slides - Simon Fraser University
... Before giving control to a user program, OS sets a timer to a specific value After period expires, an interrupt is issued and OS regains control OS then decides whether to grant more time for the program or terminate it ...
... Before giving control to a user program, OS sets a timer to a specific value After period expires, an interrupt is issued and OS regains control OS then decides whether to grant more time for the program or terminate it ...
CMPT 880: Internet Architectures and Protocols
... Before giving control to a user program, OS sets a timer to a specific value After period expires, an interrupt is issued and OS regains control OS then decides whether to grant more time for the program or terminate it ...
... Before giving control to a user program, OS sets a timer to a specific value After period expires, an interrupt is issued and OS regains control OS then decides whether to grant more time for the program or terminate it ...
Ch. 4 Operating System Fundamentals
... concurrent users and multiple jobs are called "network servers" or "servers“. Servers have operating systems installed called Network Operating Systems (NOS). There are three basic elements that make up the major design components of any operating system. 1. User interface 2. Kernel 3. File manageme ...
... concurrent users and multiple jobs are called "network servers" or "servers“. Servers have operating systems installed called Network Operating Systems (NOS). There are three basic elements that make up the major design components of any operating system. 1. User interface 2. Kernel 3. File manageme ...
Operating System Concepts
... Provides services to computer user To make more effective use of computer Why do we study it?... To get the knowledge of services ...
... Provides services to computer user To make more effective use of computer Why do we study it?... To get the knowledge of services ...
Slide 1
... – Hides the messy details which must be performed – Presents user with a virtual machine, easier to use ...
... – Hides the messy details which must be performed – Presents user with a virtual machine, easier to use ...
Tutorial-3 - WordPress.com
... 6- A computer has a monoprogramming operating system. If the size of memory is 64 MB and the memory reserved part for the operating system is 4 MB, what is the maximum size of program that can be run by this computer? ...
... 6- A computer has a monoprogramming operating system. If the size of memory is 64 MB and the memory reserved part for the operating system is 4 MB, what is the maximum size of program that can be run by this computer? ...
Operating system - Department of Computer Science
... processor. This allows the operating system to perform certain functions on a regular basis, like scheduling z Hardware Failure Interrupts: Generated by a failure (e.g. power failure or memory parity error). z Traps (Software Interrupts): Generated by some condition that occurs as a result of an ins ...
... processor. This allows the operating system to perform certain functions on a regular basis, like scheduling z Hardware Failure Interrupts: Generated by a failure (e.g. power failure or memory parity error). z Traps (Software Interrupts): Generated by some condition that occurs as a result of an ins ...
Unit I Operating Systems in Distributed Environments
... have the function to coordinate to the other parts of an OS such as : I/O Devices, Process, Memory and File Systems. • The structure of and OS could be different but in most of the time are very similar because some OS use Open Standards. ...
... have the function to coordinate to the other parts of an OS such as : I/O Devices, Process, Memory and File Systems. • The structure of and OS could be different but in most of the time are very similar because some OS use Open Standards. ...
Chapter One
... Use the date, cal, who, man, whatis, and clear commands Perform basic command-line editing operations Enter multiple commands on a single command line ...
... Use the date, cal, who, man, whatis, and clear commands Perform basic command-line editing operations Enter multiple commands on a single command line ...
Mgt 20600: IT Management
... Price/Performance gap between laptops and desktops has narrowed considerably Availability of workstation-class laptops for computing intensive tasks like software development and computer-aided design – Laptop reliability has improved ...
... Price/Performance gap between laptops and desktops has narrowed considerably Availability of workstation-class laptops for computing intensive tasks like software development and computer-aided design – Laptop reliability has improved ...
1. Introduction (by Andy Wang)
... system: collects a batch of jobs before processing them and printing out results ...
... system: collects a batch of jobs before processing them and printing out results ...
Operating System - GCG-42
... Over the years the Microsoft have evolved various versions of Windows. Win95, Win98, Win2000, Win ME, Win NT, Win XP. It gives user a handy environment where he doesn’t have to remember and learn the syntaxes of various commands as is the case in DOS. The user can just point and click on the I ...
