An efficient local Algorithm for Distributed Multivariate Regression in
... the MR model no longer represents it, the feedback loop inmachine learning tool that is widely used for prediction, clasdicates this and the model is rebuilt. Moreover, we also show sification, and data compression. Multivariate regression is that all the data need not be centralized to recompute th ...
... the MR model no longer represents it, the feedback loop inmachine learning tool that is widely used for prediction, clasdicates this and the model is rebuilt. Moreover, we also show sification, and data compression. Multivariate regression is that all the data need not be centralized to recompute th ...
21-p2p
... – Search scope small (only nodes along search path involved); no flooding – Anonymity properties may give you “plausible ...
... – Search scope small (only nodes along search path involved); no flooding – Anonymity properties may give you “plausible ...
Advanced Operating Systems
... layer of library functions. Application designers often overlook available facilities and resources because they mistakenly limit themselves to the features provided by a particular programming language. Even if only those language-provided facilities are used, understanding the system services thei ...
... layer of library functions. Application designers often overlook available facilities and resources because they mistakenly limit themselves to the features provided by a particular programming language. Even if only those language-provided facilities are used, understanding the system services thei ...
Towards a Flexible, Lightweight Virtualization Alternative,
... which the host exposes an abstraction of objects: variablesize byte containers, each with a unique identifier and a set of associated attributes. An object can be created, deleted, read from, written to, truncated, and have its attributes be retrieved and manipulated. This small set of operations ma ...
... which the host exposes an abstraction of objects: variablesize byte containers, each with a unique identifier and a set of associated attributes. An object can be created, deleted, read from, written to, truncated, and have its attributes be retrieved and manipulated. This small set of operations ma ...
Quality is Advantage
... After completing this course, you will be able to: Describe the process for replacing or upgrading personal computer components and apply preventive maintenance and troubleshooting techniques Describe the processes used to install, upgrade, configure, and optimize a computer operating system, and ap ...
... After completing this course, you will be able to: Describe the process for replacing or upgrading personal computer components and apply preventive maintenance and troubleshooting techniques Describe the processes used to install, upgrade, configure, and optimize a computer operating system, and ap ...
The Abstraction: The Process
... this memory and gives it to the process. The OS will also likely initialize the stack with arguments; specifically, it will fill in the parameters to the main() function, i.e., argc and the argv array. The OS may also allocate some memory for the program’s heap. In C programs, the heap is used for e ...
... this memory and gives it to the process. The OS will also likely initialize the stack with arguments; specifically, it will fill in the parameters to the main() function, i.e., argc and the argv array. The OS may also allocate some memory for the program’s heap. In C programs, the heap is used for e ...
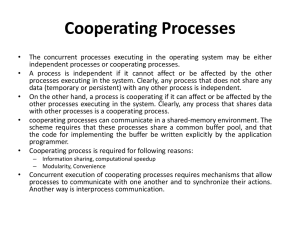
Cooperating Processes
... the code for implementing the buffer be written explicitly by the application programmer. Cooperating process is required for following reasons: – Information sharing, computational speedup – Modularity, Convenience ...
... the code for implementing the buffer be written explicitly by the application programmer. Cooperating process is required for following reasons: – Information sharing, computational speedup – Modularity, Convenience ...
Multimedia Traffic Security Architecture for the Internet of Things
... Media-Aware Traffic Security Architecture In order to meet the information security requirements for multimedia communication, computation, and service in the environment of an IoT, it is necessary to consider some criteria that refer to the traffic security strategy and performance. In this section ...
... Media-Aware Traffic Security Architecture In order to meet the information security requirements for multimedia communication, computation, and service in the environment of an IoT, it is necessary to consider some criteria that refer to the traffic security strategy and performance. In this section ...
P - Bilkent University Computer Engineering Department
... Consider the resources that are allocated at the moment. Consider the process that has the highest numbered allocated resource. – That process will not block; will be able to continue and finish. Because: • It can not make a request to a resource with a smaller number and get block. This will not ha ...
... Consider the resources that are allocated at the moment. Consider the process that has the highest numbered allocated resource. – That process will not block; will be able to continue and finish. Because: • It can not make a request to a resource with a smaller number and get block. This will not ha ...
[slides] I/O systems
... Transforming I/O Requests to Hardware Operations Streams Performance ...
... Transforming I/O Requests to Hardware Operations Streams Performance ...
lect_3
... A process terminates when it finishes executing its final instruction and asks the OS to delete it by calling exit() system call The child process returns the output value to its parent via a wait() system call. All the resources are deallocated by the OS. Only the parent process can terminate its c ...
... A process terminates when it finishes executing its final instruction and asks the OS to delete it by calling exit() system call The child process returns the output value to its parent via a wait() system call. All the resources are deallocated by the OS. Only the parent process can terminate its c ...
Development of DNS
... • NCP based ARPANET -> TCP/IP based network – Large timesharing systems -> Large system plus multiple workstations – Control based on domains/organizations rather than single location. ...
