Slides
... - Look for users to connect to a high number of systems Especially useful if you isolate events into periods of time - User A connected to N number of systems in T minutes ...
... - Look for users to connect to a high number of systems Especially useful if you isolate events into periods of time - User A connected to N number of systems in T minutes ...
module10b
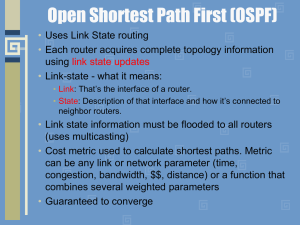
... to become neighbors. • Neighbors: All other routers who are your neighbors are specified in the hello packet. • Area ID: This is the area you are in. This value has to match on both sides in order to become neighbors. • Router Priority: This value is used to determine who will become designated or b ...
... to become neighbors. • Neighbors: All other routers who are your neighbors are specified in the hello packet. • Area ID: This is the area you are in. This value has to match on both sides in order to become neighbors. • Router Priority: This value is used to determine who will become designated or b ...
800xA Server Node Virtualization with VMware ESX
... Configuration Information (3BSE041434Rxxxx) instruction should be kept the same also when the node is installed inside virtual machines. Given that these rules are followed, with additions and limitations given in this document, the performance data stated in the system guide will be fulfilled. The ...
... Configuration Information (3BSE041434Rxxxx) instruction should be kept the same also when the node is installed inside virtual machines. Given that these rules are followed, with additions and limitations given in this document, the performance data stated in the system guide will be fulfilled. The ...
3346 Software User Guide V6.3
... Netopia and Cayman are registered trademarks, and “Making Broadband Work” is a trademark of Netopia, Inc. All rights reserved. Ethernet is a registered trademark of Xerox Corporation. Microsoft and Windows are registered trademarks of Microsoft Corporation. All other trademarks are the property of t ...
... Netopia and Cayman are registered trademarks, and “Making Broadband Work” is a trademark of Netopia, Inc. All rights reserved. Ethernet is a registered trademark of Xerox Corporation. Microsoft and Windows are registered trademarks of Microsoft Corporation. All other trademarks are the property of t ...
Ch-5 Presentation
... many devices shared the same segment, network engineers added bridges to create multiple collision domains. As networks grew in size and complexity, the bridge evolved into the modern switch, allowing microsegmentation of the network. Today’s networks typically are built using switches and routers, ...
... many devices shared the same segment, network engineers added bridges to create multiple collision domains. As networks grew in size and complexity, the bridge evolved into the modern switch, allowing microsegmentation of the network. Today’s networks typically are built using switches and routers, ...
Cisco Catalyst 3500 Series XL
... per 3500 series XL switch, spanning multiple routers, switches, and access routers Reduces administrative costs and simplifies network moves, adds, and changes Enables better management and control of broadcast and multicast traffic Improves network security by establishing separate VLAN groups for ...
... per 3500 series XL switch, spanning multiple routers, switches, and access routers Reduces administrative costs and simplifies network moves, adds, and changes Enables better management and control of broadcast and multicast traffic Improves network security by establishing separate VLAN groups for ...
Fingerprinting Encrypted Tunnel Endpoints Vafa Dario Izadinia U
... design, which introduce a weakness in the system. These two: the implementation, and the relaxed adherence to the original standards, account for weaknesses in vendors´ products. It comes as no surprise then, when products boasting strong encryption, are bypassed, or broken-into. Whether it be intru ...
... design, which introduce a weakness in the system. These two: the implementation, and the relaxed adherence to the original standards, account for weaknesses in vendors´ products. It comes as no surprise then, when products boasting strong encryption, are bypassed, or broken-into. Whether it be intru ...
Proceedings of the 9th USENIX Security Symposium USENIX Association Denver, Colorado, USA
... be set up to scan very slowly, i.e. over days. These reports can be compiled over weeks or months and cover large portions of a network. When someone discovers a new exploit for a speci c operating system, it is simple for an attacker to generate a script to run the exploit against each correspondin ...
