An Operating System for Multicore and Clouds: Mechanisms and Implementation
... the right amount of computing, memory, I/O, and storage to meet their needs at any given time. Unfortunately, counter to the vision, current IaaS systems do not provide the user the same experience as if they were accessing an infinitely scalable multiprocessor computer where resources such as memor ...
... the right amount of computing, memory, I/O, and storage to meet their needs at any given time. Unfortunately, counter to the vision, current IaaS systems do not provide the user the same experience as if they were accessing an infinitely scalable multiprocessor computer where resources such as memor ...
Process
... Sharing of memory, files and other resources of the process to which the threads belong ...
... Sharing of memory, files and other resources of the process to which the threads belong ...
ch13
... Varying enough from block and character to have own interface Unix and Windows NT/9x/2000 include socket interface ...
... Varying enough from block and character to have own interface Unix and Windows NT/9x/2000 include socket interface ...
Operating Systems for Reconfigurable Systems
... The challenges in developing an OS for reconfigurable systems ...
... The challenges in developing an OS for reconfigurable systems ...
What is a Real-Time Operating Systems
... Satellite guidance systems Patient Monitoring System Control Systems for synchrotrons ...
... Satellite guidance systems Patient Monitoring System Control Systems for synchrotrons ...
Introduction to Computer Security
... • Bot-nets of zombie machines that can be commanded to flood and disable “on-command” • Discovery of botnets with 10-100 systems is a daily occurrence; 10,000 system botnets are found almost weekly; and one botnet with 100,000 hosts has even been found (according to Johannes Ullrich, CTO of the Inte ...
... • Bot-nets of zombie machines that can be commanded to flood and disable “on-command” • Discovery of botnets with 10-100 systems is a daily occurrence; 10,000 system botnets are found almost weekly; and one botnet with 100,000 hosts has even been found (according to Johannes Ullrich, CTO of the Inte ...
Lessons Learned from 30 Years of MINIX,
... MINIX, I was extremely sensitive to any bugs or flaws that turned up. All developers should try to use their own systems as early as feasible so they can see what users will experience. Lesson. Eat your own dog food. The microkernel was indeed small. Only the scheduler, low-level process management, ...
... MINIX, I was extremely sensitive to any bugs or flaws that turned up. All developers should try to use their own systems as early as feasible so they can see what users will experience. Lesson. Eat your own dog food. The microkernel was indeed small. Only the scheduler, low-level process management, ...
Processes - United International College
... • The Operating System must – Interleave the execution of multiple processes – Allocate resources to processes, and protect the resources of each process from other processes, – Enable processes to share and exchange information, – Enable synchronization among processes. ...
... • The Operating System must – Interleave the execution of multiple processes – Allocate resources to processes, and protect the resources of each process from other processes, – Enable processes to share and exchange information, – Enable synchronization among processes. ...
Junos Pulse Access Control Service
... the intrusion prevention system (IPS) capabilities of the SRX Series gateways for both data center and branch, as well as the standalone Juniper Networks IDP Series Intrusion Detection and Prevention Appliances, to deliver broad application traffic visibility—mitigating insider threats by isolating ...
... the intrusion prevention system (IPS) capabilities of the SRX Series gateways for both data center and branch, as well as the standalone Juniper Networks IDP Series Intrusion Detection and Prevention Appliances, to deliver broad application traffic visibility—mitigating insider threats by isolating ...
Chapter 1
... List of characteristics has expanded over time, but these three remain central Successful organization maintains multiple layers of security: ...
... List of characteristics has expanded over time, but these three remain central Successful organization maintains multiple layers of security: ...
Processes - UniMAP Portal
... A thread may migrate from one process environment to another. This allows a thread to be easily moved among ...
... A thread may migrate from one process environment to another. This allows a thread to be easily moved among ...
G2_Survey_SynchronizationTools
... • Mutual-exclusion guarantees that certain sections of code (critical sections) will not be executed by more than one process simultaneously. These sections of code usually access shared variables in a common store or access shared hardware. • The standard solution to kernel-level mutualexclusion in ...
... • Mutual-exclusion guarantees that certain sections of code (critical sections) will not be executed by more than one process simultaneously. These sections of code usually access shared variables in a common store or access shared hardware. • The standard solution to kernel-level mutualexclusion in ...
Certified Penetration Testing Specialist
... methodologies as utilized by our international group of vulnerability consultants. Mile2 trainers keep abreast of their expertise by practicing what they teach because we believe that an equal emphasis on theoretical and real world experience is essential for effective knowledge transfer to you, the ...
... methodologies as utilized by our international group of vulnerability consultants. Mile2 trainers keep abreast of their expertise by practicing what they teach because we believe that an equal emphasis on theoretical and real world experience is essential for effective knowledge transfer to you, the ...
Book 2.indb
... front-end. An embedded operating system in a device today is not so far removed as one might think from its ancestor of the 1950s. ...
... front-end. An embedded operating system in a device today is not so far removed as one might think from its ancestor of the 1950s. ...
conklin_4e_PPT_ch11
... • Rights define the actions a user can perform on the system itself. • Permissions control what the user is allowed to do with objects on the system. ...
... • Rights define the actions a user can perform on the system itself. • Permissions control what the user is allowed to do with objects on the system. ...
Operating System Support for Planetary-Scale Network Services
... course, well-established concepts. What is new in PlanetLab is distributed virtualization: the acquisition of a distributed set of VMs that are treated as a single, compound entity by the system. To support this concept, PlanetLab must provide facilities to create a slice, initialize it with suffici ...
... course, well-established concepts. What is new in PlanetLab is distributed virtualization: the acquisition of a distributed set of VMs that are treated as a single, compound entity by the system. To support this concept, PlanetLab must provide facilities to create a slice, initialize it with suffici ...
A survey of security issues in hardware virtualization
... Each single virtual machine, which comprises a stack made up from an operating system and its applications, defines a guest environment. All the guests are isolated from each other, while they use the same virtual platform provided by the hypervisor. The interface published by the physical platform ...
... Each single virtual machine, which comprises a stack made up from an operating system and its applications, defines a guest environment. All the guests are isolated from each other, while they use the same virtual platform provided by the hypervisor. The interface published by the physical platform ...
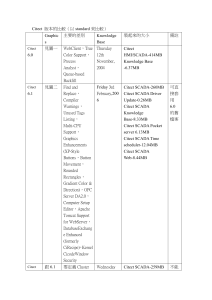
Integrate all your facilities systems with CitectFacilities V7.0
... CitectSCADA installation from that on which the project was backed up. It was also possible to generate different Object Identifiers from one CitectSCADA machine to ...
... CitectSCADA installation from that on which the project was backed up. It was also possible to generate different Object Identifiers from one CitectSCADA machine to ...
process
... • The Operating System must – Interleave the execution of multiple processes – Allocate resources to processes, and protect the resources of each process from other processes, – Enable processes to share and exchange information, – Enable synchronization among processes. ...
... • The Operating System must – Interleave the execution of multiple processes – Allocate resources to processes, and protect the resources of each process from other processes, – Enable processes to share and exchange information, – Enable synchronization among processes. ...
... Note: Since CompactPCI boards might be installed or removed from the backplane while the system is powered down, the configuration of each board might be different when the machine is then rebooted. This makes it essential that the device drivers in the system not store board configuration informati ...
Lecture 1 - Rabie A. Ramadan
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs. Concurrency by multiplexing the CPUs among the processes / threads. ...
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs. Concurrency by multiplexing the CPUs among the processes / threads. ...