Lec1
... Of course, should also ask why the interfaces look the way they do, and whether it might be better to push more responsibilities into applications or into hardware, or vice versa. (examples, RISC architectures, VBasic libraries, etc.) ...
... Of course, should also ask why the interfaces look the way they do, and whether it might be better to push more responsibilities into applications or into hardware, or vice versa. (examples, RISC architectures, VBasic libraries, etc.) ...
Adeyl Khan
... program thinks it is writing to the printer The program actually writes to the hard disk When the program is complete, the file on the hard disk is sent to the printer ...
... program thinks it is writing to the printer The program actually writes to the hard disk When the program is complete, the file on the hard disk is sent to the printer ...
introduction - Eastern Mediterranean University
... Each processor runs an identical copy of the operating system which communicates with each other as needed. Many processes can run at once without performance deterioration. Most modern operating systems support SMP Asymmetric multiprocessing Each processor is assigned a specific task; mas ...
... Each processor runs an identical copy of the operating system which communicates with each other as needed. Many processes can run at once without performance deterioration. Most modern operating systems support SMP Asymmetric multiprocessing Each processor is assigned a specific task; mas ...
Slide 1
... consistent user interface provided by the OS • This UI can be a command-line interface in which a user types in the commands. Example: copy a:/file1.html c:/file1.html • Or, it can be a graphical UI, where Windows, Icons, Menus, and a Pointing device (such as a mouse) is used to receive and display ...
... consistent user interface provided by the OS • This UI can be a command-line interface in which a user types in the commands. Example: copy a:/file1.html c:/file1.html • Or, it can be a graphical UI, where Windows, Icons, Menus, and a Pointing device (such as a mouse) is used to receive and display ...
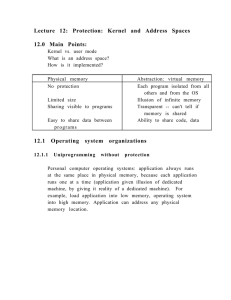
Lecture 12: Protection: Kernel and Address Spaces 12.0 Main Points
... each program verifies that its input is as expected. Alternately, on most UNIXes, can ask kernel to set up address spaces to share a region of memory, but that violates the whole notion of why we have address spaces -- to protect each program from bugs in the other programs. So why do UNIXes support ...
... each program verifies that its input is as expected. Alternately, on most UNIXes, can ask kernel to set up address spaces to share a region of memory, but that violates the whole notion of why we have address spaces -- to protect each program from bugs in the other programs. So why do UNIXes support ...
Lect03
... where # is the number of the Linux server that you have connected to. You may use any of the Linux servers. ...
... where # is the number of the Linux server that you have connected to. You may use any of the Linux servers. ...
Introduction - UW Courses Web Server
... Memory Protection: A region from the base to the limit register allowed to use ...
... Memory Protection: A region from the base to the limit register allowed to use ...
Operating systems. History. Function. Organization. Software
... • Users seeking services from same machine at the same time – time sharing – Implemented using a technique called multiprogramming (time is divided into multiple intervals, execution of one job is limited to a single time interval) ...
... • Users seeking services from same machine at the same time – time sharing – Implemented using a technique called multiprogramming (time is divided into multiple intervals, execution of one job is limited to a single time interval) ...
Document
... • Users seeking services from same machine at the same time – time sharing – Implemented using a technique called multiprogramming (time is divided into multiple intervals, execution of one job is limited to a single time interval) ...
... • Users seeking services from same machine at the same time – time sharing – Implemented using a technique called multiprogramming (time is divided into multiple intervals, execution of one job is limited to a single time interval) ...
Introduction
... • In multicomputers, a further distinction can be made between homogeneous and heterogeneous systems. • Examples of switched homogenous multicomputers: – Massively Parallel Processors (MPPs) are huge, multimillion dollar supercomputers consisting of thousands of CPUs. – Clusters of Workstations (COW ...
... • In multicomputers, a further distinction can be made between homogeneous and heterogeneous systems. • Examples of switched homogenous multicomputers: – Massively Parallel Processors (MPPs) are huge, multimillion dollar supercomputers consisting of thousands of CPUs. – Clusters of Workstations (COW ...
DOS - InfoShare.tk
... • The first module consist of BIOS which consist of system initialization program init which determines the linked set of resident device drivers for the console, auxiliary port, printer, clock devices and some hardware specific initialization code. ...
... • The first module consist of BIOS which consist of system initialization program init which determines the linked set of resident device drivers for the console, auxiliary port, printer, clock devices and some hardware specific initialization code. ...
What is an Operating System
... Constructs higher-level (virtual) resources out of lower-level (physical) resources (e.g., files). Definition: Is a collection of software enhancements, executed on the bare hardware, culminating in a high-level virtual machine that serves as an advanced programming environment ...
... Constructs higher-level (virtual) resources out of lower-level (physical) resources (e.g., files). Definition: Is a collection of software enhancements, executed on the bare hardware, culminating in a high-level virtual machine that serves as an advanced programming environment ...
CENG334 Introduction to Operating Systems
... Every application thinks it has its own CPU Every application thinks it has access to its memory space Every application thinks it has clean/simple interface to hardware devices Arbitration – Manages access to shared resources. ...
... Every application thinks it has its own CPU Every application thinks it has access to its memory space Every application thinks it has clean/simple interface to hardware devices Arbitration – Manages access to shared resources. ...
What is an Operating System? - Oman College of Management
... execution of one command, it seeks the next “control statement” from the user’s keyboard. On-line system must be available for users to access data and code. ...
... execution of one command, it seeks the next “control statement” from the user’s keyboard. On-line system must be available for users to access data and code. ...
Abstract View of System Components
... use of the hardware among the various application programs for the various users. 3. Applications programs – define the ways in which the system resources are used to solve the computing problems of the users (compilers, database systems, video games, business ...
... use of the hardware among the various application programs for the various users. 3. Applications programs – define the ways in which the system resources are used to solve the computing problems of the users (compilers, database systems, video games, business ...
Free-Space Management
... Thus, output to the disk through the file system is often faster than ...
... Thus, output to the disk through the file system is often faster than ...
CS_350_OS_PL_Presentation(1) Group 5
... but you want maximum cache hits o The competition for cache space means the OS must help decide which processes receive cache space to ...
... but you want maximum cache hits o The competition for cache space means the OS must help decide which processes receive cache space to ...
1.operating systems overview
... programmer and provides the programmer with a convenient interface for using system resources (system calls) ...
... programmer and provides the programmer with a convenient interface for using system resources (system calls) ...
1.operating systems overview
... programmer and provides the programmer with a convenient interface for using system resources (system calls) ...
... programmer and provides the programmer with a convenient interface for using system resources (system calls) ...
Mohammad Husain
... The permissions defined by ACLs are a superset of the permissions specified by the file permission bits. The permissions defined for the file owner correspond to the permissions of the ACL_USER_OBJ entry. The permissions defined for the file group correspond to the permissions of the ACL_GROUP_OBJ e ...
... The permissions defined by ACLs are a superset of the permissions specified by the file permission bits. The permissions defined for the file owner correspond to the permissions of the ACL_USER_OBJ entry. The permissions defined for the file group correspond to the permissions of the ACL_GROUP_OBJ e ...