ProLiant Essentials Intelligent Networking Pack Windows Edition
... NOTE: For use with a single server. Contains one license with a unique license activation key and documentation ProLiant Essentials Intelligent Networking Pack, Flexible License NOTE: For use with multiple servers (minimum of 5). This part number allows you to specify the license quantity. When orde ...
... NOTE: For use with a single server. Contains one license with a unique license activation key and documentation ProLiant Essentials Intelligent Networking Pack, Flexible License NOTE: For use with multiple servers (minimum of 5). This part number allows you to specify the license quantity. When orde ...
Compatible Systems Reference Guides
... Introduction The default passwords as shipped from the factory are letmein. It is strongly recommended that the password be changed using the [ General ] section. Once the passwords are set, the same passwords are used by CompatiView. Modes of Operation There are two modes of operation in the Comma ...
... Introduction The default passwords as shipped from the factory are letmein. It is strongly recommended that the password be changed using the [ General ] section. Once the passwords are set, the same passwords are used by CompatiView. Modes of Operation There are two modes of operation in the Comma ...
datagram network
... Dynamic Host Configuration Protocol (DHCP) – DHCP sets the host IP address, the subnet mask, defines the first-hop router (default gateway), and local DNS server – DHCP is often known as a plug-and-play protocol, because it makes network admin much easier! INFO 203 week 7 ...
... Dynamic Host Configuration Protocol (DHCP) – DHCP sets the host IP address, the subnet mask, defines the first-hop router (default gateway), and local DNS server – DHCP is often known as a plug-and-play protocol, because it makes network admin much easier! INFO 203 week 7 ...
Gnutella2: A Better Gnutella?
... response messages since Gnutella2's method allows the responding node to directly contact the requesting node, rather than sending the message back through the path to ...
... response messages since Gnutella2's method allows the responding node to directly contact the requesting node, rather than sending the message back through the path to ...
Customizable virtual private network service with QoS
... network infrastructure amongst multiple VPNs. The ubiquity of the Internet makes it an ideal infrastructure for providing the VPN service. Fig. 1 illustrates the situation where two dierent VPN topologies are created on top of the same underlying shared network infrastructure. Various forms of priv ...
... network infrastructure amongst multiple VPNs. The ubiquity of the Internet makes it an ideal infrastructure for providing the VPN service. Fig. 1 illustrates the situation where two dierent VPN topologies are created on top of the same underlying shared network infrastructure. Various forms of priv ...
4.2 TCP Handoff implementation - The Linux Virtual Server Project
... In popular cluster-based Web server scheduling techniques, content-aware scheduling is a popular scheduling technique, it has many advantages. But the existing systems have low scalability, scheduler performance bottleneck problem, which lead to the advantages can not be fully exerted. TCP Handoff i ...
... In popular cluster-based Web server scheduling techniques, content-aware scheduling is a popular scheduling technique, it has many advantages. But the existing systems have low scalability, scheduler performance bottleneck problem, which lead to the advantages can not be fully exerted. TCP Handoff i ...
downloading
... Can be confusing at first Consider this example: Two 100 Mbps circuits - 1 km of optic fiber - Via satellite with a distance of 30 km between the base and the satellite ...
... Can be confusing at first Consider this example: Two 100 Mbps circuits - 1 km of optic fiber - Via satellite with a distance of 30 km between the base and the satellite ...
Using Your Gateway WGR
... Insert the CD into the disc drive on the computer attached to your broadband modem. If the The Gateway Wireless-G Access Point/Router Setup Wizard opens, go to Step 5. - OR If the wizard does not start automatically, go to Step 2. ...
... Insert the CD into the disc drive on the computer attached to your broadband modem. If the The Gateway Wireless-G Access Point/Router Setup Wizard opens, go to Step 5. - OR If the wizard does not start automatically, go to Step 2. ...
Where is the collision domain?
... Connect LANs and WANs with similar or different protocols together Switches and bridges isolate collision domains but forward broadcast messages to all LANs connected to them. Routers isolate both collision domains and broadcast domains Acts like normal stations on a network, but have more than one ...
