Enhanced Security Models for Operating Systems: A Cryptographic
... Computer Security problem: Earlier, many approaches have been tried in order to provide security in use of computing resources, but we have only limited success. Why is this situation actually getting worse? Reason: Increased use of distributed computing resources across insecure networks and un ...
... Computer Security problem: Earlier, many approaches have been tried in order to provide security in use of computing resources, but we have only limited success. Why is this situation actually getting worse? Reason: Increased use of distributed computing resources across insecure networks and un ...
download
... • No single mechanism that will support all functions required • One particular element underlies many of the security mechanisms in use: cryptographic techniques ...
... • No single mechanism that will support all functions required • One particular element underlies many of the security mechanisms in use: cryptographic techniques ...
Advanced Linux Security
... • All subjects (processes) and objects (files, sockets, . . . ) have a set of security attributes, referred to as the security context of the object. • Instead of working with the security context all the time, the security server maintains a mapping between security at-tribute sets and security ide ...
... • All subjects (processes) and objects (files, sockets, . . . ) have a set of security attributes, referred to as the security context of the object. • Instead of working with the security context all the time, the security server maintains a mapping between security at-tribute sets and security ide ...
Guidance for when No PP Exists
... NIAP will only accept products for evaluation against Protection Profiles (i.e. Security Target-based evaluations are not accepted within NIAP), this guidance explains options for vendors and end users when a suitable Protection Profile is not available for certain products. NIAP takes several facto ...
... NIAP will only accept products for evaluation against Protection Profiles (i.e. Security Target-based evaluations are not accepted within NIAP), this guidance explains options for vendors and end users when a suitable Protection Profile is not available for certain products. NIAP takes several facto ...
Information Assurance (IA) Framework
... requirements and, to the extent possible, it is the intention of the architecture that these capabilities be “baked-in.” In other words, they are identified, designed, and delivered from the very first builds, rather than through some effort to add them on at the end. It is virtually impossible to a ...
... requirements and, to the extent possible, it is the intention of the architecture that these capabilities be “baked-in.” In other words, they are identified, designed, and delivered from the very first builds, rather than through some effort to add them on at the end. It is virtually impossible to a ...
The Top Ten of Security
... as in a DDOS attack, you could be liable. • Using industry Best Practices can protect you from lawsuits. ...
... as in a DDOS attack, you could be liable. • Using industry Best Practices can protect you from lawsuits. ...
D1S1_TSV404_Course_Intro_2011_v1
... ■ Up-front design criteria for hosts, networks, applications and systems ■ Difficult to retrofit information protection into an environment where none previously existed ■ Protection designed into a system should be consistent with the threat to which it is likely to be exposed ■ Major consideration ...
... ■ Up-front design criteria for hosts, networks, applications and systems ■ Difficult to retrofit information protection into an environment where none previously existed ■ Protection designed into a system should be consistent with the threat to which it is likely to be exposed ■ Major consideration ...
Overview of Database Security
... A code able to copy itself and to damage permanently and often irreparably the environment where it gets reproduced ...
... A code able to copy itself and to damage permanently and often irreparably the environment where it gets reproduced ...
Slides.
... 1. Something the user knows 2. Something the user has 3. Something the user is This is done before user can use the system ...
... 1. Something the user knows 2. Something the user has 3. Something the user is This is done before user can use the system ...
SANDS CORP CYBER JOB
... Must be able to work collaboratively with the global team. Experience configuring and installing information security applications. Hands-on experience with security applications is preferred. Fundamental understanding of encryption technologies. Understanding of common network traffic, i.e., Transm ...
... Must be able to work collaboratively with the global team. Experience configuring and installing information security applications. Hands-on experience with security applications is preferred. Fundamental understanding of encryption technologies. Understanding of common network traffic, i.e., Transm ...
Certifications authenticate Blancco´s high standards
... the high standards the MoD requires, special security specifications were set based on CESG’s standards. Blancco is currently the only DIPCOG approved product for selective data erasure and is highly recommended for use within the UK’s MoD. ...
... the high standards the MoD requires, special security specifications were set based on CESG’s standards. Blancco is currently the only DIPCOG approved product for selective data erasure and is highly recommended for use within the UK’s MoD. ...
