the remote firmware platform. The SHA-256 file measurement val ...
UH_Quick User Guide
... The information about the currently connected WiMAX network such as device, receiving signal strength and quality, transmit power and Modulation Code Scheme for UL and DL will be shown in the Link Status. Link Satistics gives you a summary of the information transmit and receive packets as well as t ...
... The information about the currently connected WiMAX network such as device, receiving signal strength and quality, transmit power and Modulation Code Scheme for UL and DL will be shown in the Link Status. Link Satistics gives you a summary of the information transmit and receive packets as well as t ...
CIT 016 Review for Final
... difficult to understand, troubleshoot, and feel secure about The challenge is to make the system simple from the inside but complex from the outside ...
... difficult to understand, troubleshoot, and feel secure about The challenge is to make the system simple from the inside but complex from the outside ...
VPNs, PKIs, ISSs, SSLs with narration
... • Webserver authenticates itself • Browser may authenticate itself but rarely does • Browser selects a symmetric session key, sends to webserver • Adds a digital signature and encrypts all messages with the symmetric key ...
... • Webserver authenticates itself • Browser may authenticate itself but rarely does • Browser selects a symmetric session key, sends to webserver • Adds a digital signature and encrypts all messages with the symmetric key ...
Handout
... r Two or more transmitting nodes -> “collision”, r Random access MAC protocol specifies: m How to detect collisions m How to recover from collisions (e.g., via delayed retransmissions) r Examples of random access MAC protocols: m Slotted ALOHA and ALOHA m CSMA and CSMA/CD ...
... r Two or more transmitting nodes -> “collision”, r Random access MAC protocol specifies: m How to detect collisions m How to recover from collisions (e.g., via delayed retransmissions) r Examples of random access MAC protocols: m Slotted ALOHA and ALOHA m CSMA and CSMA/CD ...
Coop-ICNP - Columbia University
... R-MN builds a list of {Subnet ID, IP address} pairs, one per each possible subnet it might move to next. ...
... R-MN builds a list of {Subnet ID, IP address} pairs, one per each possible subnet it might move to next. ...
Logical attack advisory for U.S. and Canada
... Other Dispenser Security Authentication levels WILL NOT protect against Black Box attacks. The only protection against Black Box attacks is a combination of Level 3 Authentication AND USB dispenser component from APTRA XFS 06.03. For Personas ATMs: Fleet modernization is an important part of sta ...
... Other Dispenser Security Authentication levels WILL NOT protect against Black Box attacks. The only protection against Black Box attacks is a combination of Level 3 Authentication AND USB dispenser component from APTRA XFS 06.03. For Personas ATMs: Fleet modernization is an important part of sta ...
802 21-IEEE-Security_Tutorial
... • Handover techniques that assume concurrent radio usage cannot be used • Even for dual-radio devices it might make sense to reduce the security-related signaling, as it decreases the time that both radios need to be active and thus can increase battery life • In addition, handovers between networks ...
... • Handover techniques that assume concurrent radio usage cannot be used • Even for dual-radio devices it might make sense to reduce the security-related signaling, as it decreases the time that both radios need to be active and thus can increase battery life • In addition, handovers between networks ...
Cryptanalysis of Stream Cipher
... 128-bit state information The overall differential probability of the forgery attack against AEGIS increases But the differential probability that a difference propagates through 5 AES rounds is not affected ...
... 128-bit state information The overall differential probability of the forgery attack against AEGIS increases But the differential probability that a difference propagates through 5 AES rounds is not affected ...
Distributed System Concepts and Architectures
... system wide basis E.g. multilevel security, all subjects and objects in the system are assigned a sensitivity label. The labels are used as the basis for mandatory access control decisions. ...
... system wide basis E.g. multilevel security, all subjects and objects in the system are assigned a sensitivity label. The labels are used as the basis for mandatory access control decisions. ...
About the Presentations
... File has restricted access Passwords are stored only after being encrypted with the salt value and an encoding algorithm ...
... File has restricted access Passwords are stored only after being encrypted with the salt value and an encoding algorithm ...
CISSP CBK #2 Access Control
... • Security labels can be defined the organization. • They also have categories to support “need to know” @ a certain level. • Categories can be defined by the organization • If I have “top secret” clearance can I see all projects in the “secret ...
