Hashing hash functions collision resolution
... 2. Collision resolution: Algorithm and data structure to handle two keys that hash to the same index. 3. Equality test: Method for checking whether two keys are equal. Classic space-time tradeoff. No space limitation: trivial hash function with key as address. No time limitation: trivial collision r ...
... 2. Collision resolution: Algorithm and data structure to handle two keys that hash to the same index. 3. Equality test: Method for checking whether two keys are equal. Classic space-time tradeoff. No space limitation: trivial hash function with key as address. No time limitation: trivial collision r ...
Cryptography for IoT
... Designed specifically for constrained devices such as RFID tags and networked sensors (hardware oriented). ...
... Designed specifically for constrained devices such as RFID tags and networked sensors (hardware oriented). ...
12_Auth_nemo
... • Idea: random challenges enciphered, so attacker cannot verify correct decipherment of challenge • Assume Alice, Bob share secret password s • In what follows, Alice needs to generate a random public key p and a corresponding private key q • Also, k is a randomly generated session key, and RA and R ...
... • Idea: random challenges enciphered, so attacker cannot verify correct decipherment of challenge • Assume Alice, Bob share secret password s • In what follows, Alice needs to generate a random public key p and a corresponding private key q • Also, k is a randomly generated session key, and RA and R ...
Data structures and web filtering
... • README.txt: This file should contain your name, your NetID, all known issues you have with your submitted code, and the names of anyone you have discussed the homework with. You should briefly describe and justify your design, noting any interesting design decisions you encountered. • perf.txt or ...
... • README.txt: This file should contain your name, your NetID, all known issues you have with your submitted code, and the names of anyone you have discussed the homework with. You should briefly describe and justify your design, noting any interesting design decisions you encountered. • perf.txt or ...
DHTs
... – We can have r different coordinate spaces – Nodes hold a zone in each of them – Creates r replicas of the (key, value) pairs – Increases robustness – Reduces path length as search can be continued in the reality where the target is closest • Overloading zones – Different peers are responsible for ...
... – We can have r different coordinate spaces – Nodes hold a zone in each of them – Creates r replicas of the (key, value) pairs – Increases robustness – Reduces path length as search can be continued in the reality where the target is closest • Overloading zones – Different peers are responsible for ...
Chapter9
... • Overflow – No longer a concern • Data stored in linked lists • Memory space to store data allocated dynamically ...
... • Overflow – No longer a concern • Data stored in linked lists • Memory space to store data allocated dynamically ...
Do Loop
... • Use a Button to accept the “print table” command from the user • Use a List Box to show the multiplication ...
... • Use a Button to accept the “print table” command from the user • Use a List Box to show the multiplication ...
Lecture 16 - Suraj @ LUMS
... deciphering routine • At instruction level: substitute instructions • At algorithm level: different algorithms to achieve the same purpose • Toolkits to make these exist (Mutation Engine, Trident Polymorphic Engine) ...
... deciphering routine • At instruction level: substitute instructions • At algorithm level: different algorithms to achieve the same purpose • Toolkits to make these exist (Mutation Engine, Trident Polymorphic Engine) ...
B Trees
... An index is an ordered list of all the values that reside in a group of one or more columns at a given time. Such a list makes queries that test the values in those columns vastly more efficient. Indexes also take up storage space, and must be changed whenever the data is, so a cost-benefit analys ...
... An index is an ordered list of all the values that reside in a group of one or more columns at a given time. Such a list makes queries that test the values in those columns vastly more efficient. Indexes also take up storage space, and must be changed whenever the data is, so a cost-benefit analys ...
Lists, Hash Tables, Trees - NEMCC Math/Science Division
... For example: Use some function to reduce the address space of a billion possible SocSecNums to the population size of 100 students. Hash Function: The function by which you shrink the address space, e.g, ...
... For example: Use some function to reduce the address space of a billion possible SocSecNums to the population size of 100 students. Hash Function: The function by which you shrink the address space, e.g, ...
Solutions
... a. What is a hash function? A function to generate a number from a key b. What is a desirable property of hash functions? Numbers generated from keys are spread out uniformly in a range c. What is a perfect hash function? Every key is assigned a unique number d. What is a collision? Identical numbe ...
... a. What is a hash function? A function to generate a number from a key b. What is a desirable property of hash functions? Numbers generated from keys are spread out uniformly in a range c. What is a perfect hash function? Every key is assigned a unique number d. What is a collision? Identical numbe ...
$doc.title
... max with a heap is constant time, but in an LLRB it is logarithmic time (though this can be trivially fixed by adding an extra instance variable to an LLRB based PQ). ii. Yes, a max heap us ...
... max with a heap is constant time, but in an LLRB it is logarithmic time (though this can be trivially fixed by adding an extra instance variable to an LLRB based PQ). ii. Yes, a max heap us ...
Midterm Solutions
... The inner loop gets executed N 3 times. It consists of two additions and one comparison; the innermost for loop also does one increment and one comparison. This is a total of 5N 3 instructions. The outer and middle loops are inconsequential – O(N ) and O(N 2 ) instructions, respectively. (a) Estimat ...