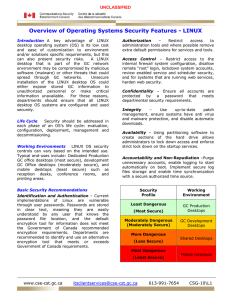
Overview of Operating Systems Security Features
... desktop that is part of the GC network environment may be compromised by malicious software (malware) or other threats that could spread through GC networks. Unsecure installation of the LINUX desktop OS could either expose stored GC information to unauthorized personnel or make critical information ...
... desktop that is part of the GC network environment may be compromised by malicious software (malware) or other threats that could spread through GC networks. Unsecure installation of the LINUX desktop OS could either expose stored GC information to unauthorized personnel or make critical information ...
Evaluation and Assurance - NYU Polytechnic School of
... QuickTi me™ and a TIFF (U ncompressed) decompressor are needed to see this picture. ...
... QuickTi me™ and a TIFF (U ncompressed) decompressor are needed to see this picture. ...
Architecting High-Security Systems for Multilateral
... Using hypervisors to isolate large, defective operating systems and the applications, which run on top of them, is a step into the right direction. However, virtualization does not necessarily imply separation. Many solutions are integrated into large and potentially defective operating systems whic ...
... Using hypervisors to isolate large, defective operating systems and the applications, which run on top of them, is a step into the right direction. However, virtualization does not necessarily imply separation. Many solutions are integrated into large and potentially defective operating systems whic ...
secure operating system
... A reference monitor is the classical access enforcement mechanism. It takes a request as input, and returns a binary response Indicating whether the request is authorized by the reference monitor’s access control policy. We identify three distinct components of a reference monitor: (1) its interfa ...
... A reference monitor is the classical access enforcement mechanism. It takes a request as input, and returns a binary response Indicating whether the request is authorized by the reference monitor’s access control policy. We identify three distinct components of a reference monitor: (1) its interfa ...
Lecture 10 - The University of Texas at Dallas
... process finds the file locked, a 1 bit is passed covertly - When the Secret process unlocks the file and the Unclassified process finds it unlocked, a 1 bit is passed covertly - Over time the bits could contain sensitive data ...
... process finds the file locked, a 1 bit is passed covertly - When the Secret process unlocks the file and the Unclassified process finds it unlocked, a 1 bit is passed covertly - Over time the bits could contain sensitive data ...
Firewall
... • imposes security by limiting which such connections are allowed • once created usually relays traffic without examining contents • typically used when trust internal users by allowing general outbound connections • SOCKS commonly used for this ...
... • imposes security by limiting which such connections are allowed • once created usually relays traffic without examining contents • typically used when trust internal users by allowing general outbound connections • SOCKS commonly used for this ...
Security
... securely without ability to authorize users, processes, control their access, and log their activities. Hardware protection, e.g. memory protection, features are a must for overall protection scheme. January 2017 ...
... securely without ability to authorize users, processes, control their access, and log their activities. Hardware protection, e.g. memory protection, features are a must for overall protection scheme. January 2017 ...
Chapter 1
... The challenge is to develop operating systems which can share information without allowing this behavior. ...
... The challenge is to develop operating systems which can share information without allowing this behavior. ...
William Stallings, Cryptography and Network Security 3/e
... • imposes security by limiting which such connections are allowed • once created usually relays traffic without examining contents • typically used when trust internal users by allowing general outbound connections • SOCKS commonly used for this ...
... • imposes security by limiting which such connections are allowed • once created usually relays traffic without examining contents • typically used when trust internal users by allowing general outbound connections • SOCKS commonly used for this ...
High Assurance MLS File Service - Center for Computer Systems
... The crypto seal guard architecture uses two or more guards connected by a common systemhigh network. Each guard has one high and one or more low interfaces. Each guard cryptographically binds the sensitivity level of the source network with the contents of each packet it forwards from lowto-high. Th ...
... The crypto seal guard architecture uses two or more guards connected by a common systemhigh network. Each guard has one high and one or more low interfaces. Each guard cryptographically binds the sensitivity level of the source network with the contents of each packet it forwards from lowto-high. Th ...