Ch19v2.0
... • To add an entry Search probe sequence same as for retrieval Note first available slot Use available slot if the key is not found ...
... • To add an entry Search probe sequence same as for retrieval Note first available slot Use available slot if the key is not found ...
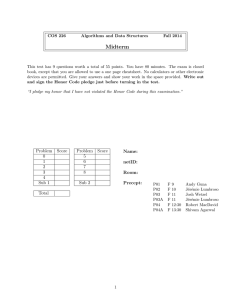
Midterm
... Assuming that the initial size of the hash table was 7 and that it did not grow or shrink, circle all possible keys that could have been the last key inserted. ...
... Assuming that the initial size of the hash table was 7 and that it did not grow or shrink, circle all possible keys that could have been the last key inserted. ...
Lecture 27
... Problem: Find the best way to multiply n matrices (where best means the one that uses the minimum number of scalar multiplications). Practical use: Computer Graphics (Long chains of matrices). Digital Signal processing: applying filters to signals, etc. Formally: Given are n matr ...
... Problem: Find the best way to multiply n matrices (where best means the one that uses the minimum number of scalar multiplications). Practical use: Computer Graphics (Long chains of matrices). Digital Signal processing: applying filters to signals, etc. Formally: Given
Scripting languages
... coded in a similar fashion to C++ (which is a programming language. • JavaScript is much simpler to use than Java. No compiling, no applets, just a simple sequence. ...
... coded in a similar fashion to C++ (which is a programming language. • JavaScript is much simpler to use than Java. No compiling, no applets, just a simple sequence. ...
h + 1
... 62. 2 is empty, therefore 62 is not in the hash table. 63. 3 is empty, therefore 63 is not in the hash table. 64. Searching for 64, we check 4, 4 + 1 ≡ 5, and 4 + 4 ≡ 8, and 64 is located in 8, and therefore 64 is in the hash table. 65. Searching for 65, we check 5 and 5 + 1 ≡ 6 and 6 is empty. Ther ...
... 62. 2 is empty, therefore 62 is not in the hash table. 63. 3 is empty, therefore 63 is not in the hash table. 64. Searching for 64, we check 4, 4 + 1 ≡ 5, and 4 + 4 ≡ 8, and 64 is located in 8, and therefore 64 is in the hash table. 65. Searching for 65, we check 5 and 5 + 1 ≡ 6 and 6 is empty. Ther ...
Data Structures Part 2
... printf( "%d not inserted. No memory available.\n", info ); }/*end else*/ } /* end function push */ In the main : Stack * stackPtr = NULL; /* points to stack top */ ...
... printf( "%d not inserted. No memory available.\n", info ); }/*end else*/ } /* end function push */ In the main : Stack * stackPtr = NULL; /* points to stack top */ ...
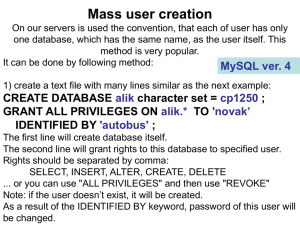
GRANT ALL PRIVILEGES ON alik.* TO `novak`
... This is important to prepare this file in such directory, that the name including path can be easy written (the desktop address is very complicated to be written). Note: in the Windows XP command line prompt, you cannot use the Ctrl+C and Ctrl+V commands. Using Linux and the “putty” program, you can ...
... This is important to prepare this file in such directory, that the name including path can be easy written (the desktop address is very complicated to be written). Note: in the Windows XP command line prompt, you cannot use the Ctrl+C and Ctrl+V commands. Using Linux and the “putty” program, you can ...
ppt
... Always use the first “good” one If neither are good, rehash at every deletion If not using 1, keep a top-level table for it for easy “goodness” checking (likewise for 2) ...
... Always use the first “good” one If neither are good, rehash at every deletion If not using 1, keep a top-level table for it for easy “goodness” checking (likewise for 2) ...
Remote Access
... • A capitalized letter or punctuation or non-alphanumeric character (e.g. !@#*+) Avoid words found in any dictionary (including medical, foreign language) Shall not contain the user login-name (UserID) o For example, passwords constructed from the first letter of words from the title of a favori ...
... • A capitalized letter or punctuation or non-alphanumeric character (e.g. !@#*+) Avoid words found in any dictionary (including medical, foreign language) Shall not contain the user login-name (UserID) o For example, passwords constructed from the first letter of words from the title of a favori ...
Operating System Security Fundamentals
... User Administration (continued) Best practices (continued): Create a specific file system for users Educate users on how to select a password Lock non-used accounts Grant privileges on a per host basis Do not grant privileges to all machines Use ssh, scp, and Secure FTP Isolate a system after a com ...
... User Administration (continued) Best practices (continued): Create a specific file system for users Educate users on how to select a password Lock non-used accounts Grant privileges on a per host basis Do not grant privileges to all machines Use ssh, scp, and Secure FTP Isolate a system after a com ...
