HW2_wet
... As we seen, handling many processes in pseudo parallel way, may have many advantages, but it also comes with a cost. The kernel must keep track of the relevant data for many processes, and context switching itself is an operation that consumes a little resources. Thus, it makes sense, in case that w ...
... As we seen, handling many processes in pseudo parallel way, may have many advantages, but it also comes with a cost. The kernel must keep track of the relevant data for many processes, and context switching itself is an operation that consumes a little resources. Thus, it makes sense, in case that w ...
Scheduling - Ubiquitous Computing Lab
... • Scheduling: deciding which threads are given access to resources from moment to moment Operating Systems ...
... • Scheduling: deciding which threads are given access to resources from moment to moment Operating Systems ...
EECC722 - Shaaban
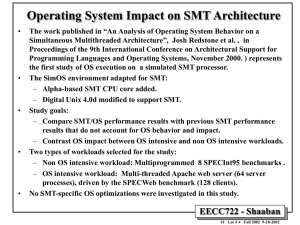
... • Results show that for SMT, omission of the operating system did not lead to a serious misprediction of performance for SPECInt, although the effects were more significant for a superscalar executing the same workload. • On the Apache workload, however, the operating system is responsible for the m ...
... • Results show that for SMT, omission of the operating system did not lead to a serious misprediction of performance for SPECInt, although the effects were more significant for a superscalar executing the same workload. • On the Apache workload, however, the operating system is responsible for the m ...
Sessuib 12 2012
... obligations concerning protection of information technology and assets. Provides a baseline to provide assurance for compliance with the policy. Provides a basis for determine what security tools to use to adequately protect information ...
... obligations concerning protection of information technology and assets. Provides a baseline to provide assurance for compliance with the policy. Provides a basis for determine what security tools to use to adequately protect information ...
Moodle-9 - Willingdon College, Sangli
... 3) Worst fit : This allocates to largest hole. This can be achieved by external fragmentation, files are broken into pieces. ...
... 3) Worst fit : This allocates to largest hole. This can be achieved by external fragmentation, files are broken into pieces. ...
Chapter3
... • Process Control Information – Scheduling and State Information This is information that is needed by the operating system to perform its scheduling function. Typical items of information: •Process state: defines the readiness of the process to be scheduled for execution (e.g., running, ready, wait ...
... • Process Control Information – Scheduling and State Information This is information that is needed by the operating system to perform its scheduling function. Typical items of information: •Process state: defines the readiness of the process to be scheduled for execution (e.g., running, ready, wait ...
OSPP: The Kernel Abstraction
... – Wake up other threads to do any real work – E.g., device driver runs as a kernel thread ...
... – Wake up other threads to do any real work – E.g., device driver runs as a kernel thread ...
TOTALVIEW CHANGE LOG - Rogue Wave Software
... FlexLM software has been upgraded to the latest FlexNet v11.12.1 version. This eliminates the need to work around the Flexera INCREMENT bug on most platforms. The platforms Linux-IA64, Linux Power, and AIX (RS6000) remain on FlexNet v11.11.1 either because v11.12.1 is not available or because of oth ...
... FlexLM software has been upgraded to the latest FlexNet v11.12.1 version. This eliminates the need to work around the Flexera INCREMENT bug on most platforms. The platforms Linux-IA64, Linux Power, and AIX (RS6000) remain on FlexNet v11.11.1 either because v11.12.1 is not available or because of oth ...
Security Policies, Standards, and Planning
... a. The policy should begin with a clear statement of purpose. The introductory section should outline the scope and applicability of the policy. b. What does this policy address? c. Who is responsible and accountable for policy implementation? d. What technologies and issues does the policy document ...
... a. The policy should begin with a clear statement of purpose. The introductory section should outline the scope and applicability of the policy. b. What does this policy address? c. Who is responsible and accountable for policy implementation? d. What technologies and issues does the policy document ...
VPN
... Secure Shell VPN - offers VPN tunneling to secure remote connections to a network or to internetwork links Microsoft Point-to-Point Encryption - works with the point-to-point protocol and in several ...
... Secure Shell VPN - offers VPN tunneling to secure remote connections to a network or to internetwork links Microsoft Point-to-Point Encryption - works with the point-to-point protocol and in several ...
z/VM Conversational Monitor System (CMS)
... Files are stored in file pools A user can be given an amount of file space in a pool The files in a file space are organized in directories A file can be placed in more than one directory ...
... Files are stored in file pools A user can be given an amount of file space in a pool The files in a file space are organized in directories A file can be placed in more than one directory ...
detection of peer to peer applications
... patterns and packets. Network scanning looks for common ports or protocols that may be open. These methods are useful for detecting P2P applications such as Piolet. Piolet is an executable which can be dropped and run from anywhere. It requires no installation and leaves no footprint behind. An admi ...
... patterns and packets. Network scanning looks for common ports or protocols that may be open. These methods are useful for detecting P2P applications such as Piolet. Piolet is an executable which can be dropped and run from anywhere. It requires no installation and leaves no footprint behind. An admi ...
CHAPTER 1 Concepts and Tools n this chapter, we`ll introduce the
... tab lists the top-level visible windows on all the desktops in the interactive window station you are connected to. (By default, there is only one interactive desktop—an application can create more by using the Windows CreateDesktop function, as is done by the Sysinternals Desktops tool.) The Status ...
