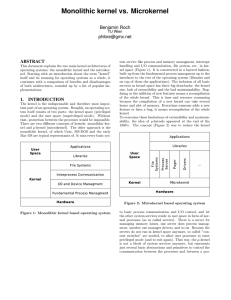
Monolithic kernel vs. Microkernel
... kernel. With the introduction of multitasking (and multithreading) new problems arised, concerning isolation of memory and processes. These problems include issues like race conditions, memory protection and system security itself. The kernel must be able to grant that in case a process cracks down, ...
... kernel. With the introduction of multitasking (and multithreading) new problems arised, concerning isolation of memory and processes. These problems include issues like race conditions, memory protection and system security itself. The kernel must be able to grant that in case a process cracks down, ...
The Guidelines on Cyber Security onboard Ships - ics
... Unlike other areas of safety and security where historic evidence is available and reporting of incidents is required, cyber security is made more challenging by the absence of any definitive information about the incidents and their impact. There are motives for organisations and individuals to exp ...
... Unlike other areas of safety and security where historic evidence is available and reporting of incidents is required, cyber security is made more challenging by the absence of any definitive information about the incidents and their impact. There are motives for organisations and individuals to exp ...
Linux+ Guide to Linux Certification Chapter Nine System Initialization
... • Boot loaders are typically loaded by the system BIOS from the MBR or the first sector of the active partition of a hard disk • The boot loader is responsible for loading the Linux kernel • The LILO boot loader uses the /etc/lilo.conf configuration file, whereas the GRUB boot loader uses the /boot/ ...
... • Boot loaders are typically loaded by the system BIOS from the MBR or the first sector of the active partition of a hard disk • The boot loader is responsible for loading the Linux kernel • The LILO boot loader uses the /etc/lilo.conf configuration file, whereas the GRUB boot loader uses the /boot/ ...
Ch 1 Getting Started with the Operating System
... Understanding Commands Internal commands: Built into command processor Automatically loaded/stored in ...
... Understanding Commands Internal commands: Built into command processor Automatically loaded/stored in ...
Federal Systems Level Guidance for Securing
... applications. Well, there are many choices. Should we go with a Windows system? The Microsoft (MS) platforms have great GUI interfaces and numerous applications, but patch after patch needs to be applied to keep attackers from exploiting vulnerabilities that are discovered each week. Well, we could ...
... applications. Well, there are many choices. Should we go with a Windows system? The Microsoft (MS) platforms have great GUI interfaces and numerous applications, but patch after patch needs to be applied to keep attackers from exploiting vulnerabilities that are discovered each week. Well, we could ...
VIII. Input/Output
... Common in large storage environments (and becoming more common) Multiple hosts attached to multiple storage arrays - flexible ...
... Common in large storage environments (and becoming more common) Multiple hosts attached to multiple storage arrays - flexible ...
VIII. Input/Output I/O Hardware
... Host-attached storage accessed through I/O ports talking to I/O busses ...
... Host-attached storage accessed through I/O ports talking to I/O busses ...
Introduction CS 239 Security for Networks and System
... • Data can only be decrypted successfully on that machine • Can also seal storage such that only a particular application can access it CS 236 Online ...
... • Data can only be decrypted successfully on that machine • Can also seal storage such that only a particular application can access it CS 236 Online ...
What is an Operating System? - Sekolah Tinggi Teknik Surabaya
... » Protection – any mechanism for controlling access of processes or users to resources defined by the OS » Security – defense of the system against internal and external attacks ˃ Huge range, including denial-of-service, worms, viruses, identity theft, theft of service ...
... » Protection – any mechanism for controlling access of processes or users to resources defined by the OS » Security – defense of the system against internal and external attacks ˃ Huge range, including denial-of-service, worms, viruses, identity theft, theft of service ...
Web Site Development Tools
... Virus Hoaxes • Some so-called viruses trumpeted in the media or announced via warning e-mails are just hoaxes • False warnings about viruses proliferate as quickly as real viruses • Creates an atmosphere in which a real virus warning might not be taken seriously • Several antivirus software vendors ...
... Virus Hoaxes • Some so-called viruses trumpeted in the media or announced via warning e-mails are just hoaxes • False warnings about viruses proliferate as quickly as real viruses • Creates an atmosphere in which a real virus warning might not be taken seriously • Several antivirus software vendors ...
ppt
... Page fault executes when memory access error System call executes via trap to trigger kernel to execute ...
... Page fault executes when memory access error System call executes via trap to trigger kernel to execute ...
Operating System
... frequently that the users may interact with each program while it is running. Time-sharing systems were developed to provide interactive use of a computer system at a reasonable cost. A time-shared operating system uses CPU scheduling and multiprogramming to provide each user with a small portion of ...
... frequently that the users may interact with each program while it is running. Time-sharing systems were developed to provide interactive use of a computer system at a reasonable cost. A time-shared operating system uses CPU scheduling and multiprogramming to provide each user with a small portion of ...
