* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download cs459 - Operating Systems: Introduction
Plan 9 from Bell Labs wikipedia , lookup
Security-focused operating system wikipedia , lookup
Copland (operating system) wikipedia , lookup
Unix security wikipedia , lookup
Burroughs MCP wikipedia , lookup
Spring (operating system) wikipedia , lookup
Distributed operating system wikipedia , lookup
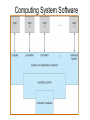
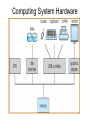
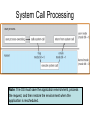
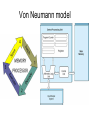
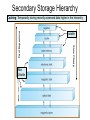
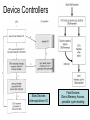
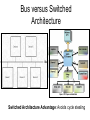
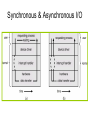
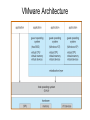
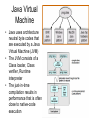
Operating Systems • Definition: Software that creates an environment so computer can perform useful tasks • What is in an operating system? – Loose definition: Everything that ships with the computer – More precise definition: Software that runs at all times (kernel). The rest is either a system utility or an application program • Possible focus – – – – – – Provide a good user experience Responsive to user commands Minimize idle time and maximize throughput Respond to real time constraints Maximize connectivity Efficient sharing distributed resources Computer System Components 1. Hardware – One or more CPUs, I/O devices and controllers, bus or switch connections, memory 2. Operating system modules: kernel, bootstrap (start up firmware), device drivers (for I/O), and disk resident subsystems 3. System utilities – Sysgen (System generation) software, defragmenters, disk editors, etc. 4. Application programs- Word processors, compilers, web browsers, database systems, video games 5. Users: People, machines, other computers Types of Operating Systems • Batch: Small resident kernel sequences jobs for one or more batch streams using a job control interface. Goal: minimize setup time, minimize idle time • Real time: Often part of special purpose embedded systems with no user interface. Goal: satisfy well-defined hard or soft time constraints • Time shared: Responds to multiple users at workstations. Scheduling is based on real time clock “slices”. Goal: Responsive to users • Desktop systems: Single users, with multitasked and multi-programming capabilities. Goal: user friendly and responsive • Multiprocessor: Tightly coupled processors sharing memory and peripherals. Goal: maximize throughput and reliability (redundancy) • Multi-computer: Loosely coupled, often heterogeneous systems working cooperatively. Goal: efficient and secure client-server or peer-to-peer intercomputer communication • Grid-based: loosely coupled, heterogeneous, geographically separated. Communicate through LAN or WAN; peer-to-peer or client-server. Goal: utilized distributed resources to address grand challenge problems • Handheld systems: Slow, limited in processor speed, available power and user interfaces. Goal: support user-friendly portable applications, maximize wireless connectivity, optimize battery life, optimize execution efficiency Real Time System Constraints • Hard (System fails if constraints not satisfied) – Guarantee that real time constraints complete on-time. – Not supportable by general purpose operating systems. – Data is stored in ROM or in short term memory; no secondary storage, virtual memory, or advanced operating system features. – Examples: Respond to sensor control inputs, assist scientific experiments, weapon systems, medical imaging • Soft (Best effort made to meet constraints) – Priority-based, delays are bounded. – Not useful for hard restraints like when a robotic arm movement cannot be stopped on time or if a gyroscope falls without fast enough CPU signals supplied. – Examples: streaming of audio and video, web cams, stock market activity Parallel Processing Peer to Peer or Client Server • Multiprocessors (tightly coupled) – Can be Less expensive because they share peripherals – Can be more reliable: • Service continues upon processor failure (graceful degradation) • One processor picks up functionality upon failure (fault tolerant) – Operation can be • Asymmetric: Each processor performs a separate task • Symmetric: All processors perform the same tasks simultaneously • Clustered systems (loosely coupled via local LAN) – High availability service – Asymmetric: one machine is in hot-standby mode – Symmetric: multiple host running and monitoring each other • Grids: loosely connected and geographically separated Computing System Software Computing System Hardware Dual-Mode Control Enables the Operating system to protect itself from users and executing software • Mode bit: Provided by hardware for dual-mode operation – User mode: