Document
... 12. List out the services provided by operating systems to programs and to the 13. Define operating system and list out the function and component of operating system. 14. Explain in detail the modern computer system 15. Explain the abstract view of the components of a computer system 16. Explain Vo ...
... 12. List out the services provided by operating systems to programs and to the 13. Define operating system and list out the function and component of operating system. 14. Explain in detail the modern computer system 15. Explain the abstract view of the components of a computer system 16. Explain Vo ...
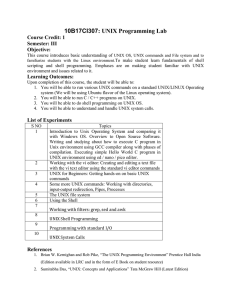
10B17CI307: UNIX Programming Lab
... scripting and shell programming. Emphases are on making student familiar with UNIX environment and issues related to it. ...
... scripting and shell programming. Emphases are on making student familiar with UNIX environment and issues related to it. ...
SECDO Platform White Paper -
... Gathering information for forensic analysis is so time-consuming and labor intensive that it inevitably delays the remediation of a breach. Because the SECDO platform continuously collects detailed endpoint and server activity and typically saves it for 100 days (the actual number is configurable), ...
... Gathering information for forensic analysis is so time-consuming and labor intensive that it inevitably delays the remediation of a breach. Because the SECDO platform continuously collects detailed endpoint and server activity and typically saves it for 100 days (the actual number is configurable), ...
lecture10
... particular system entity—either local or remote—must be both invisible to, and undetectable by the user. • Location transparency - Location transparency comprises two distinct subaspects of transparency, Naming transparency and User mobility. Naming transparency requires that nothing in the physical ...
... particular system entity—either local or remote—must be both invisible to, and undetectable by the user. • Location transparency - Location transparency comprises two distinct subaspects of transparency, Naming transparency and User mobility. Naming transparency requires that nothing in the physical ...
(Silberschatz) I/O subsystems
... If device can serve only one request at a time i.e., Printing Device reservation - provides exclusive access to a ...
... If device can serve only one request at a time i.e., Printing Device reservation - provides exclusive access to a ...
ch3
... processor with its own memory The resources of the physical computer are shared: CPU is scheduled (shared) among the virtual machines File system and devices are shared/allocated to virtual machines A normal user time-sharing terminal serves as the virtual machine ...
... processor with its own memory The resources of the physical computer are shared: CPU is scheduled (shared) among the virtual machines File system and devices are shared/allocated to virtual machines A normal user time-sharing terminal serves as the virtual machine ...
Unit 2
... • Software interrupts – Limited data exchange – Processes may catch, ignore or mask a signal • Catch: run specific function on signal • Ignore: let OS run default function • Mask: prevent signal from occurring ...
... • Software interrupts – Limited data exchange – Processes may catch, ignore or mask a signal • Catch: run specific function on signal • Ignore: let OS run default function • Mask: prevent signal from occurring ...
Presentation4 - University Of Worcester
... » policy should be enforced by the network itself » usually achieved through use of “group policies” ...
... » policy should be enforced by the network itself » usually achieved through use of “group policies” ...
What is an operating system?
... Multi-tasking Operating Systems Manages resources and processes to support different user applications ...
... Multi-tasking Operating Systems Manages resources and processes to support different user applications ...
A Specialization Toolkit to Increase the Diversity of Operating Systems
... To support methodical specialization, we have been developing a toolkit that helps the kernel programmer in the tedious but important task of making specialized modules correct. For example, we have developed a specializer (called Tempo-C) [2, 1J for dynamic partial evaluation of C code, to simplify ...
... To support methodical specialization, we have been developing a toolkit that helps the kernel programmer in the tedious but important task of making specialized modules correct. For example, we have developed a specializer (called Tempo-C) [2, 1J for dynamic partial evaluation of C code, to simplify ...
Cardenas_Claudia_WorkShopSlides
... In terms of the PHY layer most of these attacks can be counteracted by using different signals and proper configuration of the protocol. Some of MAC flaws have been fixed by the enhanced security of IEEE 802.16e but not all of them. The lack of encryption of MAC management messages that can affect t ...