... The inner loop gets executed N 3 times. It consists of two additions and one comparison; the innermost for loop also does one increment and one comparison. This is a total of 5N 3 instructions. The outer and middle loops are inconsequential – O(N ) and O(N 2 ) instructions, respectively. (a) Estimat ...
Data Structures and Text Editing
... In addition to the code you write for data structures and the text editor plugins, you should also submit any tests that you write. Testing is a component of the grade for this assignment. You should implement your test cases using JUnit, a framework for writing test suites. JUnit has excellent Ecli ...
... In addition to the code you write for data structures and the text editor plugins, you should also submit any tests that you write. Testing is a component of the grade for this assignment. You should implement your test cases using JUnit, a framework for writing test suites. JUnit has excellent Ecli ...
Introduction to MS Access
... Primary Key • Each customer number in Customer table must be unique, so that you can distinguish one customer from one another. • The customer number field is the Primary Key of the Customer table. • A Primary Key is a field or collection of fields whose values uniquely identify each record in a ta ...
... Primary Key • Each customer number in Customer table must be unique, so that you can distinguish one customer from one another. • The customer number field is the Primary Key of the Customer table. • A Primary Key is a field or collection of fields whose values uniquely identify each record in a ta ...
pptx - Chair of Software Engineering
... Removal: remove an occurrence (if any) of an item Wipeout: remove all occurrences of an item Search: find out if a given item is present Iteration (or “traversal”): apply a given operation to every item Various container implementations, as studied next, determine: Which of these operation ...
... Removal: remove an occurrence (if any) of an item Wipeout: remove all occurrences of an item Search: find out if a given item is present Iteration (or “traversal”): apply a given operation to every item Various container implementations, as studied next, determine: Which of these operation ...
Lecture No. 41 - Taleem-E
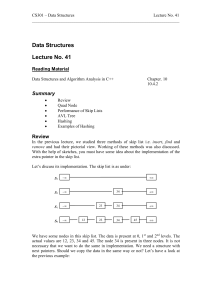
... search before the insertion. However for an unsorted list, a programmer will insert the item in the start. Similarly we have seen the data structure where insertions, deletions and searches are proportional to n. In link list, insertions and deletions are proportional to n whereas search is log n. I ...
... search before the insertion. However for an unsorted list, a programmer will insert the item in the start. Similarly we have seen the data structure where insertions, deletions and searches are proportional to n. In link list, insertions and deletions are proportional to n whereas search is log n. I ...
Access Queries
... Each value in a field has very specific data coded for a computer to read. Humans can discern vague similarities and differences among data fairly easily. Computers are more exacting. Computers need you to tell them when data is a date, or a character, or a number. A zero is not the same as a blank ...
... Each value in a field has very specific data coded for a computer to read. Humans can discern vague similarities and differences among data fairly easily. Computers are more exacting. Computers need you to tell them when data is a date, or a character, or a number. A zero is not the same as a blank ...
Access Queries - College of Business
... Each value in a field has very specific data coded for a computer to read. Humans can discern vague similarities and differences among data fairly easily. Computers are more exacting. Computers need you to tell them when data is a date, or a character, or a number. A zero is not the same as a blank ...
... Each value in a field has very specific data coded for a computer to read. Humans can discern vague similarities and differences among data fairly easily. Computers are more exacting. Computers need you to tell them when data is a date, or a character, or a number. A zero is not the same as a blank ...
Storing a Compressed Function with Constant Time Access
... values is not much larger than the number of values n. Ignoring this term, the number of bits per character is at most H0 (a lower bound) times 1 + δ, plus a small additive term. This is similar to the space that would be obtained by Huffman coding the sequence of function values (with no random acc ...
... values is not much larger than the number of values n. Ignoring this term, the number of bits per character is at most H0 (a lower bound) times 1 + δ, plus a small additive term. This is similar to the space that would be obtained by Huffman coding the sequence of function values (with no random acc ...
Binary Trees and Hash Tables
... • If the slot determined by the hash function is full, linearly search down the array for the next empty ...
... • If the slot determined by the hash function is full, linearly search down the array for the next empty ...
K - CS1001.py
... • If we are able to make sure that the tree is always balanced, we will have an efficient way to store and search data. But we can observe that the shape of the tree depends on the sequence of inserts that generated the tree. • There are several variations of balanced binary search trees, such as AV ...
... • If we are able to make sure that the tree is always balanced, we will have an efficient way to store and search data. But we can observe that the shape of the tree depends on the sequence of inserts that generated the tree. • There are several variations of balanced binary search trees, such as AV ...
Elementary Data Structures and Hash Tables
... All direct-address table operations are O(1)! So why isn’t every set implemented with a direct-address table? The space complexity is Θ(`U`) ...
... All direct-address table operations are O(1)! So why isn’t every set implemented with a direct-address table? The space complexity is Θ(`U`) ...
Rainbow table
A rainbow table is a precomputed table for reversing cryptographic hash functions, usually for cracking password hashes. Tables are usually used in recovering a plaintext password up to a certain length consisting of a limited set of characters. It is a practical example of a space/time trade-off, using less computer processing time and more storage than a brute-force attack which calculates a hash on every attempt, but more processing time and less storage than a simple lookup table with one entry per hash. Use of a key derivation function that employs a salt makes this attack infeasible.Rainbow tables are an application of an earlier, simpler algorithm by Martin Hellman.