Executing privileged instructions will automatically trap to the operating system – kernel mode: Full access to the system is enabled • Processing – At boot time: System is automatically in kernel mode – During System call: Mode automatically changes kernel mode – After responding to system call: Restore application environment, set mode to user, and reschedule the application – Illegal operations: A trap (exception) occurs. Control immediately transfers to the operating system, which creates a data dump and terminates the executing program • Note: Early PC's had no mode bit; applications could (and did) often crash the system System Timer Enables the Operating system to maintain ultimate control over the system • Definition: A device that signals at regular intervals (i.e. every millisecond) • Processing: A timer signal occurs Control transfers to the operating system in kernel mode Operating System decrement a system counter IF counter = 0 IF executing application exceeds run time limits (i.e. infinite loop) Create core dump and terminate the application ELSE IF process is compute bound (i.e. allocated time slice expires) Save application environment and schedule another application ELSE return control to the application System Call Processing Note: The OS must save the application environment, process the request, and then restore the environment when the application is rescheduled. System Boot 1. Reset event: hardware sets the program counter to a predefined location 2. A firmware bootstrap loader executes to: a. Execute diagnostics b. Loads a boot block from a fixed disk location 3. The boot block then loads the entire operating system into memory 4. The Operating system initializes itself and begins to execute Firmware Notes • Definition: Firmware is a set of instructions programmed persistently on a hardware device (i.e. ROM or EEPROM) • Some embedded devices store their entire operating system in firmware • Firmware updates: ROM-based firmware requires chip changes; EEPROM-based firmware allows updates after special command given System Software Components • Sysgen: – Purpose: install/configure an operating system onto specific hardware – Goal: user friendly installation process • Kernel: The part that is always in memory – Provides a basic interface for programs and device drivers – Include: scheduler, I/O subsystem, Memory Management module, and many others • User Interface: Command line interface, shell, or GUI enabling the operating system to communicate with users • System Programs: System level applications that normally reside on disk. Examples include loaders, compilers, editors, disk utilities, batch systems, communication services, system usage monitors, etc. The Operating System • Operating System Functions – – – – – – – – – – – Create a secure and stable user-friendly environment Efficiently schedule and execute programs (processes ) and threads Read and write from system hardware devices Connect to local and wide area networks Manage memory allocation and protect against illegal access Define and maintain the directory and access to secondary storage Allocate and share resources efficiently and fairly Maintain system security Enforce scheduling priorities Recovery from system faults Perform low-level system services for applications • Implementation – Higher level language: Portable, fast development, more maintainable – Assembly language: fast, less portable, difficult to maintain – Typical operating systems: 95% C, 5% Assembly Optimizing System Utilization Note: A single user generally cannot keep the CPU and I/O devices busy • Multiprogramming: Concurrent process execution – A set of jobs is kept in memory (or partially on disk) – The OS job scheduler module picks one to execute – A OS switch occurs when it blocks (ex: for I/O) • Multitasking/Time sharing: Multi-user responsiveness – – – – Extends multiprogramming OS switches between jobs frequently User Response time should be < 1 second Each user has at least one program executing • Multithreading: Multiple paths of execution in a process – Time consuming work is done in separate threads – Threads are spawned by processes – They have a program counter, register allocation, and stack but share all other resources with the parent process • Considerations – Swapping moves processes in and out of memory to run – Virtual memory allows execution of processes that don't fit in memory Process Management • A process is a program that is executing. – Programs are passive (blocks of executable instructions/data) – Processes are active (A program together with its active state) • Operating System responsibilities – – – – – – – Give process the resources they need Provide an API so processes can "talk" to the OS Protect processes from one another Allow processes to