... Over the years the Microsoft have evolved various versions of Windows. Win95, Win98, Win2000, Win ME, Win NT, Win XP. It gives user a handy environment where he doesn’t have to remember and learn the syntaxes of various commands as is the case in DOS. The user can just point and click on the I ...
Linux Systems Programming I
... develop and code several (six-ten) programs of intermediate difficulty and length in the C++ language, including programs broken into several files; 3. adhere to style and documentation standards in writing programs; 4. use system debuggers to step into and over code, set breakpoints and watch varia ...
... develop and code several (six-ten) programs of intermediate difficulty and length in the C++ language, including programs broken into several files; 3. adhere to style and documentation standards in writing programs; 4. use system debuggers to step into and over code, set breakpoints and watch varia ...
Document
... automatic validation on open (with server??) A cache entry is considered valid if one of the following are true: cache entry is less than t seconds old (3-30 s for files, 30-60 s for directories) modified time at server is the same as modified time on client ...
... automatic validation on open (with server??) A cache entry is considered valid if one of the following are true: cache entry is less than t seconds old (3-30 s for files, 30-60 s for directories) modified time at server is the same as modified time on client ...
Document
... • First software we see when we turn a computer on. • ‘Enables’ all the programs we use. • Organises and controls all the hardware. • Hides the details of all the actual processing from the user. ...
... • First software we see when we turn a computer on. • ‘Enables’ all the programs we use. • Organises and controls all the hardware. • Hides the details of all the actual processing from the user. ...
Test1
... The following image shows a Petri-net design of two processes engaged in communication. Explain how they are communicating. We ignore the necessity of sending any acknowledgement from the receiver to the sender. ...
... The following image shows a Petri-net design of two processes engaged in communication. Explain how they are communicating. We ignore the necessity of sending any acknowledgement from the receiver to the sender. ...
Objectives of KeyKOS
... as components of OS and their mutual relations can change over time, the evolution is easy to take place more operating systems can run on top of microkernel simultaneously ...
... as components of OS and their mutual relations can change over time, the evolution is easy to take place more operating systems can run on top of microkernel simultaneously ...
NETWORK OPERATING SYSTEMS
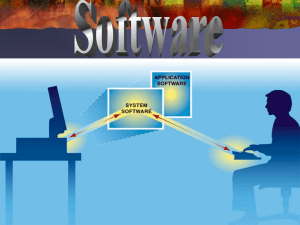
... These softwares are actually use to solve a problem. And the problem to be solved is user specific. You can simply say them end user programs or productivity programs, as they facilitate users to complete different tasks. System Software: Software which actually interacts with hardware. It makes it ...
... These softwares are actually use to solve a problem. And the problem to be solved is user specific. You can simply say them end user programs or productivity programs, as they facilitate users to complete different tasks. System Software: Software which actually interacts with hardware. It makes it ...
Fall 2008 Term - Computer Science
... 3. UNIX runs on virtually every computer ever made (including handheld computers, cell phones, watches, and Ipods). Although there are variations (different versions) of Unix, each provides fundamentally the same set of commands and tools. 4. Many variations of UNIX are open source. Thus, you can ob ...
... 3. UNIX runs on virtually every computer ever made (including handheld computers, cell phones, watches, and Ipods). Although there are variations (different versions) of Unix, each provides fundamentally the same set of commands and tools. 4. Many variations of UNIX are open source. Thus, you can ob ...
Introduction
... on each terminal port whenever the system is allowing users to log in After getty displays the message login: and some types the usernames followed by RETURN, it starts up a program called login to finish the process of logging in. Then getty ...
... on each terminal port whenever the system is allowing users to log in After getty displays the message login: and some types the usernames followed by RETURN, it starts up a program called login to finish the process of logging in. Then getty ...
Chapter 6
... programs in the system that need processing, giving each one a small slice of time on each cycle. ...
... programs in the system that need processing, giving each one a small slice of time on each cycle. ...
interrupt
... When counter zero generate an interrupt Set up before scheduling process to regain control or terminate program that exceeds allotted time ...
... When counter zero generate an interrupt Set up before scheduling process to regain control or terminate program that exceeds allotted time ...