Chapter 3: Processes
... To explore interprocess communication using shared memory and message passing" ...
... To explore interprocess communication using shared memory and message passing" ...
Chapter 3 - reduced
... Context of a process represented in the PCB Context-switch time is overhead; the system does no useful ...
... Context of a process represented in the PCB Context-switch time is overhead; the system does no useful ...
CS153: Lecture 3
... Creates and initializes a new PCB Creates a new address space Initializes the address space with a copy of the entire contents of the address space of the parent Initializes the kernel resources to point to the resources used by parent (e.g., open files) Places the PCB on the ready queue ...
... Creates and initializes a new PCB Creates a new address space Initializes the address space with a copy of the entire contents of the address space of the parent Initializes the kernel resources to point to the resources used by parent (e.g., open files) Places the PCB on the ready queue ...
threads
... Thread creation is done through clone() system call Linux’s trick Store process information in separate structures and use pointers to point to them instead of storing it directly in the data structure for the process Clone() allows a child task to share the address space of ...
... Thread creation is done through clone() system call Linux’s trick Store process information in separate structures and use pointers to point to them instead of storing it directly in the data structure for the process Clone() allows a child task to share the address space of ...
Socket Programming
... the BSD Unix file access mechanism (open-readwrite-close) that provides an end-point for communication. ...
... the BSD Unix file access mechanism (open-readwrite-close) that provides an end-point for communication. ...
Programming with TCP/IP
... the BSD Unix file access mechanism (open-readwrite-close) that provides an end-point for communication. ...
... the BSD Unix file access mechanism (open-readwrite-close) that provides an end-point for communication. ...
Tenable Malware Detection
... Vulnerabilities are rapidly exploited in organizations that do not keep up with the software updates provided by software vendors, particular operating system web facing application vulnerabilities. SCCV scans hosts for their patch status and can alert administrators if there are systems in the envi ...
... Vulnerabilities are rapidly exploited in organizations that do not keep up with the software updates provided by software vendors, particular operating system web facing application vulnerabilities. SCCV scans hosts for their patch status and can alert administrators if there are systems in the envi ...
Porting OSE Systems to Linux
... that require multitasking, networking or have similar relatively advanced features, it is more often than not easier to use an operating system. As can be seen on the Wikipedia page of operating systems; there are quite a few such systems made for embedded devices and many of those are made for usag ...
... that require multitasking, networking or have similar relatively advanced features, it is more often than not easier to use an operating system. As can be seen on the Wikipedia page of operating systems; there are quite a few such systems made for embedded devices and many of those are made for usag ...
QUESTION BANK AOS
... Issues in IPC of multidatagram messages? Describe a mechanism for handling each Of issues. 8. Explain what is meant by absolute ordering, consistent ordering and casual ordering Of messages. Suggest a mechanism to implement each one. 9. What are the main issues in designing a transparent RPC mechani ...
... Issues in IPC of multidatagram messages? Describe a mechanism for handling each Of issues. 8. Explain what is meant by absolute ordering, consistent ordering and casual ordering Of messages. Suggest a mechanism to implement each one. 9. What are the main issues in designing a transparent RPC mechani ...
Socket
... the BSD Unix file access mechanism (open-readwrite-close) that provides an end-point for communication. ...
... the BSD Unix file access mechanism (open-readwrite-close) that provides an end-point for communication. ...
ITE PC v4.0 Chapter 1
... Leveraging CDP CDP is a layer 2 Cisco proprietary protocol used to discover other Cisco devices that are directly connected It is designed to allow the devices to auto-configure their connections If an attacker is listening to CDP messages, it could learn important information such as device m ...
... Leveraging CDP CDP is a layer 2 Cisco proprietary protocol used to discover other Cisco devices that are directly connected It is designed to allow the devices to auto-configure their connections If an attacker is listening to CDP messages, it could learn important information such as device m ...
Fonctionnement de la Messagerie Electronique or Email
... ailleurs, l'emploi de mots en majuscules indique, dans les pratiques du Net, que l'on veut exprimer de grandes émotions (joie, colère), ce qui n'est pas toujours bien ressenti par votre correspondant. Pour faire ressortir un terme, le placer plutôt entre guillemets. Avant de transmettre un message, ...