communicate with one another Implement fair share scheduling algorithms Terminate and reclaim reusable resources Create and manage execution of threads • Note: Typically systems have many processes running. These include applications, system processes, and background services Scheduling • Short Term (Must be extremely efficient) – – – – – Look at queue of processes that are ready to run Decide which has the highest priority Restore its runtime environment Set the system to user mode Transfer control to the process • Long Term (Low priority background process) – Decide if system load is at an acceptable level – Launch processes waiting to enter the system Von Neumann model Process Control Block Definition: An object that maintains the state of a process • A program counter and registers for all threads in a process • Pointers to the resources allocated to a process – File and device handles – Mutexes – Connections to remote resources • Physical and logical memory allocated to this process (which can be contiguous or not, in memory or on disk) • Initialization data • Runtime statistics and accounting information • Links to shared memory and connections to other processes Memory Management • Memory: volatile large array of bytes directly accessible by the processor. Can be DRAM (dynamic ram – one transistor per bit) or RAM (volatile transistor based storage) • Operating System responsibilities – Keep track of which parts of memory are currently in use – Transfer processes (or parts thereof) and data in and out of memory – Allocate and release memory space as needed – Maintain sections of memory for caching disk operations – Control shared memory accessible to multiple processes – Map logical program addresses into physical memory and maintain portions that are on disk and not contiguous – Prevent processes from overwriting each other's memory Protect and Manage Memory Operating System Operating System P1 part 1 P1 part 2 p1 part 3 Disk Memory Management Examples Free BSD MS-DOS (a) no process (b) process running Storage Management • Provide a uniform logical view of data – A logical storage view abstracts physical properties – Each medium is controlled by a storage device – Examples: disk, flash disks, cd, dvd, tape • OS responsibilities – Create the file system structure of files and directories – Mount and dismount devices – Maintain secondary storage by effectively mapping files onto available areas of the system mediums – Backup files onto stable storage media – Establish transparent connections to remote data – Establish access control mechanisms – Schedule writes and reads for maximum efficiency Storage Hierarchy • Storage systems are organized in hierarchy – Higher levels are faster, smaller, and are more likely to be volatile – Lower levels are slower, larger, and are less likely to be volatile • Cache: Temporarily copy data into faster storage – – – – Locality principle: Data accessed clusters in local areas Load policy: Retrieve the data needed plus surrounding data Replacement policy: Choice of cache items to expel when the cache fills Processing: • The system looks to a faster cache before accessing the slower hierarchy levels • Higher levels in the storage hierarchy can serve as caches for the lower levels • On updates, lower levels are either immediately updated (write through) or updated only when an item is expelled (delayed write) from the cache • Cache coherence (consistency of multiple caches) is an important consideration in parallel systems which contain multiple caches • Caching can be explicitly OS controlled or implicitly done in hardware Secondary Storage Hierarchy Non Volatile Volatile Slow Cheap Fast Expensive Caching: Temporarily storing recently accessed data higher in the hierarchy Storage Hierarchy Performance Cache Coherence • We must always use the most recent value, no matter where it is in storage hierarchy • A Multiprocessor environment must provide cache coherency. All CPUs have the most recent value in their local cache • Distributed environments are even more complex I/O Management • Purpose: hide hardware specifics from users • I/O subsystem responsible for – – – – – Buffering (storing data temporarily while it is being transferred) Caching (storing parts of data in faster storage for performance) Spooling (writing to disk instead of directly to the device) Uniform device-driver API to abstract device specifics Managing drivers (software modules) for specific hardware devices • Device Controllers – – – – – Operate simultaneously and autonomously with CPU Are limited instruction set processors to solely manage devices Are responsible for a particular type of device Contain local memory buffers and hardware registers to control I/O Example: SCSI (small computer-systems interface) handles