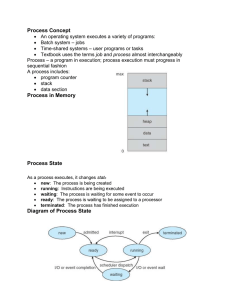
Process State
... A link is associated with exactly one pair of communicating processes Between each pair there exists exactly one link The link may be unidirectional, but is usually bi-directional ...
... A link is associated with exactly one pair of communicating processes Between each pair there exists exactly one link The link may be unidirectional, but is usually bi-directional ...
ioChap05-week13 - Rensselaer Polytechnic Institute
... Operating Systems: A Modern Perspective, Chapter 5 ...
... Operating Systems: A Modern Perspective, Chapter 5 ...
Project proposal
... …coding your own Bluetooth stack? Because you get the complete stack (with the hardware you bought), you have no other choice than to use the profiles it has exposed (most commonly used profile is Serial port profile) as virtual COM ports. This results in a limited functionality, and inability to ex ...
... …coding your own Bluetooth stack? Because you get the complete stack (with the hardware you bought), you have no other choice than to use the profiles it has exposed (most commonly used profile is Serial port profile) as virtual COM ports. This results in a limited functionality, and inability to ex ...
Safe & Secure Environment for Students
... the most of its computing technology – while receiving only appropriate Internet content – Previous filtering solution provided inadequate integration with user directories, ...
... the most of its computing technology – while receiving only appropriate Internet content – Previous filtering solution provided inadequate integration with user directories, ...
Network Security
... we also want to prevent our inside people from spoofing to a different IP address as well. The only range that is allowed to transmit is my internal network, in this case 192.168.1.0 /24 Router (config)# access-list 105 permit ip 192.168.1.0 0.0.0.255 any Router(config)# access-list 105 deny ip any ...
... we also want to prevent our inside people from spoofing to a different IP address as well. The only range that is allowed to transmit is my internal network, in this case 192.168.1.0 /24 Router (config)# access-list 105 permit ip 192.168.1.0 0.0.0.255 any Router(config)# access-list 105 deny ip any ...
Chapter 4
... Job handled based on length of CPU cycle time Easy implementation in batch environment – CPU time requirement known in advance ...
... Job handled based on length of CPU cycle time Easy implementation in batch environment – CPU time requirement known in advance ...
Week 3 Chapter 04
... • The first DC configured in a forest becomes the global catalog server • The global catalog server enables forest-wide searches of data Hands-On Microsoft Windows Server 2008 ...
... • The first DC configured in a forest becomes the global catalog server • The global catalog server enables forest-wide searches of data Hands-On Microsoft Windows Server 2008 ...
SG 17 is
... (i.e. laws cannot keep up with the pace of technological change), and, since attacks are often transnational, national laws may well be inapplicable anyway. What this means is that the defenses must be largely technical, procedural and administrative; i.e. those that can be addressed in standards. ...
... (i.e. laws cannot keep up with the pace of technological change), and, since attacks are often transnational, national laws may well be inapplicable anyway. What this means is that the defenses must be largely technical, procedural and administrative; i.e. those that can be addressed in standards. ...
Homework Assignment 1 Practice the following questions based on
... perform an action (for example, read data from a database); in response, the server executes the action and sends back results to the client. The file-server system provides a file-system interface where clients can create, update, read, and delete files. An example of such a system is a Web server ...
... perform an action (for example, read data from a database); in response, the server executes the action and sends back results to the client. The file-server system provides a file-system interface where clients can create, update, read, and delete files. An example of such a system is a Web server ...
CompTIA Network + - We Provide Solutions
... Firewall - Firewall servers can be hardware or software based. They protect an organization’s internal network and servers from outside penetration. They secure the organization from the internet and typically scan incoming and outgoing data traffic. Firewall security can be configured in any numb ...
... Firewall - Firewall servers can be hardware or software based. They protect an organization’s internal network and servers from outside penetration. They secure the organization from the internet and typically scan incoming and outgoing data traffic. Firewall security can be configured in any numb ...
Firewall configuration tools
... ENABLE PING • BY DEFAULT, UFW ALLOWS PING REQUESTS. • IN ORDER TO DISABLE PING (ICMP) REQUESTS, YOU NEED TO EDIT /ETC/UFW/BEFORE.RULES AND REMOVE THE FOLLOWING LINES: # OK ICMP CODES -A UFW-BEFORE-INPUT -P ICMP --ICMP-TYPE DESTINATION-UNREACHABLE -J ACCEPT ...
... ENABLE PING • BY DEFAULT, UFW ALLOWS PING REQUESTS. • IN ORDER TO DISABLE PING (ICMP) REQUESTS, YOU NEED TO EDIT /ETC/UFW/BEFORE.RULES AND REMOVE THE FOLLOWING LINES: # OK ICMP CODES -A UFW-BEFORE-INPUT -P ICMP --ICMP-TYPE DESTINATION-UNREACHABLE -J ACCEPT ...
Advanced Operating Systems
... Systems what the goal of their resource management decisions should be Applications should be given as much control ...
... Systems what the goal of their resource management decisions should be Applications should be given as much control ...
