E42062126
... scheme in [35] may not be able to fully explore the possible performance gain in the buffer management scheme. Second, the absence of an analytical model leaves the scheme simply a heuristic hard to be evaluated. Krifa et al. in [11] proposed an interesting approach for solving the problem of buffer ...
... scheme in [35] may not be able to fully explore the possible performance gain in the buffer management scheme. Second, the absence of an analytical model leaves the scheme simply a heuristic hard to be evaluated. Krifa et al. in [11] proposed an interesting approach for solving the problem of buffer ...
PPT Chapter 07
... real-time systems) or are met probabilistically (soft realtime systems), depending on type of RT system ...
... real-time systems) or are met probabilistically (soft realtime systems), depending on type of RT system ...
Abstract G=
... probabilistic digraph G=(V,E) with a distinguished set of terminal nodes K of V, a sink node s ∈ K, and where the links fail independently with known probabilities (nodes are always operational), let RK,s(G) be the probability that for each node u ∈ K, there exists an operational u,s-dipath spanned ...
... probabilistic digraph G=(V,E) with a distinguished set of terminal nodes K of V, a sink node s ∈ K, and where the links fail independently with known probabilities (nodes are always operational), let RK,s(G) be the probability that for each node u ∈ K, there exists an operational u,s-dipath spanned ...
Processes - Mitra.ac.in
... a) collection of programs that manages hardware resources b) system service provider to the application programs c) link to interface the hardware and application programs d) all of the mentioned 2. To access the services of operating system, the interface is provided by the a) system calls b) API ...
... a) collection of programs that manages hardware resources b) system service provider to the application programs c) link to interface the hardware and application programs d) all of the mentioned 2. To access the services of operating system, the interface is provided by the a) system calls b) API ...
standards - Uni Marburg
... application may send control information along a single channel and application data along a series of channels that may vary depending upon the type of data being sent. The application developer may also take advantage of the MCS concept of private channels to direct data to a discrete subset of a ...
... application may send control information along a single channel and application data along a series of channels that may vary depending upon the type of data being sent. The application developer may also take advantage of the MCS concept of private channels to direct data to a discrete subset of a ...
HotView Pro™ Network Management Software
... to point wireless backhaul—for example, to connect two mesh networks. In the linear mode, both radios operate independently enabling sustained bandwidth levels over an unlimited number of hops. This enables long linear topologies, such as when networking a railway line, and provides a sustained leve ...
... to point wireless backhaul—for example, to connect two mesh networks. In the linear mode, both radios operate independently enabling sustained bandwidth levels over an unlimited number of hops. This enables long linear topologies, such as when networking a railway line, and provides a sustained leve ...
Presentation Title Size 30PT
... What is this chapter about and why is it important? This chapter discusses operating systems (OS). It covers the functions and terminology of operating systems, specifically Windows 2000, Windows XP, and Windows Vista. Because operating system functionality varies, this chapter explains how to d ...
... What is this chapter about and why is it important? This chapter discusses operating systems (OS). It covers the functions and terminology of operating systems, specifically Windows 2000, Windows XP, and Windows Vista. Because operating system functionality varies, this chapter explains how to d ...
20060420_OnLinkScalability_rev1
... Control Traffic on an Active (non-linklocal only) Network on a Stable Link • Active (non-link-local only)? – Every host is communicating only with non-link-local nodes ...
... Control Traffic on an Active (non-linklocal only) Network on a Stable Link • Active (non-link-local only)? – Every host is communicating only with non-link-local nodes ...
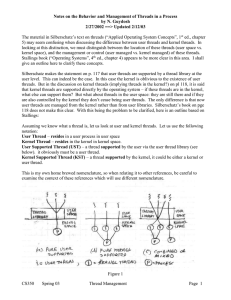
Notes by Guydosh on Thread managment
... creating and destroying threads, passing messages and data between threads, scheduling thread execution, and doing any thread context switching overhead. Since the kernel only sees the process containing these threads, a user thread making a blocking system call (for example I/O) will cause the kern ...
