L03 - UMBC
... Provides a uniform interface for users and programs to access changing, evolving hardware (H/W) Very different H/W platforms can support a common OS (partially custom-written, of course) (standard “PC”, Sony PSP can both run Linux) One H/W platform can support multiple OSs ...
... Provides a uniform interface for users and programs to access changing, evolving hardware (H/W) Very different H/W platforms can support a common OS (partially custom-written, of course) (standard “PC”, Sony PSP can both run Linux) One H/W platform can support multiple OSs ...
Symbian - T-Dose
... What does he do? • Acts as gatekeeper between apps and system • Performs signature check • Performs capability check • Handles file moving ...
... What does he do? • Acts as gatekeeper between apps and system • Performs signature check • Performs capability check • Handles file moving ...
Symbolic Honeynets for Gathering Cyber
... Identify vulnerabilities & exploits of IEC61850 substation automation systems using hardware-in-the-loop realtime testing. Develop a framework that addresses holistic integrity in realtime by enforcing trust policies and controls and by enabling security mechanisms and tools (engines). ...
... Identify vulnerabilities & exploits of IEC61850 substation automation systems using hardware-in-the-loop realtime testing. Develop a framework that addresses holistic integrity in realtime by enforcing trust policies and controls and by enabling security mechanisms and tools (engines). ...
Operating Systems Security
... to pay for it, in financial, convenience, performance and other terms. A perfectly secure system is unlikely to be popular since it will by necessity, omit many of the popular but highly insecure features to which people have become accustomed. Interestingly many of the emerging problems that are no ...
... to pay for it, in financial, convenience, performance and other terms. A perfectly secure system is unlikely to be popular since it will by necessity, omit many of the popular but highly insecure features to which people have become accustomed. Interestingly many of the emerging problems that are no ...
operating systems - Ronny`s Web Site
... • Kernel:-The kernel which is the care of os. The kernel is also called real time executive. The kernel contains all the devices that interact with the hardware. ...
... • Kernel:-The kernel which is the care of os. The kernel is also called real time executive. The kernel contains all the devices that interact with the hardware. ...
Securing the Network - Austin Community College
... The survival of many businesses depends on allowing open access to network resources and ensuring that data and resources are as secure as possible. The escalating importance of e-business and the need for private data to traverse potentially unsafe public networks both increase the need for the dev ...
... The survival of many businesses depends on allowing open access to network resources and ensuring that data and resources are as secure as possible. The escalating importance of e-business and the need for private data to traverse potentially unsafe public networks both increase the need for the dev ...
4th Chapter - information systems and it audit
... • Automatic disability of un-used display for a time • Logon attempts Log • Information about communication line connected • Test of Logical Security: Chapter # : 04 - CISA ...
... • Automatic disability of un-used display for a time • Logon attempts Log • Information about communication line connected • Test of Logical Security: Chapter # : 04 - CISA ...
Web Security
... public-key from the certificate to encrypt the generated session key for protecting the conversation between the source and destination. • Session is encrypted using a symmetric cipher (slow) • conversation is encrypted using an asymmetric cipher (fast) • its done this way to speed up overall commun ...
... public-key from the certificate to encrypt the generated session key for protecting the conversation between the source and destination. • Session is encrypted using a symmetric cipher (slow) • conversation is encrypted using an asymmetric cipher (fast) • its done this way to speed up overall commun ...
NSS Labs 2015 Enterprise Endpoint Testing
... This and other related documents available at: www.nsslabs.com. To receive a licensed copy or report misuse, please contact NSS Labs. © 2015 NSS Labs, Inc. All rights reserved. No part of this publication may be reproduced, copied/scanned, stored on a retrieval system, e-mailed or otherwise dissemin ...
... This and other related documents available at: www.nsslabs.com. To receive a licensed copy or report misuse, please contact NSS Labs. © 2015 NSS Labs, Inc. All rights reserved. No part of this publication may be reproduced, copied/scanned, stored on a retrieval system, e-mailed or otherwise dissemin ...
Steps of porting (cont
... is simple and well-designed Unix consider all the things as ‘files’ in system Kernel and system utilities are written by C language which is portable very short time to create process easy and stableness inter-process ...
... is simple and well-designed Unix consider all the things as ‘files’ in system Kernel and system utilities are written by C language which is portable very short time to create process easy and stableness inter-process ...
DISTRIBUTED OPERATING SYSTEM
... execution may require specialized processor - Software preference – required software may be available at only a particular site - Data access – run process remotely, rather than transfer all data locally ...
... execution may require specialized processor - Software preference – required software may be available at only a particular site - Data access – run process remotely, rather than transfer all data locally ...
