Amoeba Vs. Mach OS
... Protocol) for actual message transmission. In OSI terms, FLIP is a network layer protocol, whereas RPC is more of connectionless transport or session protocol. Mach allows messages to be transmitted from one process to another using the copy-on-write mechanism. Amoeba does not have this. Ports: In A ...
... Protocol) for actual message transmission. In OSI terms, FLIP is a network layer protocol, whereas RPC is more of connectionless transport or session protocol. Mach allows messages to be transmitted from one process to another using the copy-on-write mechanism. Amoeba does not have this. Ports: In A ...
Design of Hybrid Kernel and the Performance Improvement of
... The new task fetches original information from corresponding PCB. The time switching consumed depends on the processor architecture, because different processors need to preserve and restore different number of registers; some processors have a single special instruction which is able to achieve all ...
... The new task fetches original information from corresponding PCB. The time switching consumed depends on the processor architecture, because different processors need to preserve and restore different number of registers; some processors have a single special instruction which is able to achieve all ...
Multicores
... Track of which process opens up which queue for what. If a process opens up the queue for read-only access, then later tries to write the queue, it can cause problems. If the number of concurrently executing] tasks involved is small, this can be readily managed. However, once you move beyond a dozen ...
... Track of which process opens up which queue for what. If a process opens up the queue for read-only access, then later tries to write the queue, it can cause problems. If the number of concurrently executing] tasks involved is small, this can be readily managed. However, once you move beyond a dozen ...
Total cost of ownership – Linux vs. QNX realtime operating system
... In contrast, the QNX realtime OS (RTOS) is designed with a microkernel architecture. This architectuture provides an extensive level of fault containment and recovery. The microkernel architecture means that every driver, protocol stack, filesystem and application runs outside the kernel, in the saf ...
... In contrast, the QNX realtime OS (RTOS) is designed with a microkernel architecture. This architectuture provides an extensive level of fault containment and recovery. The microkernel architecture means that every driver, protocol stack, filesystem and application runs outside the kernel, in the saf ...
ppt - UNSW
... °The I/O system is shared by multiple programs using the processor °Low-level control of I/O devices is complex because requires managing a set of concurrent events and because requirements for correct device control are often very detailed °I/O systems often use interrupts to communicate informatio ...
... °The I/O system is shared by multiple programs using the processor °Low-level control of I/O devices is complex because requires managing a set of concurrent events and because requirements for correct device control are often very detailed °I/O systems often use interrupts to communicate informatio ...
Chapter 1: Introduction
... jobs so frequently that users can interact with each job while it is running, creating interactive computing ...
... jobs so frequently that users can interact with each job while it is running, creating interactive computing ...
[slides] Introduction to operating systems
... jobs so frequently that users can interact with each job while it is running, creating interactive computing ...
... jobs so frequently that users can interact with each job while it is running, creating interactive computing ...
Chapter 2 Computer System Structure
... AndrewGalvin O’Shauqhnessy, Unix world Silberschatz, and Gagne 2002 ...
... AndrewGalvin O’Shauqhnessy, Unix world Silberschatz, and Gagne 2002 ...
Types of Attacks - Digital Locker and Personal Web Space
... • Attacker observes all network traffic. – Software, hardware, or combination of the two – Ability to target specific protocol, service, string of characters, etc. – May be able to modify some or all traffic in route • Network administrators can use to monitor and troubleshoot network performance. ...
... • Attacker observes all network traffic. – Software, hardware, or combination of the two – Ability to target specific protocol, service, string of characters, etc. – May be able to modify some or all traffic in route • Network administrators can use to monitor and troubleshoot network performance. ...
A Reflective Middleware Framework for Communication in
... Unbounded-buffer places no practical limit on the size of the buffer. Consumer may wait, producer never waits. Bounded-buffer assumes that there is a fixed buffer size. Consumer waits for new item, producer waits if buffer is full. ...
... Unbounded-buffer places no practical limit on the size of the buffer. Consumer may wait, producer never waits. Bounded-buffer assumes that there is a fixed buffer size. Consumer waits for new item, producer waits if buffer is full. ...
lect_3
... Program counter: indicates the address of the next instruction to be executed for this process. CPU registers: they include index registers, stack pointers, and general purpose registers, and condition code information. Along with the program counter, this information must be saved when an interrupt ...
... Program counter: indicates the address of the next instruction to be executed for this process. CPU registers: they include index registers, stack pointers, and general purpose registers, and condition code information. Along with the program counter, this information must be saved when an interrupt ...
I/O Systems
... registers in two ways: I/O instructions: in/out instructions Example from the Intel architecture: out 0x21,AL Memory mapped I/O: load/store instructions Registers/memory appear in physical address space I/O accomplished with load and store instructions Operating System Concepts – 8th Editi ...
... registers in two ways: I/O instructions: in/out instructions Example from the Intel architecture: out 0x21,AL Memory mapped I/O: load/store instructions Registers/memory appear in physical address space I/O accomplished with load and store instructions Operating System Concepts – 8th Editi ...
4.3 Operations on Processes 4.3.1 Process Creation
... processes to communicate with one another and to synchronize their actions. To illustrate the concept of cooperating processes, let us consider the producerconsumer problem, which is a common paradigm for cooperating processes. A producer process produces information that is consumed by a consumer p ...
