Notes by Guydosh on Thread managment
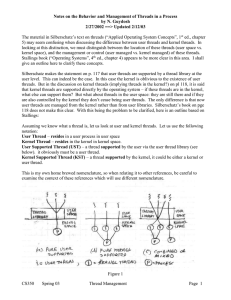
... 5) may seem confusing when discussing the difference between user threads and kernel threads. In looking at this distinction, we must distinguish between the location of these threads (user space vs. kernel space), and the management or control (user managed vs. kernel managed) of these threads. Sta ...
... 5) may seem confusing when discussing the difference between user threads and kernel threads. In looking at this distinction, we must distinguish between the location of these threads (user space vs. kernel space), and the management or control (user managed vs. kernel managed) of these threads. Sta ...
Click for PDF - Cyber Security Services
... using Java for business purposes while minimising their risk. 12. The newly introduced mitigation strategy #6 ‘Automated dynamic analysis’ extracts the behavioural analysis functionality from the existing two mitigation strategies ‘Email content filtering’ and ‘Web content filtering’. A ...
... using Java for business purposes while minimising their risk. 12. The newly introduced mitigation strategy #6 ‘Automated dynamic analysis’ extracts the behavioural analysis functionality from the existing two mitigation strategies ‘Email content filtering’ and ‘Web content filtering’. A ...
module_23
... Mutual exclusion: only one process at a time can use a resource. Hold and wait: a process holding at least one resource is waiting to acquire additional resources held by other processes. No preemption: a resource can be released only voluntarily by the process holding it, after that process has com ...
... Mutual exclusion: only one process at a time can use a resource. Hold and wait: a process holding at least one resource is waiting to acquire additional resources held by other processes. No preemption: a resource can be released only voluntarily by the process holding it, after that process has com ...
OS course notes - CS
... where we have used a 3-D perspective to show that there is one hardware base, one operating system, but many applications. It also shows the important interfaces: applications can execute only non-privileged machine instructions, and they may also call upon the operating system to perform some servi ...
... where we have used a 3-D perspective to show that there is one hardware base, one operating system, but many applications. It also shows the important interfaces: applications can execute only non-privileged machine instructions, and they may also call upon the operating system to perform some servi ...
Hands-On Ethical Hacking and Network Security
... Kerberos is used on LANs for authentication Uses Tickets and Keys Used by Windows 2000, XP, and 2003 Server by default Not common on WLANS (I think) ...
... Kerberos is used on LANs for authentication Uses Tickets and Keys Used by Windows 2000, XP, and 2003 Server by default Not common on WLANS (I think) ...
What is an Operating System?
... Process needs resources to accomplish its task CPU, memory, I/O, files (received upon creation and along execution) Initialization data (e.g., a process for presenting the status of a file) Process termination requires reclaim of any reusable resources ...
... Process needs resources to accomplish its task CPU, memory, I/O, files (received upon creation and along execution) Initialization data (e.g., a process for presenting the status of a file) Process termination requires reclaim of any reusable resources ...
View
... registers to determine what action to take. For example, if it finds a read request, the controller will start the transfer of data from the device to its local butter. Once the transfer of data is complete, the device controller informs the CPU that it has finished its operation. It accomplishes th ...
... registers to determine what action to take. For example, if it finds a read request, the controller will start the transfer of data from the device to its local butter. Once the transfer of data is complete, the device controller informs the CPU that it has finished its operation. It accomplishes th ...
faculty.elgin.edu
... • A phishing filter has also been added • Prevents unauthorized Web sites from stealing log-on credentials and other personal information ...
... • A phishing filter has also been added • Prevents unauthorized Web sites from stealing log-on credentials and other personal information ...
2-OS
... • Discussion points – 64-bit processing is faster than 32-bit processing – 64-bit OS requires that device drivers operating in kernel mode be 64-bit drivers – Application is compiled to process 64 bits or 32 bits – 32-bit OS can only address up to 4 GB of memory – Benefit from 64-bit computing if: • ...
... • Discussion points – 64-bit processing is faster than 32-bit processing – 64-bit OS requires that device drivers operating in kernel mode be 64-bit drivers – Application is compiled to process 64 bits or 32 bits – 32-bit OS can only address up to 4 GB of memory – Benefit from 64-bit computing if: • ...
Using an expanded cyber kill chain model to increase
... • Understanding the Stages of a Sophisticated Attack • Using the Expanded Model to Build a Resilient Enterprise ...
... • Understanding the Stages of a Sophisticated Attack • Using the Expanded Model to Build a Resilient Enterprise ...
thread - Lyle School of Engineering
... suspending all threads of the process since all threads share the same address space Termination of a process, terminates all threads within the process ...