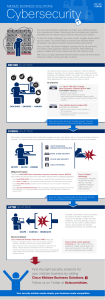
View the graphic
... You face unprecedented challenges to protect your midsize business from cybersecurity threats. New trends such as mobility and cloud are changing how you need to secure devices, data and your network. To deal with these challenges, you need a smart, scalable threat-centric security model. This model ...
... You face unprecedented challenges to protect your midsize business from cybersecurity threats. New trends such as mobility and cloud are changing how you need to secure devices, data and your network. To deal with these challenges, you need a smart, scalable threat-centric security model. This model ...
What is an Operating System?
... No longer need to maximize CPU utilization. Some have not: File protection and user isolation, needed on multitasking mainframes to separate user, are now needed for virus isolation on networked PCs with only a single user. ...
... No longer need to maximize CPU utilization. Some have not: File protection and user isolation, needed on multitasking mainframes to separate user, are now needed for virus isolation on networked PCs with only a single user. ...
Functions of the operating systems
... Input and output: allows computer to display and get data from the I/O devices to interact with users. 2. Memory and secondary storage management: 1. allows the user to organize their data on secondary storage into files & folders 2. also manages the use of main memory by splitting main memory into ...
... Input and output: allows computer to display and get data from the I/O devices to interact with users. 2. Memory and secondary storage management: 1. allows the user to organize their data on secondary storage into files & folders 2. also manages the use of main memory by splitting main memory into ...
Operating Systems
... The information was piled into a job queue; the computer reads one job at a time (first-come firstserved), performs it, then goes to the next job This is batch processing — the jobs in the queue form a “batch of work” to be done in sequence The control program that cycled through reading then runnin ...
... The information was piled into a job queue; the computer reads one job at a time (first-come firstserved), performs it, then goes to the next job This is batch processing — the jobs in the queue form a “batch of work” to be done in sequence The control program that cycled through reading then runnin ...
Porting existing software - International Union of Crystallography
... Two easy routes 1. install Linux and dual boot (best environment) 2. install Cygwin (easiest since you can run MS-Windows simultaneously) Each of these provides a fully-featured windowed environment via X11 windows, but Cygwin will produce MS-Windows executables unless you cross-compile! ...
... Two easy routes 1. install Linux and dual boot (best environment) 2. install Cygwin (easiest since you can run MS-Windows simultaneously) Each of these provides a fully-featured windowed environment via X11 windows, but Cygwin will produce MS-Windows executables unless you cross-compile! ...
10.2 BASIC E-COMMERCE SECURITY ISSUES AND LANDSCAPE
... Availability: The assurance that access to any relevant data, information websites, or other EC services and their use is available in real time, whenever and wherever needed. ...
... Availability: The assurance that access to any relevant data, information websites, or other EC services and their use is available in real time, whenever and wherever needed. ...
Bhargavi Konduru`s presentation on Constructing Secure Operating
... consists of TL4 microkernel, the multiple instances of a μITRON kernel. Multiple applications can run within a single instance of a μITRON kernel. Applications can access services provided by servers through server proxies. Only TL4 microkernel executes in the privileged mode directly on top o ...
... consists of TL4 microkernel, the multiple instances of a μITRON kernel. Multiple applications can run within a single instance of a μITRON kernel. Applications can access services provided by servers through server proxies. Only TL4 microkernel executes in the privileged mode directly on top o ...
Integrity - Andrew.cmu.edu
... – attacker ensures that all network packets are routed to him or her before they are transmitted to their final destination ...
... – attacker ensures that all network packets are routed to him or her before they are transmitted to their final destination ...
CS 471-001: Operating Systems Spring 2017 Department of
... an official/verifiable proof of why you are missing the exam before the exam. Once it is validated, instructor can arrange a make exam. Honor code: - All students must adhere to the GMU Honor Code and the Computer Science Department's Honor Code Policies. - The students are supposed to work indi ...
... an official/verifiable proof of why you are missing the exam before the exam. Once it is validated, instructor can arrange a make exam. Honor code: - All students must adhere to the GMU Honor Code and the Computer Science Department's Honor Code Policies. - The students are supposed to work indi ...
(MSWindows, LINUX, UNIX) (China)
... Unix to Unix copy program A batch-processing/spooling system Typically used between systems with dial-up telephone lines or direct serial lines ...
... Unix to Unix copy program A batch-processing/spooling system Typically used between systems with dial-up telephone lines or direct serial lines ...
slides - Computer Science
... Approach 3: Wimps reuse giant-provided services but only after efficiently ...
... Approach 3: Wimps reuse giant-provided services but only after efficiently ...
Data Mining BS/MS Project
... Clusters are shown as different colors in this visual, anomaly detection identifies the outliers (axes/instances for this graph are not specified in the paper) ...
... Clusters are shown as different colors in this visual, anomaly detection identifies the outliers (axes/instances for this graph are not specified in the paper) ...