... Connect LANs and WANs with similar or different protocols together Switches and bridges isolate collision domains but forward broadcast messages to all LANs connected to them. Routers isolate both collision domains and broadcast domains Acts like normal stations on a network, but have more than one ...
Chapter 6: The Transport Layer
... • (a) At t = 0, (b) After 500 μsec, (c) After 20 msec, (d) after 40 ...
... • (a) At t = 0, (b) After 500 μsec, (c) After 20 msec, (d) after 40 ...
DSL-504T ADSL Router User’s Guide
... shall be to replace the non-conforming Software (or defective media) with software that substantially conforms to D-Link’s functional specifications for the Software or to refund at D-Link’s sole discretion. Except as otherwise agreed by D-Link in writing, the replacement Software is provided only t ...
... shall be to replace the non-conforming Software (or defective media) with software that substantially conforms to D-Link’s functional specifications for the Software or to refund at D-Link’s sole discretion. Except as otherwise agreed by D-Link in writing, the replacement Software is provided only t ...
OSPF
... the command ip ospf hello-interval. RouterDeadInterval - The period in seconds that the router will wait to hear a Hello from a neighbor before declaring the neighbor down. Cisco ...
... the command ip ospf hello-interval. RouterDeadInterval - The period in seconds that the router will wait to hear a Hello from a neighbor before declaring the neighbor down. Cisco ...
slides - network systems lab @ sfu
... •Using this protocol, peers can advertise their own resources, network service, identity, and discover the resources from other peers • Peer resources are published using XML-based metadata format ...
... •Using this protocol, peers can advertise their own resources, network service, identity, and discover the resources from other peers • Peer resources are published using XML-based metadata format ...
OfficeConnect ADSL Wireless 11g Firewall Router User Guide
... anyone outside of your network from seeing your files or damaging your computers. The Router can also prevent your users from accessing Web sites which you find unsuitable. Figure 1 shows an example network without a Router. In this network, only one computer is connected to the Internet. This compu ...
... anyone outside of your network from seeing your files or damaging your computers. The Router can also prevent your users from accessing Web sites which you find unsuitable. Figure 1 shows an example network without a Router. In this network, only one computer is connected to the Internet. This compu ...
Chapter14 (Unicast Routing Protocols)
... 14.7 BGP Border Gateway Protocol is an interdomain routing protocol using path vector routing Distance vector routing and link state routing distance vector routing : just considering the number of hops link state routing : requiring each router to have a huge link ...
... 14.7 BGP Border Gateway Protocol is an interdomain routing protocol using path vector routing Distance vector routing and link state routing distance vector routing : just considering the number of hops link state routing : requiring each router to have a huge link ...
IP CIP compared to other NonStop TCP/IP products – Technical
... Each conventional TCP/IP process is a separate protocol stack, so you are not limited to connecting a NonStop system to just one network, but can run multiple TCP/IP processes and then connect the system to multiple independent networks, where the hosts on each network have routes to all other hosts ...
... Each conventional TCP/IP process is a separate protocol stack, so you are not limited to connecting a NonStop system to just one network, but can run multiple TCP/IP processes and then connect the system to multiple independent networks, where the hosts on each network have routes to all other hosts ...
Layer 2 Technologies
... on which a frame needs to be transmitted. • Switches often replace shared hubs and work with existing cable infrastructures. • Higher speeds than bridges. ...
... on which a frame needs to be transmitted. • Switches often replace shared hubs and work with existing cable infrastructures. • Higher speeds than bridges. ...
Exploration CCNA4 - College of DuPage
... addresses over the Internet, and there are not enough public addresses to allow organizations to provide one to every one of their hosts, networks need a mechanism to translate private addresses to public addresses at the edge of their network that works in both directions. – Without a translation s ...
... addresses over the Internet, and there are not enough public addresses to allow organizations to provide one to every one of their hosts, networks need a mechanism to translate private addresses to public addresses at the edge of their network that works in both directions. – Without a translation s ...