... be set up to scan very slowly, i.e. over days. These reports can be compiled over weeks or months and cover large portions of a network. When someone discovers a new exploit for a speci c operating system, it is simple for an attacker to generate a script to run the exploit against each correspondin ...
Reference Manual for the 108 Mbps Wireless Firewall Router WGT624
... MAC Addresses and Address Resolution Protocol ................................................. B-8 Related Documents ................................................................................................. B-9 Domain Name Server ............................................................. ...
... MAC Addresses and Address Resolution Protocol ................................................. B-8 Related Documents ................................................................................................. B-9 Domain Name Server ............................................................. ...
third edition
... insight needed to work in tomorrow’s landscape. And that is important, since there is no reason to believe that the evolution of networks is going to slow down anytime soon. It is hard to remember what the world looked like only ten years ago. Back then the Internet was not really a commercial reali ...
... insight needed to work in tomorrow’s landscape. And that is important, since there is no reason to believe that the evolution of networks is going to slow down anytime soon. It is hard to remember what the world looked like only ten years ago. Back then the Internet was not really a commercial reali ...
OSI layers
... components to allow multiple vendor development and support. It allows different types of network hardware and software to communicate with each other. It prevents changes in one layer from affecting other layers. It divides network communication into smaller parts to make learning it easier to unde ...
... components to allow multiple vendor development and support. It allows different types of network hardware and software to communicate with each other. It prevents changes in one layer from affecting other layers. It divides network communication into smaller parts to make learning it easier to unde ...
Chapter 3
... the TCP layer which uses two types of messages: Error-Reporting and Query • Query uses one of four types of messages, including Echo Request and Reply. • Ping combines the Echo Request and Reply function of ICMP with UDP in an IP packet to validate whether a node is functioning ...
... the TCP layer which uses two types of messages: Error-Reporting and Query • Query uses one of four types of messages, including Echo Request and Reply. • Ping combines the Echo Request and Reply function of ICMP with UDP in an IP packet to validate whether a node is functioning ...
Routing & Addressing
... • Router can also be called a computer – However, it is a special purpose computer that is dedicated to routing ...
... • Router can also be called a computer – However, it is a special purpose computer that is dedicated to routing ...
Reference Manual for the MR814v2 Cable/DSL Wireless Router
... Routing Information Protocol ................................................................................... B-2 IP Addresses and the Internet ....................................................................................... B-2 Netmask ..................................................... ...
... Routing Information Protocol ................................................................................... B-2 IP Addresses and the Internet ....................................................................................... B-2 Netmask ..................................................... ...
DSL-G624T Wireless ADSL Router User Guide
... Since ADSL and telephone services share the same copper wiring to carry their respective signals, a filtering mechanism may be necessary to avoid mutual interference. A low pass filter device can be installed for each telephone that shares the line with the ADSL line. These filters are easy to insta ...
... Since ADSL and telephone services share the same copper wiring to carry their respective signals, a filtering mechanism may be necessary to avoid mutual interference. A low pass filter device can be installed for each telephone that shares the line with the ADSL line. These filters are easy to insta ...
DSL-2750U - D-Link
... Please, read this manual prior to installing the device. Make sure that you have all the necessary information and equipment. Operating System Configuration of the multifunction 3G/ADSL/Ethernet router DSL-2750U (hereinafter referred to as “the router”) is performed via the built-in web-based interf ...
... Please, read this manual prior to installing the device. Make sure that you have all the necessary information and equipment. Operating System Configuration of the multifunction 3G/ADSL/Ethernet router DSL-2750U (hereinafter referred to as “the router”) is performed via the built-in web-based interf ...
IP: Addresses and Forwarding - RPI ECSE
... Flooding in NBMA always goes through DR Multicast not available to optimize LSA flooding. DR generates network-LSA just like broadcast subnet ...
