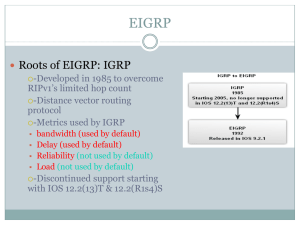
EIGRP
... you can see in the figure, EIGRP uses different EIGRP packets and maintains separate neighbor, topology, and routing tables for each Network layer protocol. • The IP-EIGRP module is responsible for sending and receiving EIGRP packets that are encapsulated in IP and for using DUAL to build and mainta ...
... you can see in the figure, EIGRP uses different EIGRP packets and maintains separate neighbor, topology, and routing tables for each Network layer protocol. • The IP-EIGRP module is responsible for sending and receiving EIGRP packets that are encapsulated in IP and for using DUAL to build and mainta ...
S9700 Series Terabit Routing Switches
... operation time, which reduce customers' total cost of ownership (TCO). The S9700 is available in three models: S9703, S9706, and S9712, which provide different switching capacities and port densities to suit networks of different scales. Furthermore, the S9700 adopts innovative energy saving technol ...
... operation time, which reduce customers' total cost of ownership (TCO). The S9700 is available in three models: S9703, S9706, and S9712, which provide different switching capacities and port densities to suit networks of different scales. Furthermore, the S9700 adopts innovative energy saving technol ...
Introduction to IPv6 protocol
... • «Anycast addresses allow a packet to be routed to one of a number of different nodes all responding to the same address » • «Anycast addresses are taken from the unicast address spaces (of any scope) and are not syntactically distinguishable from unicast addresses … it may be assigned to an IPv6 r ...
... • «Anycast addresses allow a packet to be routed to one of a number of different nodes all responding to the same address » • «Anycast addresses are taken from the unicast address spaces (of any scope) and are not syntactically distinguishable from unicast addresses … it may be assigned to an IPv6 r ...
On Networks N300 WiFi Router(N300R) User Manual
... configuration is correct. Your Internet service provider (ISP) should have provided you with all the information needed to connect to the Internet. If you cannot locate this information, ask your ISP to provide it. When your router Internet connection is set up, you no longer need to launch the ISP’ ...
... configuration is correct. Your Internet service provider (ISP) should have provided you with all the information needed to connect to the Internet. If you cannot locate this information, ask your ISP to provide it. When your router Internet connection is set up, you no longer need to launch the ISP’ ...
Cisco WRVS4400N Wireless-N Gigabit Security Router
... If you use the Router to share your cable or DSL Internet connection, contact your ISP to find out if they have assigned a static IP address to your account. If so, you will need that static IP address when configuring the Router. You can get the information from your ISP. A dynamic IP address is au ...
... If you use the Router to share your cable or DSL Internet connection, contact your ISP to find out if they have assigned a static IP address to your account. If so, you will need that static IP address when configuring the Router. You can get the information from your ISP. A dynamic IP address is au ...
M T ASTER’S HESIS
... groups have members on their directly attached subnetworks. Hosts respond to a query with a Host Membership Report for each host group to which they belong on the network interface from which the query was received. To minimize the protocol overhead, when a host receives a query, rather than sending ...
... groups have members on their directly attached subnetworks. Hosts respond to a query with a Host Membership Report for each host group to which they belong on the network interface from which the query was received. To minimize the protocol overhead, when a host receives a query, rather than sending ...
Introduction to Dynamic Routing Protocols
... The data networks that we use in our everyday lives to learn, play, and work range from small, local networks to large, global internetworks. At home, you might have a router and two or more computers. At work, your organization might have multiple routers and switches servicing the data communicati ...
... The data networks that we use in our everyday lives to learn, play, and work range from small, local networks to large, global internetworks. At home, you might have a router and two or more computers. At work, your organization might have multiple routers and switches servicing the data communicati ...
ccna4-mod3-PPP
... – ID = sequential number that identifies the challenge. – random = a reasonably random number generated by the router. – HQ = the authentication name of the challenger. 2. The ID and random values are kept on the called router. 3. The challenge packet is sent to the calling router. A list of outstan ...