... In terms of the PHY layer most of these attacks can be counteracted by using different signals and proper configuration of the protocol. Some of MAC flaws have been fixed by the enhanced security of IEEE 802.16e but not all of them. The lack of encryption of MAC management messages that can affect t ...
Terminal Control - Utah Valley University
... What if this program was running in an atm machine, and the person walked away without typing ‘y’ or ‘n’? Someone else could walk up and run a transaction using this person’s account. ...
... What if this program was running in an atm machine, and the person walked away without typing ‘y’ or ‘n’? Someone else could walk up and run a transaction using this person’s account. ...
Module 3: Operating
... secondary storage to back up main memory. Most modern computer systems use disks as the principle on-line storage medium, for both programs and data. The operating system is responsible for the following activities in connection with disk management: Free space management Storage allocation ...
... secondary storage to back up main memory. Most modern computer systems use disks as the principle on-line storage medium, for both programs and data. The operating system is responsible for the following activities in connection with disk management: Free space management Storage allocation ...
Chapter 3: Operating-System Structures Common System
... secondary storage to back up main memory. ■ Most modern computer systems use disks as the principle on-line storage medium, for both programs and data. ■ The operating system is responsible for the following activities in connection with disk management: ✦ Free space management ✦ Storage allocation ...
... secondary storage to back up main memory. ■ Most modern computer systems use disks as the principle on-line storage medium, for both programs and data. ■ The operating system is responsible for the following activities in connection with disk management: ✦ Free space management ✦ Storage allocation ...
System Software
... the computer Loaded into memory each time a computer is started When a new device is added, new device drivers must be installed Add a Device Wizard – step-by-step Windows already has many drivers within the system software ...
... the computer Loaded into memory each time a computer is started When a new device is added, new device drivers must be installed Add a Device Wizard – step-by-step Windows already has many drivers within the system software ...
View
... secondary storage to back up main memory. Most modern computer systems use disks as the principle on-line storage medium, for both programs and data. The operating system is responsible for the following activities in connection with disk management: Free space management Storage allocation ...
... secondary storage to back up main memory. Most modern computer systems use disks as the principle on-line storage medium, for both programs and data. The operating system is responsible for the following activities in connection with disk management: Free space management Storage allocation ...
choices
... – PURE is for deeply embedded systems – PURE extension has an OSEK API – PURE uses the concept of components at the design level, and avoids artificical boundaries in implementation concerning run time and code size – PURE is fine-grained ...
... – PURE is for deeply embedded systems – PURE extension has an OSEK API – PURE uses the concept of components at the design level, and avoids artificical boundaries in implementation concerning run time and code size – PURE is fine-grained ...
Security - The University of Texas at Dallas
... • You hear them murmur, "Let's see you use that VISA card now, Professor "I-Don't-Give-A's-To Any MBA Candidate!" ...
... • You hear them murmur, "Let's see you use that VISA card now, Professor "I-Don't-Give-A's-To Any MBA Candidate!" ...
INTRODUCTION TO THE STUDY OF CONSUMER BEHAVIOUR
... system) is still in use today for a variety of reasons. DOS originally came into widespread use in the 1980s, with the appearance of the IBM PC, which was the first personal computer to catch on with consumers and businesses. Two versions of DOS reigned as the desktop operating system of choice thro ...
... system) is still in use today for a variety of reasons. DOS originally came into widespread use in the 1980s, with the appearance of the IBM PC, which was the first personal computer to catch on with consumers and businesses. Two versions of DOS reigned as the desktop operating system of choice thro ...
Figure 1-3
... • Help ensure memory is used properly and there are no memory conflicts • Manages how programs access the processing capabilities of the CPU – Example: if there is one CPU and ten programs that want to access the CPU, the OS will give each program a time slice on the CPU • Each program does a little ...
... • Help ensure memory is used properly and there are no memory conflicts • Manages how programs access the processing capabilities of the CPU – Example: if there is one CPU and ten programs that want to access the CPU, the OS will give each program a time slice on the CPU • Each program does a little ...