seven or more devices The Interrupt Definition: A hardware signal that forces a program counter (PC) change • Interrupts occur when – Hardware devices complete operations – Software requests a service or attempts an illegal operation (a trap) • Processing (Interrupts give operating systems ultimate control) – Interrupt architecture saves the interrupted instruction address – Incoming interrupts are disabled to avoid lost interrupts. – Control may transfer control via a • Low memory device indexed interrupt vector (array) of addresses • A fixed location that polls to identify the type of interrupt – The CPU state is saved (PC and register contents). – Separate routines process the interrupt – The CPU state is restored and execution continues Approaches for Handling Devices 1. Device driver API: a uniform mechanism to abstract hardware operations from the rest of the system 2. Programmed I/O: Computer starts an operation and then waits in a tight loop for the operation to complete 3. Polling: A loop that inquires and responds to each device 4. Interrupts (A special I/O signal raised by a device) a.Computer starts an operation b.Computer does other things c. Computer transfers data, pice by piece, when interrupts occur 5. Direct Memory Access (DMA) a.Computer starts an operation b.Computer does other things c. Device transfers a block using main memory by cycle stealing d.Computer responds to interrupt when device i/o is done How do Interrupts Work? • Device raises an interrupt signal • Interrupt signal interrupts whatever the computer was doing, lower priority interrupts get disabled • The address of the executing instruction, registers, etc get saved (normally with a hardware stack) • An interrupt vector (array) contains addresses of device drivers • Device driver processes the interrupt • Incoming lower level interrupts are re-enabled • Control goes back to the OS short term scheduler Trap: Interrupts generated by software Device Controllers Slow Devices Interrupt-driven IO Fast Devices Direct Memory Access, possible cycle stealing Bus versus Switched Architecture Switched Architecture Advantage: Avoids cycle stealing Interrupt Timeline Synchronous & Asynchronous I/O Synchronous Asynchronous Device-Status Table Protection and Security • Protection: Internal mechanism to control user and process access to system resources – Specifies and implements the controls available – Distinguish between authorized and unauthorized use – Detect and recover from hardware faults – Examples: infinite loop, malicious processes, disk corruption • Security: Internal or external attack defense mechanisms – Operating system middleware level approaches – Examples: denial-of-service, worms, viruses, identity theft • Techniques to enforce protections and security – Distinguish between groups of users: user ID and group ID – Privilege escalation: process request additional rights (setuid call) – Access Control: rwx rights (chmod) Network Services • Communications – Exchange of Information – To processes in the same computer – To processes on remote network computers • Protocol Stack Layers (ISO) 1. Physical layer – Standardized electrical interfaces (RS 232C) 2. Data Link Layer – Send, receive, detect errors, retransmit (Ethernet) 3. Network Layer – Routing (IP) 4. Transport Layer – connection-oriented (TCP) or connectionless (UDP) packet handling 5. Session Layer – Synchronization for checkpoints 6. Presentation Layer – Format of the message fields 7. Application Layer – FTP, HTTP, e-mail, etc. Note: Layers 5 and 6 are often not used Note: Middleware consists of background service processes, which provide communication and data management facilities to application programs User Interface Definition: The mode of communication between the operating system and users • Embedded systems: special purpose buttons and displays • Unix and batch systems: command line interface (CLI) – Direct command entry – Fetch command and execute – Fast commands execute directly, others launch system programs • Windows and IOS: Graphics User Interface (GUI) – – – – Point and click: mouse, keyboard, and monitor Touch: finger movements trigger actions Icon based: files, programs, actions, etc show as icons Various types of mouse clicks respond accordingly • Hybrids: Both CLI and GUI components – – – – Microsoft Windows is GUI with CLI “command” shell Apple Mac OS X is GUI interface with various UNIX shells Solaris is CLI with optional GUIs (Java Desktop, KDE) Handheld has terminal apps with touch controls Fault Recovery and Detection • OS constantly checks for possible errors – – – – – Faulty disk sectors (maintain spare tracks and sectors) Physical memory failure (skip use of memory areas) Program faults (rollback, checkpoint, restart) Network connection problems (retransmission) Device