... tab lists the top-level visible windows on all the desktops in the interactive window station you are connected to. (By default, there is only one interactive desktop—an application can create more by using the Windows CreateDesktop function, as is done by the Sysinternals Desktops tool.) The Status ...
File
... LDAP: Strengths, Weaknesses, and AD Integration Lightweight Directory Access Protocol (LDAP) is “a set of open protocols used to access centrally stored information over a network,” and “runs on a layer above the TCP/IP stack” (Red Hat, Inc., 2011) (Mcirosoft Corporation, 2011). The use of directory ...
... LDAP: Strengths, Weaknesses, and AD Integration Lightweight Directory Access Protocol (LDAP) is “a set of open protocols used to access centrally stored information over a network,” and “runs on a layer above the TCP/IP stack” (Red Hat, Inc., 2011) (Mcirosoft Corporation, 2011). The use of directory ...
the Mach kernel
... The kernel also must process pointers to out-of-line data, as a pointer to data in the sender’s address space would be invalid if the receiver’s -- especially if the sender and receiver reside on different systems! To make it more efficient, Mach will modify the address map of the receiving task ...
... The kernel also must process pointers to out-of-line data, as a pointer to data in the sender’s address space would be invalid if the receiver’s -- especially if the sender and receiver reside on different systems! To make it more efficient, Mach will modify the address map of the receiving task ...
lecture 14
... The main disadvantage of the semaphore discussed in the previous section is that they all require busy waiting. While a process is in its critical section, any other process that tries to enter its critical section must loop continuously in the entry code. This continual looping is clearly a problem ...
... The main disadvantage of the semaphore discussed in the previous section is that they all require busy waiting. While a process is in its critical section, any other process that tries to enter its critical section must loop continuously in the entry code. This continual looping is clearly a problem ...
Process Description and Control
... • The Operating System must – Interleave the execution of multiple processes – Allocate resources to processes, and protect the resources of each process from other processes, – Enable processes to share and exchange information, – Enable synchronization among processes. ...
... • The Operating System must – Interleave the execution of multiple processes – Allocate resources to processes, and protect the resources of each process from other processes, – Enable processes to share and exchange information, – Enable synchronization among processes. ...
Operating Systems (ECS 150) Spring 2011
... Each homework, project, examinations given points that define A, B, C, D for each activity. Final A, B, C, D computed by weighted average of these points Your final graded weighted in a similar manner Your final grade depends on where you fall.. ...
... Each homework, project, examinations given points that define A, B, C, D for each activity. Final A, B, C, D computed by weighted average of these points Your final graded weighted in a similar manner Your final grade depends on where you fall.. ...
Chapter 3 Process Description and Control
... • The Operating System must – Interleave the execution of multiple processes – Allocate resources to processes, and protect the resources of each process from other processes, – Enable processes to share and exchange information, – Enable synchronization among processes. ...
... • The Operating System must – Interleave the execution of multiple processes – Allocate resources to processes, and protect the resources of each process from other processes, – Enable processes to share and exchange information, – Enable synchronization among processes. ...
Before You Begin: Assign Information Classification
... The following are the most common file attributes: R - The file is read-only A - The file will be archived the next backup S - The file is marked as a system file and a warning is given if an attempt is made to delete or modify the file H - The file is hidden in the directory display ...
... The following are the most common file attributes: R - The file is read-only A - The file will be archived the next backup S - The file is marked as a system file and a warning is given if an attempt is made to delete or modify the file H - The file is hidden in the directory display ...
"Virtual Machines: The State of the Art"
... several virtualisation programs to select the one which is most suitable for secure on-demand cluster computing. His criteria are similar to ours. Nanda and Chiueh [12] discuss some implementation details for a large number of VMMs. Both focus more on specific implementations than on characteristics ...
... several virtualisation programs to select the one which is most suitable for secure on-demand cluster computing. His criteria are similar to ours. Nanda and Chiueh [12] discuss some implementation details for a large number of VMMs. Both focus more on specific implementations than on characteristics ...
Proceedings of BSDCon ’03 USENIX Association San Mateo, CA, USA September 8–12, 2003
... In this method, privileged instructions and their related non-privileged instructions in a native operating system are statically translated into subroutine calls that perform emulation. The translated instructions of the user-level OS are executed by both the real CPU and the partial emulator. This ...
... In this method, privileged instructions and their related non-privileged instructions in a native operating system are statically translated into subroutine calls that perform emulation. The translated instructions of the user-level OS are executed by both the real CPU and the partial emulator. This ...
Process
... Sharing of memory, files and other resources of the process to which the threads belong ...
... Sharing of memory, files and other resources of the process to which the threads belong ...
O ti S t O ti S t Operating Systems Chapter 1
... provides contextual application of theory, using examples of currently used operating system environments. ...
... provides contextual application of theory, using examples of currently used operating system environments. ...
System Software - USC Upstate: Faculty
... their older OS, and some conclude that they need to purchase a new computer altogether. One down fall to this is that it is often found that some of their existing application programs do not work as well with the new OS. System Software ...
... their older OS, and some conclude that they need to purchase a new computer altogether. One down fall to this is that it is often found that some of their existing application programs do not work as well with the new OS. System Software ...