... suspending all threads of the process since all threads share the same address space Termination of a process, terminates all threads within the process ...
CompTIA Security (SY0-401)
... Risks associated with Cloud Computing and Virtualization Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
... Risks associated with Cloud Computing and Virtualization Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
PC Software and Hardware Essential Curriculum
... 15.1 Identify potential safety hazards and implement proper safety procedures related to networks 15.2 Design a network based on the customer's needs 15.3 Determine the components for your customer's network 15.4 Implement the customer's network 15.5 Upgrade the customer's network 15.6 Describe inst ...
... 15.1 Identify potential safety hazards and implement proper safety procedures related to networks 15.2 Design a network based on the customer's needs 15.3 Determine the components for your customer's network 15.4 Implement the customer's network 15.5 Upgrade the customer's network 15.6 Describe inst ...
Processes
... • Threads provide a mechanism that allows sequential processes to make blocking system calls while also achieving parallelism. ...
... • Threads provide a mechanism that allows sequential processes to make blocking system calls while also achieving parallelism. ...
DeadLocks
... Sequence is safe if for each Pi, the resources
that Pi can still request can be satisfied by currently available
resources + resources held by all the Pj, with j
... Sequence
Lecture 5 Processes
... – Kernel assigns/allocates virtual processors (kernel threads)to each process – ”signals” upcalls to run-time system upon blocking and unblocking of (user ...
... – Kernel assigns/allocates virtual processors (kernel threads)to each process – ”signals” upcalls to run-time system upon blocking and unblocking of (user ...
Process Sync
... Producer / Consumer Problem Shared data: int counter, in , out item buffer[n]; ...
... Producer / Consumer Problem Shared data: int counter, in , out item buffer[n]; ...
What is an Operating System?
... “The one program running at all times on the computer” is the kernel. Everything else is either a system program (ships with the operating system) or an application program ...
... “The one program running at all times on the computer” is the kernel. Everything else is either a system program (ships with the operating system) or an application program ...
Chapter 4
... uses icons and menus displayed on screen to send commands to the computer system • Time-sharing: allows more than one person to use a computer system at the same time • Proprietary software: one-of-a-kind program for a specific application, usually developed and owned by a single company • Off-the-s ...
... uses icons and menus displayed on screen to send commands to the computer system • Time-sharing: allows more than one person to use a computer system at the same time • Proprietary software: one-of-a-kind program for a specific application, usually developed and owned by a single company • Off-the-s ...
Chapter 4 - leons group of colleges
... uses icons and menus displayed on screen to send commands to the computer system • Time-sharing: allows more than one person to use a computer system at the same time • Proprietary software: one-of-a-kind program for a specific application, usually developed and owned by a single company • Off-the-s ...
... uses icons and menus displayed on screen to send commands to the computer system • Time-sharing: allows more than one person to use a computer system at the same time • Proprietary software: one-of-a-kind program for a specific application, usually developed and owned by a single company • Off-the-s ...
Preserving Computing`s Past: Restoration and Simulation
... interest. In computer restoration, historical systems are returned to working condition through repair of broken electrical and mechanical subsystems, if necessary substituting current parts for the original ones. In computer simulation, historical systems are re-created as software programs on curr ...
... interest. In computer restoration, historical systems are returned to working condition through repair of broken electrical and mechanical subsystems, if necessary substituting current parts for the original ones. In computer simulation, historical systems are re-created as software programs on curr ...
message
... Unbounded-buffer places no practical limit on the size of the buffer. Consumer may wait, producer never waits. Bounded-buffer assumes that there is a fixed buffer size. Consumer waits for new item, producer waits if buffer is full. ...
... Unbounded-buffer places no practical limit on the size of the buffer. Consumer may wait, producer never waits. Bounded-buffer assumes that there is a fixed buffer size. Consumer waits for new item, producer waits if buffer is full. ...
Module 4: Processes
... Most systems now a days allow more than one process called Multiprogramming Systems. In case of uni-programming you don’t need to store information about the process as much as you would need to store information about a process being executed in multiprogramming system. ...
... Most systems now a days allow more than one process called Multiprogramming Systems. In case of uni-programming you don’t need to store information about the process as much as you would need to store information about a process being executed in multiprogramming system. ...
Operating Systems 2014/2015 Part VII – Storage Devices
... scheduling algorithms in the controller hardware (OS just needs to send batch of requests to the controller, the controller then queues and schedules them to improve both the seek time and the rotational latency) ...
... scheduling algorithms in the controller hardware (OS just needs to send batch of requests to the controller, the controller then queues and schedules them to improve both the seek time and the rotational latency) ...