... • NCP based ARPANET -> TCP/IP based network – Large timesharing systems -> Large system plus multiple workstations – Control based on domains/organizations rather than single location. ...
Policy based Management of Content Distribution
... aggregates into several different service classes, and the content distribution approach is based upon deploying a number of proxy servers scattered within the network that use a variety of caching techniques to improve the response time of web-based applications. While each approach has its own adv ...
... aggregates into several different service classes, and the content distribution approach is based upon deploying a number of proxy servers scattered within the network that use a variety of caching techniques to improve the response time of web-based applications. While each approach has its own adv ...
VIII. Input/Output I/O Hardware
... Common in large storage environments (and becoming more common) ...
... Common in large storage environments (and becoming more common) ...
VIII. Input/Output
... • Secondary Storage • Magnetic disks provide bulk of secondary storage of modern computers • Disks can be removable • Drives attached to computer via I/O bus (e.h., EIDE,ATA, SATA, USB, FC, SCSI, ...) • Host controller (in computer) talks to disk controller (in device) via this ...
... • Secondary Storage • Magnetic disks provide bulk of secondary storage of modern computers • Disks can be removable • Drives attached to computer via I/O bus (e.h., EIDE,ATA, SATA, USB, FC, SCSI, ...) • Host controller (in computer) talks to disk controller (in device) via this ...
Advances in Natural and Applied Sciences
... administrator. Due to the unstable nature of nodes challenges occur during routing a packet from source to destination. As discussed previously the nodes are not stable in nature so the path between the nodes changes from time to time. For initiating a path to transmit data it is essential to identi ...
... administrator. Due to the unstable nature of nodes challenges occur during routing a packet from source to destination. As discussed previously the nodes are not stable in nature so the path between the nodes changes from time to time. For initiating a path to transmit data it is essential to identi ...
OS Virtualization
... table, page fault traps to hypervisor. – Paravirtualized OS: Since OS has been modified to account for hypervisor, page table updates can be followed by call to hypervisor about changes. ...
... table, page fault traps to hypervisor. – Paravirtualized OS: Since OS has been modified to account for hypervisor, page table updates can be followed by call to hypervisor about changes. ...
Every Node Is Born Equal - Academic Server| Cleveland State
... with the nodes within its wireless range or indirectly with other nodes via a dynamically computed, multi-hop route. Routing is one of the key issues in MANETs due to their highly dynamic and distributed nature. In order to facilitate communication within a MANET, an efficient routing protocol is re ...
... with the nodes within its wireless range or indirectly with other nodes via a dynamically computed, multi-hop route. Routing is one of the key issues in MANETs due to their highly dynamic and distributed nature. In order to facilitate communication within a MANET, an efficient routing protocol is re ...
Intelligence Finding MAPs for belief networks is NP-hard
... Diagnostic reasoning, also known as abductive reasoning or explanation, is an important problem in artificial intelligence and its applications, such as natural language understanding, medical diagnosis, circuit fault diagnosis, common-sense explanation, and pattern recognition. Abductive reasoning ...
... Diagnostic reasoning, also known as abductive reasoning or explanation, is an important problem in artificial intelligence and its applications, such as natural language understanding, medical diagnosis, circuit fault diagnosis, common-sense explanation, and pattern recognition. Abductive reasoning ...
Asynchronous Resource Discovery
... weakly connected to each other. Once all peers that are interested know of each other they may cooperate on joint tasks (for example: peers may divide work on a complex computation or may build an overlay network and form a distributed hash table [8, 1, 9, 12, 7] ). Resource discovery may be used as ...
... weakly connected to each other. Once all peers that are interested know of each other they may cooperate on joint tasks (for example: peers may divide work on a complex computation or may build an overlay network and form a distributed hash table [8, 1, 9, 12, 7] ). Resource discovery may be used as ...
GNU
... the freedom to improve the program, and release the improvements to the public (Access to the source code is a precondition for this) ...
... the freedom to improve the program, and release the improvements to the public (Access to the source code is a precondition for this) ...
Distributed operating system
A distributed operating system is a software over a collection of independent, networked, communicating, and physically separate computational nodes. Each individual node holds a specific software subset of the global aggregate operating system. Each subset is a composite of two distinct service provisioners. The first is a ubiquitous minimal kernel, or microkernel, that directly controls that node’s hardware. Second is a higher-level collection of system management components that coordinate the node's individual and collaborative activities. These components abstract microkernel functions and support user applications.The microkernel and the management components collection work together. They support the system’s goal of integrating multiple resources and processing functionality into an efficient and stable system. This seamless integration of individual nodes into a global system is referred to as transparency, or single system image; describing the illusion provided to users of the global system’s appearance as a single computational entity.









![[slides] I/O systems](http://s1.studyres.com/store/data/008422726_1-2cb56c8336d4c09c42da15c554c4a466-300x300.png)