... creating and destroying threads, passing messages and data between threads, scheduling thread execution, and doing any thread context switching overhead. Since the kernel only sees the process containing these threads, a user thread making a blocking system call (for example I/O) will cause the kern ...
No Slide Title
... Sometimes, a waiting process is never again able to change state, because the resources it has requested are held by other waiting processes. This situation is called a DEADLOCK. ...
... Sometimes, a waiting process is never again able to change state, because the resources it has requested are held by other waiting processes. This situation is called a DEADLOCK. ...
UWB CSS 430 Operating Systems: Deadlocks
... are k instances of resource type Rj available • Max: n x m matrix. If Max[i,j] = k, then process Pi may request at most k instances of resource type Rj • Allocation: n x m matrix. If Allocation[i,j] = k then Pi is currently allocated k instances of Rj • Need: n x m matrix. If Need[i,j] = k, then Pi ...
... are k instances of resource type Rj available • Max: n x m matrix. If Max[i,j] = k, then process Pi may request at most k instances of resource type Rj • Allocation: n x m matrix. If Allocation[i,j] = k then Pi is currently allocated k instances of Rj • Need: n x m matrix. If Need[i,j] = k, then Pi ...
Best Practices for Data Sharing in a Grid Distributed
... 2.7 Example migrations from stand-alone to grid Here are two possible examples of applications that are good candidates to consider moving to a distributed or grid environment (there are many others). The first example is a custom SAS® Data Integration or ETL application. The second is a large multi ...
... 2.7 Example migrations from stand-alone to grid Here are two possible examples of applications that are good candidates to consider moving to a distributed or grid environment (there are many others). The first example is a custom SAS® Data Integration or ETL application. The second is a large multi ...
slides
... – Different functions: polynomial, linear, log, exp – Model how fast the unit cost drops with throughput – In practice: a linear combination of different functions ...
... – Different functions: polynomial, linear, log, exp – Model how fast the unit cost drops with throughput – In practice: a linear combination of different functions ...
NEST Counter-Sniper Planning Meeting
... 1. Any system with a non-zero Pfa per sensor node 2. Any non-robust system that requires multiple touches per sensor 3. Any system with performance that can be degraded by a malfunctioning, poorly placed, or imperfect node. 4. Any system that creates a disproportionate response to stimuli 5. Any sys ...
... 1. Any system with a non-zero Pfa per sensor node 2. Any non-robust system that requires multiple touches per sensor 3. Any system with performance that can be degraded by a malfunctioning, poorly placed, or imperfect node. 4. Any system that creates a disproportionate response to stimuli 5. Any sys ...
the case for embedded linux
... providers have built their business on Linux by using it as their service engines. It is also finding its way in many other areas. For example, Digital Domain used over one hundred Linux systems to do the graphics processing for the movie “Titanic”. The Case For Linux Linux is an operating system th ...
... providers have built their business on Linux by using it as their service engines. It is also finding its way in many other areas. For example, Digital Domain used over one hundred Linux systems to do the graphics processing for the movie “Titanic”. The Case For Linux Linux is an operating system th ...
Threads
... Kernel threads is slower to create and manage than user threads If a thread performs a blocking system call, the kernel can schedule ...
... Kernel threads is slower to create and manage than user threads If a thread performs a blocking system call, the kernel can schedule ...
Distributed operating system
A distributed operating system is a software over a collection of independent, networked, communicating, and physically separate computational nodes. Each individual node holds a specific software subset of the global aggregate operating system. Each subset is a composite of two distinct service provisioners. The first is a ubiquitous minimal kernel, or microkernel, that directly controls that node’s hardware. Second is a higher-level collection of system management components that coordinate the node's individual and collaborative activities. These components abstract microkernel functions and support user applications.The microkernel and the management components collection work together. They support the system’s goal of integrating multiple resources and processing functionality into an efficient and stable system. This seamless integration of individual nodes into a global system is referred to as transparency, or single system image; describing the illusion provided to users of the global system’s appearance as a single computational entity.