... processes to communicate with one another and to synchronize their actions. To illustrate the concept of cooperating processes, let us consider the producerconsumer problem, which is a common paradigm for cooperating processes. A producer process produces information that is consumed by a consumer p ...
Operating Systems
... • e.g. linux is a “kernel”, but has kernel modules and certain servers. • e.g. Windows NT was originally microkernel (3.5), but now (4.0 onwards) pushed lots back into kernel for performance. • Still not clear what the best OS structure is, or how much it really matters. . . ...
... • e.g. linux is a “kernel”, but has kernel modules and certain servers. • e.g. Windows NT was originally microkernel (3.5), but now (4.0 onwards) pushed lots back into kernel for performance. • Still not clear what the best OS structure is, or how much it really matters. . . ...
Introduction to Linux Winelfred G. Pasamba Dec 9, 2005 Finster Hall
... We are not forcing you to use Linux or forcing you to stop using Windows, Or judge which is better than the other, We show you the benefits, but the choice is ...
... We are not forcing you to use Linux or forcing you to stop using Windows, Or judge which is better than the other, We show you the benefits, but the choice is ...
Windows 95/98/NT (Introduction)
... • IFS (Installable File System) Manager. This is the arbiter for the access to different file system components. On MS-DOS and Windows 3.x it was provided by interrupt 21h. Unfortunately, some add-on components did not run correctly and interfered with other installed drivers. It also did not direct ...
... • IFS (Installable File System) Manager. This is the arbiter for the access to different file system components. On MS-DOS and Windows 3.x it was provided by interrupt 21h. Unfortunately, some add-on components did not run correctly and interfered with other installed drivers. It also did not direct ...
modelpaper
... allocation algorithm with the help of suitable examples. 32.Explain the term Trashing. What are the basic causes of Trashing? How it can be minimized? 33.Compare the term Demand Paging with Demand Segmentation. Which scheme is easy to implement the concept of Virtual memory and Why? Justify your ans ...
... allocation algorithm with the help of suitable examples. 32.Explain the term Trashing. What are the basic causes of Trashing? How it can be minimized? 33.Compare the term Demand Paging with Demand Segmentation. Which scheme is easy to implement the concept of Virtual memory and Why? Justify your ans ...
Implementing Processes, Threads, and Resources
... Windows NT Process Descriptor (2) Kernel process object including: ...
... Windows NT Process Descriptor (2) Kernel process object including: ...
Lecture #14: Deadlocks
... wait, since resources are not available 3. Pretend to allocate requested resources to Pi by modifying the state as follows: ...
... wait, since resources are not available 3. Pretend to allocate requested resources to Pi by modifying the state as follows: ...
Webinar Title - Websense Knowledge Bases
... The parameters can be entered via command line as well during installation. Please review the Remote filtering document for more details. 23. Are the remote clients filtered based on the same exact rules as if they were local? Yes provided you have configured policy based on their Username and users ...
... The parameters can be entered via command line as well during installation. Please review the Remote filtering document for more details. 23. Are the remote clients filtered based on the same exact rules as if they were local? Yes provided you have configured policy based on their Username and users ...
lec-3 - WordPress.com
... When the computer is turned on, the CPU counter (a type of the CPU registers) is set to the first instruction of this bootstrap program and executes the instructions in this program. When loading is done, the program counter is set to the first instruction of the operating system in ...
... When the computer is turned on, the CPU counter (a type of the CPU registers) is set to the first instruction of this bootstrap program and executes the instructions in this program. When loading is done, the program counter is set to the first instruction of the operating system in ...
Copy area
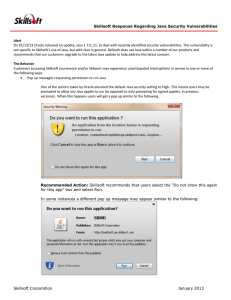
... Java in Firefox may experience messages similar to the following instructing them to check for updates to Java. ...
... Java in Firefox may experience messages similar to the following instructing them to check for updates to Java. ...
Operating System Fundamentals
... wider than the I/O busses because it is wider and faster. It contains more wires (traces) for the transmission of data between the devices. In the comparison to a city, the Front Side Bus is like a major freeway with a fast speed limit. The smaller I/O busses are like smaller side streets. Some of t ...
... wider than the I/O busses because it is wider and faster. It contains more wires (traces) for the transmission of data between the devices. In the comparison to a city, the Front Side Bus is like a major freeway with a fast speed limit. The smaller I/O busses are like smaller side streets. Some of t ...
Document
... • For server products and libraries, keep up with the latest bug reports for the products you are using. • Periodically scan your web site with one or more of the commonly available scanners that look for buffer overflow flaws in your server products and your custom web applications. • Size checking ...
... • For server products and libraries, keep up with the latest bug reports for the products you are using. • Periodically scan your web site with one or more of the commonly available scanners that look for buffer overflow flaws in your server products and your custom web applications. • Size checking ...





![[slides] Introduction to operating systems](http://s1.studyres.com/store/data/004490643_1-47ee4d56929de85b34d4b2999d518b36-300x300.png)