Red Hat Enterprise Linux 4 Update 1 EAL4 High Level Design
... of International Business Machines Corporation in the United States, other countries, or both. Linux is a registered trademark of Linus Torvalds. UNIX is a registered trademark of The Open Group in the United States and other countries. Intel and Pentium are trademarks of Intel Corporation in the Un ...
... of International Business Machines Corporation in the United States, other countries, or both. Linux is a registered trademark of Linus Torvalds. UNIX is a registered trademark of The Open Group in the United States and other countries. Intel and Pentium are trademarks of Intel Corporation in the Un ...
P - Bilkent University Computer Engineering Department
... immediately. In this way, that process will not block. Will be able to run and complete. • Then, the same thing will be applicable to the process that is holding the next highest numbered resource. That will be able to run an finish. • All process may run and finish sooner or later. ...
... immediately. In this way, that process will not block. Will be able to run and complete. • Then, the same thing will be applicable to the process that is holding the next highest numbered resource. That will be able to run an finish. • All process may run and finish sooner or later. ...
An Overview of the Intel TFLOPS Supercomputer
... machine, the system hardware and software, and how the system is used by both programmers and the end-users. The level of detail varies. When a topic is addressed elsewhere, it is discussed only briefly in this paper. For example, we say very little about SPS. When a topic is not discussed elsewhere ...
... machine, the system hardware and software, and how the system is used by both programmers and the end-users. The level of detail varies. When a topic is addressed elsewhere, it is discussed only briefly in this paper. For example, we say very little about SPS. When a topic is not discussed elsewhere ...
ch13
... The I/O transfer has to use more than one (address, length) pair for that transfer to scatter the data around memory The same applies on output, where it has to be gathered from different physical pages ...
... The I/O transfer has to use more than one (address, length) pair for that transfer to scatter the data around memory The same applies on output, where it has to be gathered from different physical pages ...
A Survey on Virtualization Technologies
... VM was a fully protected and isolated copy of the underlying system. Users could execute, develop, and test applications without ever having to fear causing a crash to systems used by other users on the same computer. Virtualization was thus used to reduce the hardware acquisition cost and improvin ...
... VM was a fully protected and isolated copy of the underlying system. Users could execute, develop, and test applications without ever having to fear causing a crash to systems used by other users on the same computer. Virtualization was thus used to reduce the hardware acquisition cost and improvin ...
Computers and Operating Systems - Ms. Wade`s Page
... Personal or desktop operating systems are installed on a single computer and are called single-user operating systems because one user interacts with the operating system at a time. They are multitasking operating systems, which means they let you work with more than one program at a time. The three ...
... Personal or desktop operating systems are installed on a single computer and are called single-user operating systems because one user interacts with the operating system at a time. They are multitasking operating systems, which means they let you work with more than one program at a time. The three ...
process
... • The Operating System must – Interleave the execution of multiple processes – Allocate resources to processes, and protect the resources of each process from other processes, – Enable processes to share and exchange information, – Enable synchronization among processes. ...
... • The Operating System must – Interleave the execution of multiple processes – Allocate resources to processes, and protect the resources of each process from other processes, – Enable processes to share and exchange information, – Enable synchronization among processes. ...
Process Migration in Distributed Systems
... system architectures. In this section, we divide the levels/systems into four categories and examine the corresponding design choices. 1. UNIX-like Kernel[1]. As naming and location transparencies are not fully supported in UNIX, transparent process migration requires significant modification to the ...
... system architectures. In this section, we divide the levels/systems into four categories and examine the corresponding design choices. 1. UNIX-like Kernel[1]. As naming and location transparencies are not fully supported in UNIX, transparent process migration requires significant modification to the ...
Processes - EECG Toronto
... • What happens if you run “exec csh” in your shell? • What happens if you run “exec ls” in your shell? Try it. • fork() can return an error. Why might this happen? • Cannot create child process (return to parent). ...
... • What happens if you run “exec csh” in your shell? • What happens if you run “exec ls” in your shell? Try it. • fork() can return an error. Why might this happen? • Cannot create child process (return to parent). ...
WOSI-CRK-Description
... kernel components. Also reviewed are Windows’ fundamental design attributes, such as preemptive multitasking, symmetric multiprocessing, support for multiple hardware architectures (32-bit and 64-bit), security, integrated networking, etc. Windows is similar to most UNIX systems in that it is a mono ...
... kernel components. Also reviewed are Windows’ fundamental design attributes, such as preemptive multitasking, symmetric multiprocessing, support for multiple hardware architectures (32-bit and 64-bit), security, integrated networking, etc. Windows is similar to most UNIX systems in that it is a mono ...
PDF - IBM Redbooks
... IPS solutions use pattern matching to detect the signatures of specific techniques. This approach does not keep up to date with the evolution of current techniques and can also lead to a high rate of incorrect detection of attacks. Additionally, pattern matching engines require a unique signature fo ...
... IPS solutions use pattern matching to detect the signatures of specific techniques. This approach does not keep up to date with the evolution of current techniques and can also lead to a high rate of incorrect detection of attacks. Additionally, pattern matching engines require a unique signature fo ...