... – ID = sequential number that identifies the challenge. – random = a reasonably random number generated by the router. – HQ = the authentication name of the challenger. 2. The ID and random values are kept on the called router. 3. The challenge packet is sent to the calling router. A list of outstan ...
Multicast
... receiver’s address when sending packets Network/routers keep track of actual receiving subnets/paths for this group address (not the actual receivers) Receivers can reply to sender’s address or to group address ...
... receiver’s address when sending packets Network/routers keep track of actual receiving subnets/paths for this group address (not the actual receivers) Receivers can reply to sender’s address or to group address ...
OS fingerprinting with IPv6
... Over the next years to come IPv6 will eventually replace IPv4 in private and public networks. This paper attempts to describe upcoming challenges and limitations as well as new methods of OS fingerprinting with the shift to IPv6. This includes performing network scans and finding live hosts to finge ...
... Over the next years to come IPv6 will eventually replace IPv4 in private and public networks. This paper attempts to describe upcoming challenges and limitations as well as new methods of OS fingerprinting with the shift to IPv6. This includes performing network scans and finding live hosts to finge ...
APS: Modbus Protocol User Guide
... The IAP Device Server uses TCP/IP protocols for network communication. The supported standards are ARP, UDP, TCP, ICMP, Telnet, TFTP, DHCP, and SNMP. For transparent connections, TCP/IP (binary stream) or Telnet protocols are used. Firmware upgrades can be made with the TFTP protocol. The IP protoco ...
... The IAP Device Server uses TCP/IP protocols for network communication. The supported standards are ARP, UDP, TCP, ICMP, Telnet, TFTP, DHCP, and SNMP. For transparent connections, TCP/IP (binary stream) or Telnet protocols are used. Firmware upgrades can be made with the TFTP protocol. The IP protoco ...
Communications Server for z/OS V1R2 TCP/IP
... This edition applies to Version 1, Release 2 of Communications Server for z/OS. Comments may be addressed to: IBM Corporation, International Technical Support Organization Dept. HZ8 Building 662 P.O. Box 12195 Research Triangle Park, NC 27709-2195 When you send information to IBM, you grant IBM a no ...
... This edition applies to Version 1, Release 2 of Communications Server for z/OS. Comments may be addressed to: IBM Corporation, International Technical Support Organization Dept. HZ8 Building 662 P.O. Box 12195 Research Triangle Park, NC 27709-2195 When you send information to IBM, you grant IBM a no ...
Chord: A Scalable Peer-to-Peer Lookup Protocol for Internet Applications
... Three features that distinguish Chord from many other peer-to-peer lookup protocols are its simplicity, provable correctness, and provable performance. To clarify comparisons with related work, we will assume in this section a Chord-based application that maps keys onto values. A value can be an add ...
... Three features that distinguish Chord from many other peer-to-peer lookup protocols are its simplicity, provable correctness, and provable performance. To clarify comparisons with related work, we will assume in this section a Chord-based application that maps keys onto values. A value can be an add ...
CIS 175 Lecture Notes
... 2 Explosive growth 3 Internet 4 Economic impact 5 Complexity 6 Abstractions and concepts 7 On-line resources ...
... 2 Explosive growth 3 Internet 4 Economic impact 5 Complexity 6 Abstractions and concepts 7 On-line resources ...
Computer Networks and Internets By Douglas E Comer
... 2 Explosive growth 3 Internet 4 Economic impact 5 Complexity 6 Abstractions and concepts 7 On-line resources ...
... 2 Explosive growth 3 Internet 4 Economic impact 5 Complexity 6 Abstractions and concepts 7 On-line resources ...
Ch. 3
... – ID = sequential number that identifies the challenge. – random = a reasonably random number generated by the router. – HQ = the authentication name of the challenger. 2. The ID and random values are kept on the called router. 3. The challenge packet is sent to the calling router. A list of outstan ...
