VDI Sales Pitch - Mapview Geographical Solutions Pvt. Ltd.
... Dynamic allocation of work environment ...
... Dynamic allocation of work environment ...
(ble) for construction noise monitoring
... implementation for vehicle noise monitoring in civil engineering applications. There has been research into the development of WSNs for civil airport noise data collection [11] using a Zigbee wireless sensor network and an ARM noise data control module. The network uses a tree topology and utilizes ...
... implementation for vehicle noise monitoring in civil engineering applications. There has been research into the development of WSNs for civil airport noise data collection [11] using a Zigbee wireless sensor network and an ARM noise data control module. The network uses a tree topology and utilizes ...
Computers and Operating Systems - Ms. Wade`s Page
... operating systems because they allow many users to run programs and use the server’s resources at the same time. Windows, Mac OS, Linux, and UNIX all have server versions of their operating systems. UNIX is used for many servers that handle e-mail and Internet access. ...
... operating systems because they allow many users to run programs and use the server’s resources at the same time. Windows, Mac OS, Linux, and UNIX all have server versions of their operating systems. UNIX is used for many servers that handle e-mail and Internet access. ...
What are the Basic Components of computer
... access control typically refers to: a. Proving that security mechanisms perform according to specification b. The flow of data within the system c. Regulating user and process access to various aspects of the system d. None of the above ANS: C 27. A common problem with full-featured operating system ...
... access control typically refers to: a. Proving that security mechanisms perform according to specification b. The flow of data within the system c. Regulating user and process access to various aspects of the system d. None of the above ANS: C 27. A common problem with full-featured operating system ...
ch13
... Suppose we’re reading a single packet or disk block into two or more non-contiguous pages The I/O transfer has to use more than one (address, length) pair for that transfer to scatter the data around memory The same applies on output, where it has to be gathered from different physical pages ...
... Suppose we’re reading a single packet or disk block into two or more non-contiguous pages The I/O transfer has to use more than one (address, length) pair for that transfer to scatter the data around memory The same applies on output, where it has to be gathered from different physical pages ...
Document
... Parallel Programming Models • Different approaches are used in the development of parallel programs ...
... Parallel Programming Models • Different approaches are used in the development of parallel programs ...
Pinpointing connectivity despite hidden nodes within stimulus-driven networks Duane Q. Nykamp 兲
... we have ignored the activity of all nodes except for one 共setting Rs̃k,i = 0 for s̃ ⫽ s兲. Since, of course, the single-node model will have different parameters, we denoted the change by removing the bar over the probability distribution. We assume that the HAH model chosen for 共6兲 is an identifiabl ...
... we have ignored the activity of all nodes except for one 共setting Rs̃k,i = 0 for s̃ ⫽ s兲. Since, of course, the single-node model will have different parameters, we denoted the change by removing the bar over the probability distribution. We assume that the HAH model chosen for 共6兲 is an identifiabl ...
CS 519 -- Operating Systems -
... When an event of interest occurs the kernel handles the event first, then modifies the process’s stack to look as if the process’s code made a procedure call to the signal handler. When the user process is scheduled next it executes the handler first From the handler the user process returns to wher ...
... When an event of interest occurs the kernel handles the event first, then modifies the process’s stack to look as if the process’s code made a procedure call to the signal handler. When the user process is scheduled next it executes the handler first From the handler the user process returns to wher ...
Notes
... iii. Stack space f. Lightweight processes shares with peer threads. i. Code section ii. Data section iii. OS resource such as open files and signals g. Threads are used when threads work on related jobs. It can be more efficient to use multiple threads, for example providing data to multiple remote ...
... iii. Stack space f. Lightweight processes shares with peer threads. i. Code section ii. Data section iii. OS resource such as open files and signals g. Threads are used when threads work on related jobs. It can be more efficient to use multiple threads, for example providing data to multiple remote ...
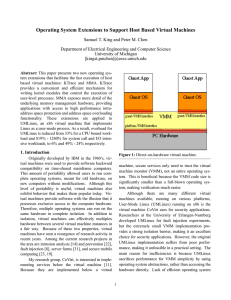
Operating System Extensions to Support Host Based Virtual Machines
... level. For example, an entire Ethernet frame can be sent to the VMM using a single instruction. This significantly reduces the number of guest to VMM traps, and simplifies the design of guest OSs. Denali runs directly on top of the hardware, there is no host operating system. As a consequence, the D ...
... level. For example, an entire Ethernet frame can be sent to the VMM using a single instruction. This significantly reduces the number of guest to VMM traps, and simplifies the design of guest OSs. Denali runs directly on top of the hardware, there is no host operating system. As a consequence, the D ...
Figure 5.01
... Linux refers to them as tasks rather than threads Thread creation is done through clone() system call clone() allows a child task to share the address space ...
... Linux refers to them as tasks rather than threads Thread creation is done through clone() system call clone() allows a child task to share the address space ...
PDF
... Figure 5: Handling of prospective children by a node that has reached its outdegree limit. Circles represent nodes and the numbers close to them are their nodeIds (* is a wildcard). Solid lines indicate that the bottom node is a child of the top node and the number close to the line is the stripeId ...
... Figure 5: Handling of prospective children by a node that has reached its outdegree limit. Circles represent nodes and the numbers close to them are their nodeIds (* is a wildcard). Solid lines indicate that the bottom node is a child of the top node and the number close to the line is the stripeId ...