What is an Operating System?
... (the overlapping of output of one job with input of other jobs) ...
... (the overlapping of output of one job with input of other jobs) ...
Lecture 1: Course Introduction and Overview
... History, Functionality, Stupidity, Bugs, Management CS152 Machine interface CS160 Human interface CS169 Software engineering/management ...
... History, Functionality, Stupidity, Bugs, Management CS152 Machine interface CS160 Human interface CS169 Software engineering/management ...
Processes
... – Create and initialize the process control block (PCB) in the kernel – Create a new address space – Initialize the address space with a copy of the entire contents of the address space of the parent – Inherit the execution context of the parent (e.g., any open files) – Inform the scheduler that the ...
... – Create and initialize the process control block (PCB) in the kernel – Create a new address space – Initialize the address space with a copy of the entire contents of the address space of the parent – Inherit the execution context of the parent (e.g., any open files) – Inform the scheduler that the ...
Introduction - McMaster Computing and Software
... Security – defense of the system against internal and external attacks Huge range of attacks: denial-of-service, worms, viruses, identity theft, theft of service Systems generally first distinguish among users, to determine who can do what User identities (user IDs, security IDs) include nam ...
... Security – defense of the system against internal and external attacks Huge range of attacks: denial-of-service, worms, viruses, identity theft, theft of service Systems generally first distinguish among users, to determine who can do what User identities (user IDs, security IDs) include nam ...
資工系網媒所NEWS實驗室Chapter 13
... separate module of the operating system, allowing it to be replaced with a different algorithm if necessary. Either SSTF or LOOK is a reasonable choice for the default algorithm. 資工系網媒所 NEWS實驗室 ...
... separate module of the operating system, allowing it to be replaced with a different algorithm if necessary. Either SSTF or LOOK is a reasonable choice for the default algorithm. 資工系網媒所 NEWS實驗室 ...
CS540_Ch19
... ◦ Features found in a desktop PC require more substantial hardware that what is typically unavailable in a real-time system due to lack of memory and fast processors. Both of these are unavailable in real time systems due to space constraints. Addition to that many systems lack sufficient space ...
... ◦ Features found in a desktop PC require more substantial hardware that what is typically unavailable in a real-time system due to lack of memory and fast processors. Both of these are unavailable in real time systems due to space constraints. Addition to that many systems lack sufficient space ...
Chapter 19 Real
... desktop system as above. Reasons include ◦ Real-time systems are typically single-purpose ◦ Real-time systems often do not require interfacing with a user ◦ Features found in a desktop PC require more substantial hardware that what is typically unavailable in a real-time system due to lack of memo ...
... desktop system as above. Reasons include ◦ Real-time systems are typically single-purpose ◦ Real-time systems often do not require interfacing with a user ◦ Features found in a desktop PC require more substantial hardware that what is typically unavailable in a real-time system due to lack of memo ...
SUSE Linux Enterprise Server 10 SP1 EAL4 High-Level Design Version 1.2.1
... This document is provided “AS IS” with no express or implied warranties. Use the information in this document at your own risk. This document may be reproduced or distributed in any form without prior permission provided the copyright notice is retained on all copies. Modified versions of this docum ...
... This document is provided “AS IS” with no express or implied warranties. Use the information in this document at your own risk. This document may be reproduced or distributed in any form without prior permission provided the copyright notice is retained on all copies. Modified versions of this docum ...
Abstract View of System Components
... • A (traditional/ heavyweight) process has a single thread (of control). • Modern operating systems allow a process to contain multiple threads of control. • Each thread, is defined by its thread ID, program counter, register set & stack (for temporary data). • A thread shares with other threads of ...
... • A (traditional/ heavyweight) process has a single thread (of control). • Modern operating systems allow a process to contain multiple threads of control. • Each thread, is defined by its thread ID, program counter, register set & stack (for temporary data). • A thread shares with other threads of ...
VMware GSX Server - Boston Tech Partners
... • Provision Servers Rapidly. Pre-configured virtual machine servers can be built once quickly and deployed anywhere immediately; provisioning a new server is as easy as copying a file, or just PXE boot a new virtual machine to download a system image. ...
... • Provision Servers Rapidly. Pre-configured virtual machine servers can be built once quickly and deployed anywhere immediately; provisioning a new server is as easy as copying a file, or just PXE boot a new virtual machine to download a system image. ...
Guidelines on Cyber Security onboard ships
... Unlike other areas of safety and security where historic evidence is available and reporting of incidents is required, cyber security is made more challenging by the absence of any definitive information about the incidents and their impact. There are motives for organisations and individuals to exp ...
... Unlike other areas of safety and security where historic evidence is available and reporting of incidents is required, cyber security is made more challenging by the absence of any definitive information about the incidents and their impact. There are motives for organisations and individuals to exp ...