... – ID = sequential number that identifies the challenge. – random = a reasonably random number generated by the router. – HQ = the authentication name of the challenger. 2. The ID and random values are kept on the called router. 3. The challenge packet is sent to the calling router. A list of outstan ...
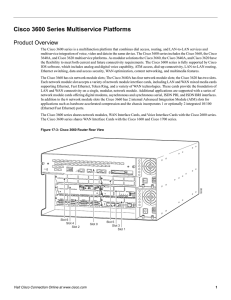
Cisco 3600 Series Multiservice Platforms
... ISDN BRI networks For areas of the world where ISDN BRI services are more widely available or cost effective, the Cisco 3600 series supports many BRI interfaces. Configured with a LAN network module and three 8-port network modules, a Cisco 3640A connects up to 48 B channels. In this way, one system ...
... ISDN BRI networks For areas of the world where ISDN BRI services are more widely available or cost effective, the Cisco 3600 series supports many BRI interfaces. Configured with a LAN network module and three 8-port network modules, a Cisco 3640A connects up to 48 B channels. In this way, one system ...
Serial Server Installation Guide
... frequency energy, and if not installed and used in accordance with this guide, may cause harmful interference to radio communications. Operation of this equipment in a residential area is likely to cause interference in which case the user, at his or her own expense, will be required to take whateve ...
... frequency energy, and if not installed and used in accordance with this guide, may cause harmful interference to radio communications. Operation of this equipment in a residential area is likely to cause interference in which case the user, at his or her own expense, will be required to take whateve ...
Overlay Network
... • An overlay socket (OL Socket) is an endpoint for communication in an overlay network • An overlay socket provides application programs an interface for communications over an overlay network • The application programming interface (API) of an OL Socket offers applications the ability to • create o ...
... • An overlay socket (OL Socket) is an endpoint for communication in an overlay network • An overlay socket provides application programs an interface for communications over an overlay network • The application programming interface (API) of an OL Socket offers applications the ability to • create o ...
ITN_instructorPPT_Chapter8
... • Multicast - the process of sending a packet from one host to a selected group of hosts, possibly in different networks ...
... • Multicast - the process of sending a packet from one host to a selected group of hosts, possibly in different networks ...
Ch. 13 - PPP
... – ID = sequential number that identifies the challenge. – random = a reasonably random number generated by the router. – HQ = the authentication name of the challenger. 2. The ID and random values are kept on the called router. 3. The challenge packet is sent to the calling router. A list of outstan ...
... – ID = sequential number that identifies the challenge. – random = a reasonably random number generated by the router. – HQ = the authentication name of the challenger. 2. The ID and random values are kept on the called router. 3. The challenge packet is sent to the calling router. A list of outstan ...
ccna4-mod1-ScalingIPAddress
... • NAT is designed to conserve IP addresses and enable networks to use ...
... • NAT is designed to conserve IP addresses and enable networks to use ...
Datagram
... • The physical and data link layers of a network operate locally. These two layers are jointly responsible for data delivery on the network from one node to the next, as shown in Figure 20.1. • طبقتي ربط البيانات والفيزيائية تعمالن بشكل محلي وهاتان الطبقتان معا مسئولتان عن تسليم : البيانات على ال ...
... • The physical and data link layers of a network operate locally. These two layers are jointly responsible for data delivery on the network from one node to the next, as shown in Figure 20.1. • طبقتي ربط البيانات والفيزيائية تعمالن بشكل محلي وهاتان الطبقتان معا مسئولتان عن تسليم : البيانات على ال ...
Administrator`s Handbook for the Motorola 3347
... The PPPoE specification, incorporating the PPP and Ethernet standards, allows your computer(s) to connect to your Service Provider’s network through your Ethernet WAN connection. The 2200 and 3300-series Gateway supports PPPoE, eliminating the need to install PPPoE client software on any LAN compute ...
... The PPPoE specification, incorporating the PPP and Ethernet standards, allows your computer(s) to connect to your Service Provider’s network through your Ethernet WAN connection. The 2200 and 3300-series Gateway supports PPPoE, eliminating the need to install PPPoE client software on any LAN compute ...