... ailleurs, l'emploi de mots en majuscules indique, dans les pratiques du Net, que l'on veut exprimer de grandes émotions (joie, colère), ce qui n'est pas toujours bien ressenti par votre correspondant. Pour faire ressortir un terme, le placer plutôt entre guillemets. Avant de transmettre un message, ...
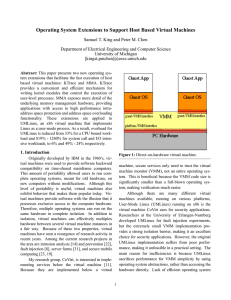
Operating System Extensions to Support Host Based Virtual Machines
... extensibility, and virtual memory abstractions that hide the power of the underling memory management haware are known to contribute to this performance degradation. In an effort to improve performance, I developed two new abstractions: KTrace and memory management abstractions (MMA). KTrace is a me ...
... extensibility, and virtual memory abstractions that hide the power of the underling memory management haware are known to contribute to this performance degradation. In an effort to improve performance, I developed two new abstractions: KTrace and memory management abstractions (MMA). KTrace is a me ...
doc.gold.ac.uk
... • Graphics, browser plug-ins, and e-mail attachments can harbor executable content • Graphic: embedded code can harm client computer • Browser plug-ins (programs) ...
... • Graphics, browser plug-ins, and e-mail attachments can harbor executable content • Graphic: embedded code can harm client computer • Browser plug-ins (programs) ...
The APIC Approach to High Performance Network Interface Design
... Protected DMA: This is a technique that is used to allow protocol libraries residing in user-space to queue buffers for transmission or reception directly to the APIC, without any kernel intervention, and without compromising the protection mechanisms of the operating system. Although similar functi ...
... Protected DMA: This is a technique that is used to allow protocol libraries residing in user-space to queue buffers for transmission or reception directly to the APIC, without any kernel intervention, and without compromising the protection mechanisms of the operating system. Although similar functi ...
Chaps_1-13_v5.0
... More about UNIX passwords A password is a string of characters. It can contain any alphanumeric or special character you see on the keyboard. There is (practically speaking) no maximum length. However, only the first 8 characters are significant. The rest of the characters are ignored any time you ...
... More about UNIX passwords A password is a string of characters. It can contain any alphanumeric or special character you see on the keyboard. There is (practically speaking) no maximum length. However, only the first 8 characters are significant. The rest of the characters are ignored any time you ...
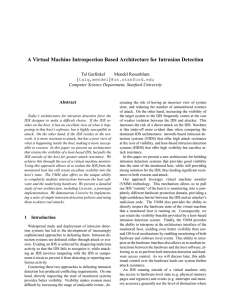
A Virtual Machine Introspection Based Architecture for Intrusion
... have sought to make user-level IDSes more attack resistant through “stealth,” i.e. by hiding the IDS using techniques similar to those used by attackers to hide their exploits, such as hiding IDS processes by modifying kernel structures and masking the presence of IDS files through the use of stegan ...
... have sought to make user-level IDSes more attack resistant through “stealth,” i.e. by hiding the IDS using techniques similar to those used by attackers to hide their exploits, such as hiding IDS processes by modifying kernel structures and masking the presence of IDS files through the use of stegan ...
Configuring
... The boot loader command line supports commands to format the flash file system, reinstall the operating system software, and recover from a lost or forgotten password. For example, the dir command can be used to view a list of files within a specified directory as shown in the figure. ...
... The boot loader command line supports commands to format the flash file system, reinstall the operating system software, and recover from a lost or forgotten password. For example, the dir command can be used to view a list of files within a specified directory as shown in the figure. ...
Advanced Operating System
... An operating system is an essential component of a computer system. The primary objectives of an operating system are to make computer system convenient to use and utilizes computer hardware in an efficient manner. An operating system is a large collection of software which manages resources of the ...
... An operating system is an essential component of a computer system. The primary objectives of an operating system are to make computer system convenient to use and utilizes computer hardware in an efficient manner. An operating system is a large collection of software which manages resources of the ...
Cooperating Processes
... – Web server (accept client request): Accessing several concurrent client (multithread). ...
... – Web server (accept client request): Accessing several concurrent client (multithread). ...