Operating Systems
... where # is the number of the Linux server that you have connected to. You may use any of the Linux servers. • The number in the brackets will change as you work. It is the “number” of the command that you are about to type. • If this prompt is not on the screen at any time, you are not communicating ...
... where # is the number of the Linux server that you have connected to. You may use any of the Linux servers. • The number in the brackets will change as you work. It is the “number” of the command that you are about to type. • If this prompt is not on the screen at any time, you are not communicating ...
Communicating Sequential Processes
... LISTMAN has a simple protocol defined by two messages - an insert message and a has message. The types insert and has are used to disambiguate the integer value passed on each communication with X. INSERT is code (not shown) that adds the value of n to the array content. SEARCH is the code shown abo ...
... LISTMAN has a simple protocol defined by two messages - an insert message and a has message. The types insert and has are used to disambiguate the integer value passed on each communication with X. INSERT is code (not shown) that adds the value of n to the array content. SEARCH is the code shown abo ...
PPT
... LISTMAN has a simple protocol defined by two messages - an insert message and a has message. The types insert and has are used to disambiguate the integer value passed on each communication with X. INSERT is code (not shown) that adds the value of n to the array content. SEARCH is the code shown abo ...
... LISTMAN has a simple protocol defined by two messages - an insert message and a has message. The types insert and has are used to disambiguate the integer value passed on each communication with X. INSERT is code (not shown) that adds the value of n to the array content. SEARCH is the code shown abo ...
Virtualization rev 01
... philosophy, by providing backup images that can "boot" into live virtual machines, capable of taking over workload for a production server experiencing an outage. ...
... philosophy, by providing backup images that can "boot" into live virtual machines, capable of taking over workload for a production server experiencing an outage. ...
Intrusion Detection in Virtual Machine Environments
... information sent by the VM monitor. The system has two operation modes: a learning mode and a monitoring mode. When executing the learning mode, all the processes executing in the guest system and their respective users are recorded as authorized processes and users, thus generating an access-contro ...
... information sent by the VM monitor. The system has two operation modes: a learning mode and a monitoring mode. When executing the learning mode, all the processes executing in the guest system and their respective users are recorded as authorized processes and users, thus generating an access-contro ...
Chapter 2 – outline
... The operating systems that are design to run on Apple computers. One of the latest versions of MAC OS. Provides a list of options or commands. the ability to switch between different applications stored in memory. Operating systems that are used to control and coordinate computers networked or linke ...
... The operating systems that are design to run on Apple computers. One of the latest versions of MAC OS. Provides a list of options or commands. the ability to switch between different applications stored in memory. Operating systems that are used to control and coordinate computers networked or linke ...
Connecting with Computer Science, 2e
... • Coordinated execution of a process, using two or more CPUs at the same time Connecting with Computer Science, 2e ...
... • Coordinated execution of a process, using two or more CPUs at the same time Connecting with Computer Science, 2e ...
ppt
... secondary storage to back up main memory. Most modern computer systems use disks as the principle on-line storage medium, for both programs and data. The operating system is responsible for the following activities in connection with disk management: Free space management Storage allocation ...
... secondary storage to back up main memory. Most modern computer systems use disks as the principle on-line storage medium, for both programs and data. The operating system is responsible for the following activities in connection with disk management: Free space management Storage allocation ...
4 Operating System Activities
... An operating system is a type of system software that acts as the master controller for all activities that take place within a computer system ...
... An operating system is a type of system software that acts as the master controller for all activities that take place within a computer system ...
ppt
... • Can Frame A change the origin of content for Frame B? • Frame-principal relationships – readCookie(A,S), writeCookie(A,S) • Can Frame A read/write cookies from site S? ...
... • Can Frame A change the origin of content for Frame B? • Frame-principal relationships – readCookie(A,S), writeCookie(A,S) • Can Frame A read/write cookies from site S? ...
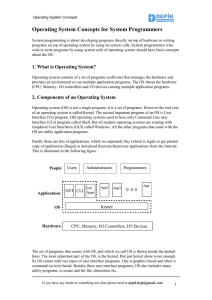
Operating System Concepts for System Programmers
... is called booting process. Following are the various steps involved while booting the OS: The BIOS program present in the non-volatile (ROM/Flash) memory of a computer will run first. In fact whenever a CPU is powered on, it tries to fetch (read) instructions from a fixed start address. The computer ...
... is called booting process. Following are the various steps involved while booting the OS: The BIOS program present in the non-volatile (ROM/Flash) memory of a computer will run first. In fact whenever a CPU is powered on, it tries to fetch (read) instructions from a fixed start address. The computer ...
Operating System Structure
... Some of them are simply user interfaces to system calls; others ...
... Some of them are simply user interfaces to system calls; others ...
2015/16 Cyber Security Survey Results
... continuously refining their efforts to compromise systems, networks and information worldwide. The financial sector is one of the more prominent targets for such attacks, and recent incidents involving financial institutions in Bangladesh, Vietnam, South Africa, Japan and Ecuador demonstrate the abs ...
... continuously refining their efforts to compromise systems, networks and information worldwide. The financial sector is one of the more prominent targets for such attacks, and recent incidents involving financial institutions in Bangladesh, Vietnam, South Africa, Japan and Ecuador demonstrate the abs ...
Processes and Threads - University of Waterloo
... privileges ● a stack (located in the process' address space) Multiple threads within the same process can be thought of as processes that share their address space (code, data, open files, etc.). Whether there is an implementation difference between a thread and a process depends on the OS. Nachos: ...
... privileges ● a stack (located in the process' address space) Multiple threads within the same process can be thought of as processes that share their address space (code, data, open files, etc.). Whether there is an implementation difference between a thread and a process depends on the OS. Nachos: ...
Glossary of Terms, Abbreviations, and Acronyms
... Process of rendering cardholder data unreadable by converting data into a fixed-length message digest via Strong Cryptography. Hashing is a (mathematical) function in which a non-secret algorithm takes any arbitrary length message as input and produces a fixed length output (usually called a “hash c ...
... Process of rendering cardholder data unreadable by converting data into a fixed-length message digest via Strong Cryptography. Hashing is a (mathematical) function in which a non-secret algorithm takes any arbitrary length message as input and produces a fixed length output (usually called a “hash c ...
Operating-System Structures
... Some of them are simply user interfaces to system calls; others ...
... Some of them are simply user interfaces to system calls; others ...
1.01 - UCSB Computer Science
... Protection – any mechanism for controlling access of processes or ...
... Protection – any mechanism for controlling access of processes or ...
Abstract View of System Components
... The protection mechanism must: distinguish between authorized and unauthorized usage. specify the controls to be imposed. provide a means of enforcement. ...
... The protection mechanism must: distinguish between authorized and unauthorized usage. specify the controls to be imposed. provide a means of enforcement. ...
Abstract View of System Components
... Usually takes the form of a trap to a specific location in the interrupt vector. Control passes through the interrupt vector to a service routine in the OS, and the mode bit is set to monitor mode by interrupt HW. The monitor verifies that the parameters are correct and legal, executes the I/O ...
... Usually takes the form of a trap to a specific location in the interrupt vector. Control passes through the interrupt vector to a service routine in the OS, and the mode bit is set to monitor mode by interrupt HW. The monitor verifies that the parameters are correct and legal, executes the I/O ...
slides
... A process has multiple thread. One of them called fork(). Should fork() duplicate only the calling thread or all threads (entire ...
... A process has multiple thread. One of them called fork(). Should fork() duplicate only the calling thread or all threads (entire ...