Using Interaction Networks for Visualisation of Message Passing
... provide operating system services. We give three examples to demonstrate the insights into message-based systems that can be gained from studying interaction network displays. Introduction Many pieces of complex software are structured as processes running different programs that communicate via mes ...
... provide operating system services. We give three examples to demonstrate the insights into message-based systems that can be gained from studying interaction network displays. Introduction Many pieces of complex software are structured as processes running different programs that communicate via mes ...
Routing and Clustering
... (inbound) link quality, send (outbound) link quality, link estimator data structures – Propagate back to the neighbors as the outbound rather than inbound link quality is needed for cost-based routing – The receiving node may update its own table based on the received information possibly indicating ...
... (inbound) link quality, send (outbound) link quality, link estimator data structures – Propagate back to the neighbors as the outbound rather than inbound link quality is needed for cost-based routing – The receiving node may update its own table based on the received information possibly indicating ...
DistSys
... conventional, centralized system and not distinguish between local and remote resources. • User mobility – brings user’s environment (i.e., home directory) to wherever the user logs in. • Fault tolerance – system should continue functioning, perhaps in a degraded form, when faced with various types ...
... conventional, centralized system and not distinguish between local and remote resources. • User mobility – brings user’s environment (i.e., home directory) to wherever the user logs in. • Fault tolerance – system should continue functioning, perhaps in a degraded form, when faced with various types ...
Migration without Virtualization
... to be able to cleanly shutdown any devices that may be attached to it. In addition, the target machine must be able to initialize or reinitialize any devices into a state that corresponds to the state of a matching device on the source machine. Note that this is not hotplugging; the kernel serves no ...
... to be able to cleanly shutdown any devices that may be attached to it. In addition, the target machine must be able to initialize or reinitialize any devices into a state that corresponds to the state of a matching device on the source machine. Note that this is not hotplugging; the kernel serves no ...
Device Interfaces - Flight Software Workshop
... In a POSIX style kernel, drivers live in kernel space and the user interacts through a standard open/close/read/write/ioctl API ...
... In a POSIX style kernel, drivers live in kernel space and the user interacts through a standard open/close/read/write/ioctl API ...
Proceedings of the 5th Symposium on Operating Systems Design and Implementation USENIX Association
... We now briefly discuss a number of outstanding issues with the current ModelNet architecture. Since we do not perform resource isolation among competing VN’s running on the edges, it is possible for a single VN to transmit UDP packets as fast as allowed by the hardware configuration (100 Mbps in our ...
... We now briefly discuss a number of outstanding issues with the current ModelNet architecture. Since we do not perform resource isolation among competing VN’s running on the edges, it is possible for a single VN to transmit UDP packets as fast as allowed by the hardware configuration (100 Mbps in our ...
QFabric System - Juniper Networks
... gateway, enabling customers to protect their investments in existing data center aggregation and FC storage area network ...
... gateway, enabling customers to protect their investments in existing data center aggregation and FC storage area network ...
24-p2p
... – No constraints on how to choose ids for files => easy to have to files collide, creating “denial of service” (censorship) – Solution: have a id type that requires a private key signature that is verified when updating the file – Cache file on the reverse path of queries/publications => attempt to ...
... – No constraints on how to choose ids for files => easy to have to files collide, creating “denial of service” (censorship) – Solution: have a id type that requires a private key signature that is verified when updating the file – Cache file on the reverse path of queries/publications => attempt to ...
Diffserv-MPLS-QoS
... result in shorter routing response time; scalable; searching multiple paths in parallel for a feasible path; routing decision and optimization is done entirely based on local states; Weaknesses: dependence on global state; flooding based algorithms which do not maintain global state have higher co ...
... result in shorter routing response time; scalable; searching multiple paths in parallel for a feasible path; routing decision and optimization is done entirely based on local states; Weaknesses: dependence on global state; flooding based algorithms which do not maintain global state have higher co ...
ppt
... 3. Bounded Waiting - A bound must exist on the number of times that other processes are allowed to enter their critical sections after a process has made a request to enter its critical section and before that request is granted ...
... 3. Bounded Waiting - A bound must exist on the number of times that other processes are allowed to enter their critical sections after a process has made a request to enter its critical section and before that request is granted ...
Dead Reckoning in Mobile Ad Hoc Networks
... speed (uniformly distributed between 0-20 m/sec). Once the destination is reached, another random destination is targeted after a pause. The pause time is varied that affects the relative speed of the mobile nodes. Note also that a lower pause time indicates higher mobility. In this mobility model, ...
... speed (uniformly distributed between 0-20 m/sec). Once the destination is reached, another random destination is targeted after a pause. The pause time is varied that affects the relative speed of the mobile nodes. Note also that a lower pause time indicates higher mobility. In this mobility model, ...
Distributed operating system
A distributed operating system is a software over a collection of independent, networked, communicating, and physically separate computational nodes. Each individual node holds a specific software subset of the global aggregate operating system. Each subset is a composite of two distinct service provisioners. The first is a ubiquitous minimal kernel, or microkernel, that directly controls that node’s hardware. Second is a higher-level collection of system management components that coordinate the node's individual and collaborative activities. These components abstract microkernel functions and support user applications.The microkernel and the management components collection work together. They support the system’s goal of integrating multiple resources and processing functionality into an efficient and stable system. This seamless integration of individual nodes into a global system is referred to as transparency, or single system image; describing the illusion provided to users of the global system’s appearance as a single computational entity.