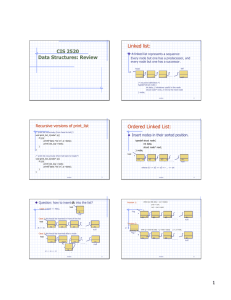
CIS 2520 Data Structures: Review Linked list: Ordered Linked List:
... Dijkstra’s Algorithm n Similar to MST algorithms n Key step is sort on the edges n Complexity is w O( (|E|+|V|)log|V| ) or w O( n 2 log n ) for a dense graph with n = |V| and |E| ≈ |V|2 ...
... Dijkstra’s Algorithm n Similar to MST algorithms n Key step is sort on the edges n Complexity is w O( (|E|+|V|)log|V| ) or w O( n 2 log n ) for a dense graph with n = |V| and |E| ≈ |V|2 ...
Optimizing Hash-Array Mapped Tries for Fast and Lean Immutable
... (cf. Figure 3b): one array holding sub-node references, and another one holding values. This split effectively reorders the elements, while the ordering within each group remains. The element order is irrelevant anyway in already unordered set and map data structures. We remove the need for using in ...
... (cf. Figure 3b): one array holding sub-node references, and another one holding values. This split effectively reorders the elements, while the ordering within each group remains. The element order is irrelevant anyway in already unordered set and map data structures. We remove the need for using in ...
1. Basic Operations (6 Points). a. To the right of the BST below, draw
... Task 3) Read in a large number of grayscale images, and display all of the unique images. The images may be displayed in any order. Each image is stored as a Picture object that contains image data stored as an int[][]variable, all of which are 512 x 512 (i.e. have a width and height of 512). Give t ...
... Task 3) Read in a large number of grayscale images, and display all of the unique images. The images may be displayed in any order. Each image is stored as a Picture object that contains image data stored as an int[][]variable, all of which are 512 x 512 (i.e. have a width and height of 512). Give t ...
ICOM4015-lec18
... Reduce it modulo the table size • Iterate through the elements of the bucket at position h For each element of the bucket, check whether it is equal to x • If a match is found among the elements of that bucket, then x is in the set Otherwise, x is not in the set ...
... Reduce it modulo the table size • Iterate through the elements of the bucket at position h For each element of the bucket, check whether it is equal to x • If a match is found among the elements of that bucket, then x is in the set Otherwise, x is not in the set ...
SELECT CustomerName
... Use the INNER JOIN to join a table to itself The AS word must be used to give each table a distinct name so that references to columns can be made unique Example: SELECT E.EmployeeName,M.EmployeeName FROM Personnel AS E INNER JOIN Personnel as M ON E.ManagerID = M.EmployeeID ...
... Use the INNER JOIN to join a table to itself The AS word must be used to give each table a distinct name so that references to columns can be made unique Example: SELECT E.EmployeeName,M.EmployeeName FROM Personnel AS E INNER JOIN Personnel as M ON E.ManagerID = M.EmployeeID ...
sorted
... Linear Search - example L = range( 1, 11 ) # fill w/numbers 1-10 random.shuffle( L ) # mix it up target = 7 # we're looking for 7 i = 0 while i < len( L ) and not bFound : if L[i] == target : break i += 1 if i < len( L ) : # we found it! print str(target) + \ " was found at index " + str(i) ...
... Linear Search - example L = range( 1, 11 ) # fill w/numbers 1-10 random.shuffle( L ) # mix it up target = 7 # we're looking for 7 i = 0 while i < len( L ) and not bFound : if L[i] == target : break i += 1 if i < len( L ) : # we found it! print str(target) + \ " was found at index " + str(i) ...
Normalization of Database Tables
... the BCNF are equivalent. • BCNF is a special case of 3NF. • Figure 5.7 illustrates a table that is in 3NF but not in BCNF. • Figure 5.8 shows how the table can be decomposed to conform to the BCNF form. ...
... the BCNF are equivalent. • BCNF is a special case of 3NF. • Figure 5.7 illustrates a table that is in 3NF but not in BCNF. • Figure 5.8 shows how the table can be decomposed to conform to the BCNF form. ...
Principles of Dimensional Modelling
... Advantages and disadvantages Advantages Small savings in storage space Normalized structures are easier to update and maintain Disadvantages Schema is less intuitive Browsing becomes difficult Degraded query performance because of additional joins ...
... Advantages and disadvantages Advantages Small savings in storage space Normalized structures are easier to update and maintain Disadvantages Schema is less intuitive Browsing becomes difficult Degraded query performance because of additional joins ...
for Sublinear Time Maximum Inner Product Search (MIPS)
... which is an instance of the standard MIPS problem. It should be noted that we do not have control over the norm of the learned vector, i.e., ∥vj ∥2 , which often has a wide range in practice [13]. If there are N items to recommend, solving (3) requires computing N inner products. Recommendation syst ...
... which is an instance of the standard MIPS problem. It should be noted that we do not have control over the norm of the learned vector, i.e., ∥vj ∥2 , which often has a wide range in practice [13]. If there are N items to recommend, solving (3) requires computing N inner products. Recommendation syst ...
int
... • Question ”Is string S inside this bucket?” will be answered quickly, if we prepare buckets for all possibilities needs much memory space • However, we can assume usually that strings are not many • So, let’s use the first two letters for the bucket classification Two strings will be in the sam ...
... • Question ”Is string S inside this bucket?” will be answered quickly, if we prepare buckets for all possibilities needs much memory space • However, we can assume usually that strings are not many • So, let’s use the first two letters for the bucket classification Two strings will be in the sam ...