The Allied Telesis x610 Series is the high performing and... solution for today’s networks, providing an extensive range of
... modules are available for local and long-distance stacking. Long-distance expansion modules can be configured to provide two additional 10G ports. Flexible endpoint deployment is ensured with the ability to power devices such as IP phones, security cameras, and wireless access points directly from t ...
... modules are available for local and long-distance stacking. Long-distance expansion modules can be configured to provide two additional 10G ports. Flexible endpoint deployment is ensured with the ability to power devices such as IP phones, security cameras, and wireless access points directly from t ...
CS610 Final term MAGA file.. all paperz are in 1 file..pages 1 to 42
... ( Marks: 1 ) - Please choose one Although message exchange can be used to bind addresses, sending a request for each binding is hopelessly inefficient. ► True ► False Question No: 22 ( Marks: 1 ) - Please choose one Address mask defines how many bits of address are in suffix? ► True ► False Question ...
... ( Marks: 1 ) - Please choose one Although message exchange can be used to bind addresses, sending a request for each binding is hopelessly inefficient. ► True ► False Question No: 22 ( Marks: 1 ) - Please choose one Address mask defines how many bits of address are in suffix? ► True ► False Question ...
WRC-1000 Wireless Routing Center
... far below the FCC radio frequency exposure limits. Nevertheless, the TOSHIBA Wireless Routing Center WRC-1000 shall be used in such a manner that the potential for human contact during normal operation is minimized. When using this device, a certain separation distance between antenna and nearby per ...
... far below the FCC radio frequency exposure limits. Nevertheless, the TOSHIBA Wireless Routing Center WRC-1000 shall be used in such a manner that the potential for human contact during normal operation is minimized. When using this device, a certain separation distance between antenna and nearby per ...
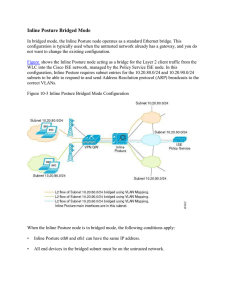
15360608-Inline Posture Bridged Mode
... Authorization policies provide the means for controlling access to the network and its resources. Cisco ISE lets you define a number of different authorization policies. The elements that define the authorization policy are referenced when you create policy rules. Your choice of conditions and attri ...
... Authorization policies provide the means for controlling access to the network and its resources. Cisco ISE lets you define a number of different authorization policies. The elements that define the authorization policy are referenced when you create policy rules. Your choice of conditions and attri ...
MRP: Wireless mesh networks routing protocol Jangeun Jun, Mihail L. Sichitiu
... and allowing them to forward each other’s packets to and from a common gateway (another AP connected to the distribution system). The main drawback of these deployments is the reduced bandwidth available to the users (this can become a major problem in scenarios with many active users [20]). Some co ...
... and allowing them to forward each other’s packets to and from a common gateway (another AP connected to the distribution system). The main drawback of these deployments is the reduced bandwidth available to the users (this can become a major problem in scenarios with many active users [20]). Some co ...
Collection Tree Protocol
... protocol benefits almost every sensor network application today, as well as the many transport, routing, overlay, and application protocols that sit on top of collection trees. At first glance, collection protocols may appear very simple. They provide best-effort, unreliable, anycast packet delivery ...
... protocol benefits almost every sensor network application today, as well as the many transport, routing, overlay, and application protocols that sit on top of collection trees. At first glance, collection protocols may appear very simple. They provide best-effort, unreliable, anycast packet delivery ...
Configuring Network Address Translation: Getting Started
... Dynamic NAT is useful when fewer addresses are available than the actual number of hosts to be translated. It creates an entry in the NAT table when the host initiates a connection and establishes a one-to-one mapping between the addresses. But, the mapping can vary and it depends upon the registere ...
... Dynamic NAT is useful when fewer addresses are available than the actual number of hosts to be translated. It creates an entry in the NAT table when the host initiates a connection and establishes a one-to-one mapping between the addresses. But, the mapping can vary and it depends upon the registere ...