redundancy (switch devices automatically upon failure) • Debugging aids: – – – – Provide logs and dumps along with the ability to analyze problems Single step debugging capabilities Program trace facility Execution histograms • Backup and clean up facilities – Defragmenter, disk verifier, firewall System Call – OS Application API • The OS implements a table of available system calls, each with a welldefined interface and supported by compiler run-time libraries • User program invoke calls to run-time libraries, which execute privileged instructions and traps to the OS kernel. The OS processes system call requests, returning status and return values Standard API Example Java read() method byte[] b - the buffer to store read data int off - the starting offset in b int len - the maximum number of bytes= System Call: Copy File Example • Low level assembly: Execute designated privileged instruction, which traps to the OS • Low level C: Utilize libraries to execute privileged instructions • Higher level programmers: Use class-based interfaces • Cross-platform libraries – Win32 API: windows – POSIX API: POSIXcompliant systems – Java API: Java JVM Copy File application system call log System Call arguments 1. First approach: Pass in hardware registers Disadvantage: There may not be enough registers 2. Second approach: Pass in an register addressed array. Advantage: There is no argument limit Note: Linux and Solaris use this approach 3. Push parameters onto a special stack Advantage: most flexible Disadvantage: loss of efficiency Parameter Passing via Table Operating System Design Goals Tradeoffs: flexibility, efficiency, kernel size, maintainability • Maximum functionality/efficiency using minimal memory – Example: MSDOS, which is monolithic, non-modular, unprotected • Maintainability (Use a higher level language (i.e. C) where possible) – Layered design: Lower levels request services from higher levels • Advantage: Easy testing and replacing layer implementations • Less efficient: multiple levels of system calls from layer to layer • Difficulty: no clear cut way to assign system functions to layers – Modular: Separate object oriented modules with well-defined interfaces – Micro kernel • Perform as many functions as possible in user mode • Communication using a message passing paradigm • Easier to extend and port; is more reliable and secure. • Degraded performance; inefficient user to kernel communication OS Organization Examples Solaris Kernel Modules Layered Approach Unix Kernel • • • • • Each layer built on top of lower layers. The bottom layer (layer 0), is hardware The highest (layer N) is user interface. layers use services of lower-level layers Easy to debug, and test replacement layers OS Policies and Mechanisms Policy (Design Goal) Mechanism (Implementation) Program Independence Restrict memory access Fair scheduling of resources Priority scheduling Support many devices Standard device driver interface Transparent input and output Privileged instructions Plug and play Check for new hardware Fault recovery Device redundancy Authentication/authorization Access control lists, passwords Run very large programs Virtual memory Handle critical sections Semaphores Concurrency Multithreading, Multiprogramming Virtual Machines • Virtual machines provide – API identical to bare hardware – Allocate of portions of disk to each virtual machine – Spooling to virtual print devices – Workstation virtual console – Combine software emulation or hardware virtualization • Advantages: – Operating systems research – Cross-platform testing • Disadvantages: – No direct sharing of resources between virtual machines – Significant loss of performance – No sharing of resources between the virtual machines The operating system illusion of multiple processes executing on their own bare-hardware processor VMware Architecture Java Virtual Machine • Java uses architecture neutral byte codes that are executed by a Java Virtual Machine (JVM) • The JVM consists of a Class loader, Class verifier, Runtime interpreter • The just-in-time compilation results in performance that is often close to native-code execution The JX Operating Systems 1. Each domain in JX is a separate JVM, with its own heap and garbage collection 2. Domain 0 is the micro kerrnel, written in C and assembly, and providing low level hardware access. Other domains are written entirely in Java. 3. Cross communication implemented through portals 4. The language semantics eliminates the need for using memory management facilities; however, virtual memory then is not possible









































![[Lecture 1, part 3] Kernel interaction with the hardware: Interrupt](http://s1.studyres.com/store/data/014183875_1-7af0f6b03bedcfbf8972c6054b446a98-150x150.png)










