L11-thread-impl
... – Thread history isn’t taken into account by scheduler – Threads are co-‐opera(ve, not compe,,ve ...
... – Thread history isn’t taken into account by scheduler – Threads are co-‐opera(ve, not compe,,ve ...
Era of Spybots - A Secure Design Solution Using
... All workstation traffic is unrestricted between their ...
... All workstation traffic is unrestricted between their ...
FreeBSD for the Linux user
... • FreeBSD consists of all the components needed for a complete operating system ...
... • FreeBSD consists of all the components needed for a complete operating system ...
I/O Systems & Mass-Storage Structure
... Requests for disk service can be influenced by the fileallocation method. The disk-scheduling algorithm should be written as a separate module of the operating system, allowing it to be replaced with a different algorithm if necessary. Either SSTF or LOOK is a reasonable choice for the default algor ...
... Requests for disk service can be influenced by the fileallocation method. The disk-scheduling algorithm should be written as a separate module of the operating system, allowing it to be replaced with a different algorithm if necessary. Either SSTF or LOOK is a reasonable choice for the default algor ...
Networks and Operating Systems (252-0062
... Linux Air Disgruntled employees of all the other OS airlines decide to start their own airline. They build the planes, ticket counters, and pave the runways themselves. They charge a small fee to cover the cost of printing the ticket, but you can also download and print the ticket yourself. When you ...
... Linux Air Disgruntled employees of all the other OS airlines decide to start their own airline. They build the planes, ticket counters, and pave the runways themselves. They charge a small fee to cover the cost of printing the ticket, but you can also download and print the ticket yourself. When you ...
Input/Output
... smaller than or equal to A. If no such row exists, the system will eventually deadlock since no process can run to completion. Assume the process of the row chosen requests all the resources it needs (which is guaranteed to be possible) and finishes. Mark that process as terminated and add all its r ...
... smaller than or equal to A. If no such row exists, the system will eventually deadlock since no process can run to completion. Assume the process of the row chosen requests all the resources it needs (which is guaranteed to be possible) and finishes. Mark that process as terminated and add all its r ...
Information & Communication Technology System Maintenance Government of India
... Maintaining and repairing equipment / peripherals. Troubleshooting different computer issues Determining and installing appropriate security measures Installing & Configuring advanced computer networks Providing technical support on-site or via phone or email Install, configure, and maintain common ...
... Maintaining and repairing equipment / peripherals. Troubleshooting different computer issues Determining and installing appropriate security measures Installing & Configuring advanced computer networks Providing technical support on-site or via phone or email Install, configure, and maintain common ...
Developing Interfaces and Interactivity for DSpace with
... – No, but.... – Basic understanding will help diagnose problems – Many skill levels represented here • Some really NEED this knowledge (and may already have it) • Will help others UNDERSTAND their tech people ...
... – No, but.... – Basic understanding will help diagnose problems – Many skill levels represented here • Some really NEED this knowledge (and may already have it) • Will help others UNDERSTAND their tech people ...
ppt
... Network OS's (e.g. Mach, modern UNIX, Windows NT) – do the same but they also support a wide range of communication standards and enable remote processes to access (some) local resources (e.g. files). ...
... Network OS's (e.g. Mach, modern UNIX, Windows NT) – do the same but they also support a wide range of communication standards and enable remote processes to access (some) local resources (e.g. files). ...
Input/Output - UWC Computer Science
... smaller than or equal to A. If no such row exists, the system will eventually deadlock since no process can run to completion. Assume the process of the row chosen requests all the resources it needs (which is guaranteed to be possible) and finishes. Mark that process as terminated and add all its r ...
... smaller than or equal to A. If no such row exists, the system will eventually deadlock since no process can run to completion. Assume the process of the row chosen requests all the resources it needs (which is guaranteed to be possible) and finishes. Mark that process as terminated and add all its r ...
Xen and the Art of Virtualization
... Notwithstanding the intricacies of the x86, there are other arguments against full virtualization. In particular, there are situations in which it is desirable for the hosted operating systems to see real as well as virtual resources: providing both real and virtual time allows a guest OS to better ...
... Notwithstanding the intricacies of the x86, there are other arguments against full virtualization. In particular, there are situations in which it is desirable for the hosted operating systems to see real as well as virtual resources: providing both real and virtual time allows a guest OS to better ...
Xen and the Art of Virtualization
... Notwithstanding the intricacies of the x86, there are other arguments against full virtualization. In particular, there are situations in which it is desirable for the hosted operating systems to see real as well as virtual resources: providing both real and virtual time allows a guest OS to better ...