... Flooding in NBMA always goes through DR Multicast not available to optimize LSA flooding. DR generates network-LSA just like broadcast subnet ...
cis185-ROUTE-lecture2-EIGRP-Part2
... By default, a Frame Relay network is an NBMA network. Like multiaccess networks (Ethernet LANs) All routers are on the same subnet But broadcast (and multicast) packets CANNOT be sent just once as they are in a broadcast environment such as Ethernet. Cisco IOS implements pseudo-broadcasting ...
... By default, a Frame Relay network is an NBMA network. Like multiaccess networks (Ethernet LANs) All routers are on the same subnet But broadcast (and multicast) packets CANNOT be sent just once as they are in a broadcast environment such as Ethernet. Cisco IOS implements pseudo-broadcasting ...
Secure and Distributed Multicast Address Allocation on IPv6 Networks M. L. Slaviero
... Why is the exploitation of a resource which promised so much, so limited? A common argument made is that many devices do not support multicast, and this is examined in a later chapter. Jonathan Barter, a self-proclaimed multicast evangelist, believes that better marketing is required to increase mul ...
... Why is the exploitation of a resource which promised so much, so limited? A common argument made is that many devices do not support multicast, and this is examined in a later chapter. Jonathan Barter, a self-proclaimed multicast evangelist, believes that better marketing is required to increase mul ...
Network Performance Definitions & Analysis
... Via satellite with a distance of 30 km between the base and the satellite ...
... Via satellite with a distance of 30 km between the base and the satellite ...
Computer Networking : Principles, Protocols and Practice
... has produced several excellent textbooks in the networking community. At a time when networking textbooks were mainly theoretical, Douglas Comer chose to write a textbook entirely focused on the TCP/IP protocol suite [Comer1988], a difficult choice at that time. He later extended his textbook by des ...
... has produced several excellent textbooks in the networking community. At a time when networking textbooks were mainly theoretical, Douglas Comer chose to write a textbook entirely focused on the TCP/IP protocol suite [Comer1988], a difficult choice at that time. He later extended his textbook by des ...
CCNA5.0 Instructor PPT
... Purpose of Dynamic Routing Protocols (cont.) Main components of dynamic routing protocols include: Data structures - Routing protocols typically use tables or databases for its operations. This information is kept in RAM. Routing protocol messages - Routing protocols use various types of message ...
... Purpose of Dynamic Routing Protocols (cont.) Main components of dynamic routing protocols include: Data structures - Routing protocols typically use tables or databases for its operations. This information is kept in RAM. Routing protocol messages - Routing protocols use various types of message ...
Seamless Vertical Handoff over Heterogeneous Network
... C. Guo, et. al., “A Seamless and Proactive End-to-End Mobility Solution for Roaming Across Heterogeneous Wireless Networks,” IEEE JSAC, 22(5), pp.834-848. Jun. 2004 ...
... C. Guo, et. al., “A Seamless and Proactive End-to-End Mobility Solution for Roaming Across Heterogeneous Wireless Networks,” IEEE JSAC, 22(5), pp.834-848. Jun. 2004 ...
LevelOne
... This printer server provides an Ethernet network port (10/100Mbps Ethernet) and one print port for printer. This printer server supports IPX/SPX, NetBEUI, TCP/IP and AppleTalk protocols. It is the best network printing solutions for various common network operating systems such as Windows 98SE/ME/20 ...
... This printer server provides an Ethernet network port (10/100Mbps Ethernet) and one print port for printer. This printer server supports IPX/SPX, NetBEUI, TCP/IP and AppleTalk protocols. It is the best network printing solutions for various common network operating systems such as Windows 98SE/ME/20 ...
TL-WR542G 54M Wireless Router
... ¾ Reset button: There are two ways to reset the router's factory defaults: ...
... ¾ Reset button: There are two ways to reset the router's factory defaults: ...