Searching Very Large Routing Tables in Wide - CSIE -NCKU
... them by an atomic write operation. If power-of-2 table sizes are enforced, which matches very well with a buddy system. Otherwise, if memory fragmentation were to become a problem, then the BARTS scheme can be adapted to use fewer buffer sizes by reducing the segment size s. A suboptimum compressi ...
... them by an atomic write operation. If power-of-2 table sizes are enforced, which matches very well with a buddy system. Otherwise, if memory fragmentation were to become a problem, then the BARTS scheme can be adapted to use fewer buffer sizes by reducing the segment size s. A suboptimum compressi ...
empty table
... Step two – generate an address from the key value • Division by table size • Folding – The key is divided into sections, and the sections are added together. – if Key = 013402122 ; hash(Key) = 013+402+122 = 537 – addition, subtraction and multiplication could be used • Midsquare – square the key and ...
... Step two – generate an address from the key value • Division by table size • Folding – The key is divided into sections, and the sections are added together. – if Key = 013402122 ; hash(Key) = 013+402+122 = 537 – addition, subtraction and multiplication could be used • Midsquare – square the key and ...
CS163_Topic6
... search key into a unique index into our table. • This would be considered a perfect hash function. But, it is only possible to construct perfect hash functions if we can afford to have a unique entry in our table for each search key -- which is not typically the case. • This means that a typical has ...
... search key into a unique index into our table. • This would be considered a perfect hash function. But, it is only possible to construct perfect hash functions if we can afford to have a unique entry in our table for each search key -- which is not typically the case. • This means that a typical has ...
pps - AquaLab - Northwestern University
... • Ping a range of IP addresses (43-bit, in dotted decimal notation w.x.y.z, each in [0,255]) , try telnet’ing to it • If you are in, get /etc/passwd and build stats on login names EECS 343 Operating Systems Northwestern University ...
... • Ping a range of IP addresses (43-bit, in dotted decimal notation w.x.y.z, each in [0,255]) , try telnet’ing to it • If you are in, get /etc/passwd and build stats on login names EECS 343 Operating Systems Northwestern University ...
Hashing and Packet Based Algorithms
... another choice, without affecting lookups. • As long as hash values can be recomputed. ...
... another choice, without affecting lookups. • As long as hash values can be recomputed. ...
Midterm Solutions
... (a) Color flip 24 (b) Rotate 18 left; rotate 22 left; rotate 26 right; rotate 28 right. The full sequence of elementary operations is: • Rotate 26 right • Color flip 24 • Rotate 22 left • Rotate 28 right • Color flip 24 • Rotate 18 left ...
... (a) Color flip 24 (b) Rotate 18 left; rotate 22 left; rotate 26 right; rotate 28 right. The full sequence of elementary operations is: • Rotate 26 right • Color flip 24 • Rotate 22 left • Rotate 28 right • Color flip 24 • Rotate 18 left ...
Hashing - METU Computer Engineering
... deletions and finds in constant average time (i.e. O(1)) • This data structure, however, is not efficient in operations that require any ordering information among the elements, such as findMin, findMax and printing the entire table in sorted order. • It uses a table consisting of pairs ...
... deletions and finds in constant average time (i.e. O(1)) • This data structure, however, is not efficient in operations that require any ordering information among the elements, such as findMin, findMax and printing the entire table in sorted order. • It uses a table consisting of
Hash Table Functions Redouan Lahmyed*, Parid Weasamae*, Said
... can find the value by simply looking up A[i]. The idea of a hash table is more generalized and can be described as follows. The concept of a hash table is a generalized idea of an array where key does not have to be an integer. We can have a name as a key, or for that matter any object as the key. T ...
... can find the value by simply looking up A[i]. The idea of a hash table is more generalized and can be described as follows. The concept of a hash table is a generalized idea of an array where key does not have to be an integer. We can have a name as a key, or for that matter any object as the key. T ...
Introduction to Hash Tables
... •For example MyHash.find(); or This_Hash.definekey(‘empid’); • Hashes can only be used in a Data Step procedure or DS2 program. • In SAS the user is shielded from most of the implementation details. •You don’t need to know anything about the hash function used or collision ...
... •For example MyHash.find(); or This_Hash.definekey(‘empid’); • Hashes can only be used in a Data Step procedure or DS2 program. • In SAS the user is shielded from most of the implementation details. •You don’t need to know anything about the hash function used or collision ...
Rainbow table
A rainbow table is a precomputed table for reversing cryptographic hash functions, usually for cracking password hashes. Tables are usually used in recovering a plaintext password up to a certain length consisting of a limited set of characters. It is a practical example of a space/time trade-off, using less computer processing time and more storage than a brute-force attack which calculates a hash on every attempt, but more processing time and less storage than a simple lookup table with one entry per hash. Use of a key derivation function that employs a salt makes this attack infeasible.Rainbow tables are an application of an earlier, simpler algorithm by Martin Hellman.