Time and location: Materials covered concepts (so far) in a nutshell COS 226
... requirements for a given set of operations – Example, create a data structure that meets the following performance requirements • findMedian in ~1 , insert ~ lg n, delete ~ lg n – Example: A leaky queue that can remove from any point, that can insert to end and delete from front, all in logarithmic ...
... requirements for a given set of operations – Example, create a data structure that meets the following performance requirements • findMedian in ~1 , insert ~ lg n, delete ~ lg n – Example: A leaky queue that can remove from any point, that can insert to end and delete from front, all in logarithmic ...
58093 String Processing Algorithms
... • Preprocess a long text for fast string matching and all kinds of other tasks ...
... • Preprocess a long text for fast string matching and all kinds of other tasks ...
Lecture 20: Priority Queues
... • It is replaced by the value stored in the last leaf node. This has echoes of the erase function in binary search trees. NOTE: We have not yet discussed how to find the last leaf. • The last leaf node is removed. • The (following) percolate_down function is then run to restore the heap property. Th ...
... • It is replaced by the value stored in the last leaf node. This has echoes of the erase function in binary search trees. NOTE: We have not yet discussed how to find the last leaf. • The last leaf node is removed. • The (following) percolate_down function is then run to restore the heap property. Th ...
Hashcube: Efficiently-queryable skycube compression
... compute skylines in arbitrary subspaces as the full dimensionality, a cost amplified when users pose a series of queries in different subspaces (such as in exploratory scenarios [2]). Skycube To offer the best possible response time for a subspace skyline query, one solution is to precompute the ans ...
... compute skylines in arbitrary subspaces as the full dimensionality, a cost amplified when users pose a series of queries in different subspaces (such as in exploratory scenarios [2]). Skycube To offer the best possible response time for a subspace skyline query, one solution is to precompute the ans ...
6.18_Exam2Review - Help-A-Bull
... Hash Functions Observe the problem with same value returned by h(x) for different values of x ...
... Hash Functions Observe the problem with same value returned by h(x) for different values of x ...
Assignment I,II and III - MLR Institute of Technology
... b. Insert a new node at the end. c. Delete a node from the beginning. d. Insert a node at the middle. Write a C program to evaluate the following postfix expression? ...
... b. Insert a new node at the end. c. Delete a node from the beginning. d. Insert a node at the middle. Write a C program to evaluate the following postfix expression? ...
Multiple choice questions Answer on Scantron Form
... A. line 0 is in error, because int * cannot be used as a return type. B. line 1 is an error, because int[n] is illegal. C. In line 2, it is illegal to modify the parameter n, because it was not passed by reference. D. line 3 will have an array bounds error at one point in the loop E. line 4 is an er ...
... A. line 0 is in error, because int * cannot be used as a return type. B. line 1 is an error, because int[n] is illegal. C. In line 2, it is illegal to modify the parameter n, because it was not passed by reference. D. line 3 will have an array bounds error at one point in the loop E. line 4 is an er ...
Balloon: A Forward-Secure Append-Only Persistent Authenticated
... providing proofs of time, when only some versions of the Balloon have been timestamped. Since Balloon is append-only, we can greatly improve the efficiency in comparison with other authenticated data structures that provide the same properties as described above, such as persistent authenticated di ...
... providing proofs of time, when only some versions of the Balloon have been timestamped. Since Balloon is append-only, we can greatly improve the efficiency in comparison with other authenticated data structures that provide the same properties as described above, such as persistent authenticated di ...
SQL un MDX (Multiple Dimensional eXpression language) valodu
... engine selects all of the records that meet the conditions in the SQL statement. Omits records that contain duplicate data in the selected fields. To be included in DISTINCT the results of the query, the values for each field listed in the SELECT statement must be unique If the SELECT clause contain ...
... engine selects all of the records that meet the conditions in the SQL statement. Omits records that contain duplicate data in the selected fields. To be included in DISTINCT the results of the query, the values for each field listed in the SELECT statement must be unique If the SELECT clause contain ...
Description - Datu bāzes tehnoloģijas
... engine selects all of the records that meet the conditions in the SQL statement. Omits records that contain duplicate data in the selected fields. To be included in DISTINCT the results of the query, the values for each field listed in the SELECT statement must be unique If the SELECT clause contain ...
... engine selects all of the records that meet the conditions in the SQL statement. Omits records that contain duplicate data in the selected fields. To be included in DISTINCT the results of the query, the values for each field listed in the SELECT statement must be unique If the SELECT clause contain ...
Slides - SRU Computer Science
... two keys hash to same position… – e.g., Hash(‘Monica’) = 4 – and, Hash(‘Scott’) = 4 ...
... two keys hash to same position… – e.g., Hash(‘Monica’) = 4 – and, Hash(‘Scott’) = 4 ...
SQL Summary
... 2) referential integrity is the rule that states that if Table A contains a foreign key that matches the primary key of Table B, then values of this foreign key must match the value of the primary key for some row or be null. ...
... 2) referential integrity is the rule that states that if Table A contains a foreign key that matches the primary key of Table B, then values of this foreign key must match the value of the primary key for some row or be null. ...
Indexing and Hashing.key
... Extended Hashing Queries and Updates • Queries are straightforward — for search-key value ...
... Extended Hashing Queries and Updates • Queries are straightforward — for search-key value ...
Rainbow table
A rainbow table is a precomputed table for reversing cryptographic hash functions, usually for cracking password hashes. Tables are usually used in recovering a plaintext password up to a certain length consisting of a limited set of characters. It is a practical example of a space/time trade-off, using less computer processing time and more storage than a brute-force attack which calculates a hash on every attempt, but more processing time and less storage than a simple lookup table with one entry per hash. Use of a key derivation function that employs a salt makes this attack infeasible.Rainbow tables are an application of an earlier, simpler algorithm by Martin Hellman.