... Notwithstanding the intricacies of the x86, there are other arguments against full virtualization. In particular, there are situations in which it is desirable for the hosted operating systems to see real as well as virtual resources: providing both real and virtual time allows a guest OS to better ...
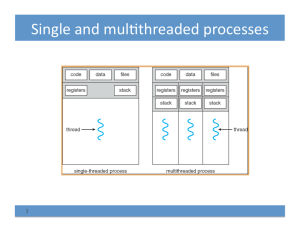
COS 318: Operating Systems Implementing Threads
... User-level thread package implements thread context switches OS doesn’t know the process has multiple threads Timer interrupt (signal facility) can introduce preemption When a user-level thread is blocked on an I/O event, the whole process is blocked Allows user-level code to build custom schedulers ...
... User-level thread package implements thread context switches OS doesn’t know the process has multiple threads Timer interrupt (signal facility) can introduce preemption When a user-level thread is blocked on an I/O event, the whole process is blocked Allows user-level code to build custom schedulers ...
Lecture 1 - The Laboratory for Advanced Systems Research
... Academic Honesty and the Internet • You might be able to find existing answers to some of the assignments on line • Remember, if you can find it, so can we – And we have, before ...
... Academic Honesty and the Internet • You might be able to find existing answers to some of the assignments on line • Remember, if you can find it, so can we – And we have, before ...
Configuring Input and Output Devices_PPT_ch06
... combines Red Hat hardware, software, and plug-in compatibility information into a single publication – For Mac OS X, use Apple Macintosh hardware such as the iMac to ensure compatibility ...
... combines Red Hat hardware, software, and plug-in compatibility information into a single publication – For Mac OS X, use Apple Macintosh hardware such as the iMac to ensure compatibility ...
Grid Operating System: Making Dynamic Virtual Services in
... applications, hosts, etc., in fact anything that requires protection) there will be a policy specifying who can access it and what they can do with it. In the case of a resource such as a file, the who could be a list of individuals and/or VOs, and the what could be read, write or execute actions si ...
... applications, hosts, etc., in fact anything that requires protection) there will be a policy specifying who can access it and what they can do with it. In the case of a resource such as a file, the who could be a list of individuals and/or VOs, and the what could be read, write or execute actions si ...
Slides
... • Justification for including signals was for the OS to inform a user process of an event ...
... • Justification for including signals was for the OS to inform a user process of an event ...
Installation Quick Start Guide
... software for Windows that you might already have on your computer include Nero Burning ROM and Roxio Creator. If you use a Windows operating system on your computer and do not have disc burning software installed (or you are not sure that the software can burn discs from image files) InfraRecorder i ...
... software for Windows that you might already have on your computer include Nero Burning ROM and Roxio Creator. If you use a Windows operating system on your computer and do not have disc burning software installed (or you are not sure that the software can burn discs from image files) InfraRecorder i ...
Security+ Guide to Network Security Fundamentals, Third Edition
... Limiting • Limiting access to information reduces the threat against it • Only those who must use data should have access to it – In addition, the amount of access granted to someone should be limited to what that person needs to know ...
... Limiting • Limiting access to information reduces the threat against it • Only those who must use data should have access to it – In addition, the amount of access granted to someone should be limited to what that person needs to know ...
PPT_ch01 - Mercer University Computer Science Department
... Limiting • Limiting access to information reduces the threat against it • Only those who must use data should have access to it – In addition, the amount of access granted to someone should be limited to what that person needs to know ...
... Limiting • Limiting access to information reduces the threat against it • Only those who must use data should have access to it – In addition, the amount of access granted to someone should be limited to what that person needs to know ...
I/O Speculation for the Microsecond Era
... example, branch predictors resolve branches before the branch path has been calculated [15]. Optimistic concurrency control in database systems enables multiple transactions to proceed before conflicts are resolved [5]. Prefetching systems attempt to make data available before it is known to be need ...
... example, branch predictors resolve branches before the branch path has been calculated [15]. Optimistic concurrency control in database systems enables multiple transactions to proceed before conflicts are resolved [5]. Prefetching systems attempt to make data available before it is known to be need ...
xv6 - PDOS-MIT
... and to provide a more useful set of services than the hardware alone supports. The operating system manages and abstracts the low-level hardware, so that, for example, a word processor need not concern itself with which type of disk hardware is being used. It also multiplexes the hardware, allowing ...
... and to provide a more useful set of services than the hardware alone supports. The operating system manages and abstracts the low-level hardware, so that, for example, a word processor need not concern itself with which type of disk hardware is being used. It also multiplexes the hardware, allowing ...