... • Security labels can be defined the organization. • They also have categories to support “need to know” @ a certain level. • Categories can be defined by the organization • If I have “top secret” clearance can I see all projects in the “secret ...
computer security - GH Raisoni Polytechnic, Nagpur
... an Authentication Server or even a Public Key Infrastructure. Authorization is the process of giving someone permission to do or have something. In multi-user computer systems, a system administrator defines for the system which users are allowed access to the system and what privileges of use (su ...
... an Authentication Server or even a Public Key Infrastructure. Authorization is the process of giving someone permission to do or have something. In multi-user computer systems, a system administrator defines for the system which users are allowed access to the system and what privileges of use (su ...
CHAPTER 1 INTRODUCTION 1.1. Introduction
... In recent years, individual have been attracted to wireless-based communication since wireless supports mobility during information exchanged while changing networks at higher speed. Nowadays, technologies in wireless communications provide users many alternatives to be connected to the Internet, su ...
... In recent years, individual have been attracted to wireless-based communication since wireless supports mobility during information exchanged while changing networks at higher speed. Nowadays, technologies in wireless communications provide users many alternatives to be connected to the Internet, su ...
Chapter. 01
... For some Computer Security is controlling access to hardware, software and data of a computerized system. A large measure of computer security is simply keeping the computer system's information secure. In broader terms, computer security can be thought of as the protection of the computer and its r ...
... For some Computer Security is controlling access to hardware, software and data of a computerized system. A large measure of computer security is simply keeping the computer system's information secure. In broader terms, computer security can be thought of as the protection of the computer and its r ...
Pathways and the Pioneering Spirit
... Deploying a WLAN posed several potential problems. For instance, there was the threat of students getting into the teachers' resource base or accessing unwanted websites. Security issues, including protection from viruses and worms, have been taken care of by adopting several measures. The school ma ...
... Deploying a WLAN posed several potential problems. For instance, there was the threat of students getting into the teachers' resource base or accessing unwanted websites. Security issues, including protection from viruses and worms, have been taken care of by adopting several measures. The school ma ...
Security Issues in Mobile Communication Systems
... infrastructure is required for charging anyway • Are these problems serious enough? • trust assumption may not change so drastically • providing true privacy is hard: hiding identity information is irrelevant as long as some other linkable information is associated with the messages • try not to pre ...
... infrastructure is required for charging anyway • Are these problems serious enough? • trust assumption may not change so drastically • providing true privacy is hard: hiding identity information is irrelevant as long as some other linkable information is associated with the messages • try not to pre ...
ISEC0511
... validate the identity of the parties. In nonrepudiation we identify the identity of these parties beyond any doubt. Digital signatures can achieve nonrepudiation. One-factor authentication, Two-factor authentication, Multi-factor authentication. ...
... validate the identity of the parties. In nonrepudiation we identify the identity of these parties beyond any doubt. Digital signatures can achieve nonrepudiation. One-factor authentication, Two-factor authentication, Multi-factor authentication. ...
Sun Microsystems
... Microsystems, Inc. to its position as a leading provider of industrial-strength hardware, software and services that make the Net work. Sun can be found in more than 100 countries and on the World Wide Web at http://sun.com. BUSINESS CHALLENGE The virtual enterprise is quickly becoming a reality as ...
... Microsystems, Inc. to its position as a leading provider of industrial-strength hardware, software and services that make the Net work. Sun can be found in more than 100 countries and on the World Wide Web at http://sun.com. BUSINESS CHALLENGE The virtual enterprise is quickly becoming a reality as ...
Confidentiality
... The five main phases of an information security plan are as follows; 2.1 Inspection - The most important tasks in developing an Information Security Plan are identifying the key corporate functions, the capabilities they need, when they need those capabilities, and how they interact with other funct ...
... The five main phases of an information security plan are as follows; 2.1 Inspection - The most important tasks in developing an Information Security Plan are identifying the key corporate functions, the capabilities they need, when they need those capabilities, and how they interact with other funct ...
Authentication
.png?width=300)
Authentication (from Greek: αὐθεντικός authentikos, ""real, genuine,"" from αὐθέντης authentes, ""author"") is the act of confirming the truth of an attribute of a single piece of data (a datum) claimed true by an entity. In contrast with identification which refers to the act of stating or otherwise indicating a claim purportedly attesting to a person or thing's identity, authentication is the process of actually confirming that identity. It might involve confirming the identity of a person by validating their identity documents, verifying the validity of a Website with a digital certificate, tracing the age of an artifact by carbon dating, or ensuring that a product is what its packaging and labeling claim to be. In other words, authentication often involves verifying the validity of at least one form of identification.