k - Current students
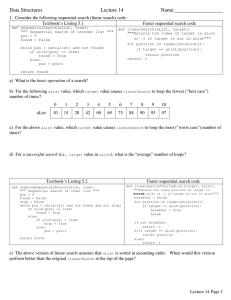
... is the number of elements currently in the heap. During the second phase, each of n removeMin operations require O (log k ) time. As k n at all times, the worst case run-time for each phase is equal to O (log n) . This gives a total run time of a PQ sort algorithm as O( n log n) if a heap is used ...
... is the number of elements currently in the heap. During the second phase, each of n removeMin operations require O (log k ) time. As k n at all times, the worst case run-time for each phase is equal to O (log n) . This gives a total run time of a PQ sort algorithm as O( n log n) if a heap is used ...
Data Structures Efficiency
... Implement a class BiDictionary that
allows adding triples {key1, key2, value} and fast
search by key1, key2 or by both key1 and key2.
Note: multiple values can be stored for given key.
...
... Implement a class BiDictionary
Sets, Maps and Hash tables
... Hash Tables • The implementations HashSet and HashMap are based on a Hash Table • A Hash Table is based on the below ideas: – Create an array of length N, which can store objects of some type T – Find a mapping from T to the interval [0; N-1] (a Hash Function f) – Store an object t of type T in the ...
... Hash Tables • The implementations HashSet and HashMap are based on a Hash Table • A Hash Table is based on the below ideas: – Create an array of length N, which can store objects of some type T – Find a mapping from T to the interval [0; N-1] (a Hash Function f) – Store an object t of type T in the ...
Securing the Network - Austin Community College
... You cannot reverse a one-way hash back to its original text. Most systems do not decrypt the stored password during authentication; they store the one-way hash. During the login process, you supply an account and password, and the password encryption algorithm generates a one-way hash. The algorithm ...
... You cannot reverse a one-way hash back to its original text. Most systems do not decrypt the stored password during authentication; they store the one-way hash. During the login process, you supply an account and password, and the password encryption algorithm generates a one-way hash. The algorithm ...
printer-friendly
... List bucket = buckets[i]; if (bucket == null) { // this is the first element in this bucket; create the bucket list first bucket = new ArrayList( ); buckets[i] = bucket; } else { // return false if elem is already contained in the set if (bucket.contains(elem)) { return false; } } // otherwise add e ...
... List bucket = buckets[i]; if (bucket == null) { // this is the first element in this bucket; create the bucket list first bucket = new ArrayList( ); buckets[i] = bucket; } else { // return false if elem is already contained in the set if (bucket.contains(elem)) { return false; } } // otherwise add e ...
hash function
... also, they specify an ordering on the values traversed by an iterator for set, values accessed in increasing order (based on operator< for TYPE) for map, values accessed in increasing order (based on operator< for KEY_TYPE) ...
... also, they specify an ordering on the values traversed by an iterator for set, values accessed in increasing order (based on operator< for TYPE) for map, values accessed in increasing order (based on operator< for KEY_TYPE) ...
Database Security - Department of Computer Science
... Query becomes: SELECT * FROM users_table WHERE username = ‘anyname‘ AND password = ‘Aa‘ OR ‘ ‘ = ‘ ‘; Note: WHERE clause => F and F or T => F or T => T AND has higher precedence than OR ...
... Query becomes: SELECT * FROM users_table WHERE username = ‘anyname‘ AND password = ‘Aa‘ OR ‘ ‘ = ‘ ‘; Note: WHERE clause => F and F or T => F or T => T AND has higher precedence than OR ...
Midterm Solutions
... Some variants of mergesort (bottom-up mergesort and natural mergesort) avoid recursion and only require O(1) extra space. ...
... Some variants of mergesort (bottom-up mergesort and natural mergesort) avoid recursion and only require O(1) extra space. ...
Slides
... – if too few intrusions detected -> false security – if too many false alarms -> ignore / waste time ...
... – if too few intrusions detected -> false security – if too many false alarms -> ignore / waste time ...
Lab Final Study Guide
... Create and save basic Functions, Stored Procedures and Triggers. o Also, you must be able to write/use an EXEC command or a SELECT command to use the function, stored procedure or trigger. Backup your database and transaction log files. (RESTORE will not be required.) Create and save an index on a f ...
... Create and save basic Functions, Stored Procedures and Triggers. o Also, you must be able to write/use an EXEC command or a SELECT command to use the function, stored procedure or trigger. Backup your database and transaction log files. (RESTORE will not be required.) Create and save an index on a f ...
The Mathematics Behind the Birthday Attack
... to note that the probability drops very quickly if we have less than 23 people, but on the other hand, the probability also reaches 1 very quickly if we have more than 23. In fact, the probability is nearly 1 with around 70 people.An important conclusion that we can draw from this is that if our has ...
... to note that the probability drops very quickly if we have less than 23 people, but on the other hand, the probability also reaches 1 very quickly if we have more than 23. In fact, the probability is nearly 1 with around 70 people.An important conclusion that we can draw from this is that if our has ...
Hash Tables The Search Problem
... If a collision occurs in the insertion operation in the cuckoo hashing scheme, then we evict the previous item in that cell and insert the new one in its place. This forces the evicted item to go to its alternate location in the other table and be inserted there, which may repeat the eviction proces ...
... If a collision occurs in the insertion operation in the cuckoo hashing scheme, then we evict the previous item in that cell and insert the new one in its place. This forces the evicted item to go to its alternate location in the other table and be inserted there, which may repeat the eviction proces ...
Max-Profit Scheduling
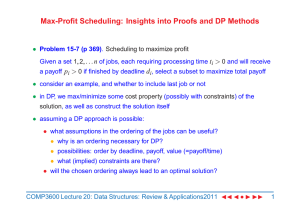
... • idea: assume jobs are ordered in increasing deadline, i.e. 1 ≤ d1 ≤ d2 ≤ . . . ≤ dn, then the max-profit scheduling problem can be expressed as: find a sub-sequence (i1, i2 , . . . im), where 1 ≤ i1 < i2 < . . . < im ≤ n s.t. the payoff Σm j=1 pi j is maximized with the constraint that Σkj=1t j ≤ ...
... • idea: assume jobs are ordered in increasing deadline, i.e. 1 ≤ d1 ≤ d2 ≤ . . . ≤ dn, then the max-profit scheduling problem can be expressed as: find a sub-sequence (i1, i2 , . . . im), where 1 ≤ i1 < i2 < . . . < im ≤ n s.t. the payoff Σm j=1 pi j is maximized with the constraint that Σkj=1t j ≤ ...
Cryptographic hashing - comp
... Hashing just over B random elements of M yields a collision probability of 0.5. Different values of p will give different constant factors, but q is still proportional to B. For a n-bit hash function, a birthday attack (or square root attack) needs 2n/2 random hashes. Answer for the birthday probl ...
... Hashing just over B random elements of M yields a collision probability of 0.5. Different values of p will give different constant factors, but q is still proportional to B. For a n-bit hash function, a birthday attack (or square root attack) needs 2n/2 random hashes. Answer for the birthday probl ...
Current Issues in Maintaining a Secure System
... How Do We Know It Works? • Basically because very smart people say it does. In general Hash Functions should have the following qualities: – The block cipher is secure. – The resulting hash size is big enough. 64-bit is too small, 128-bit might be enough. – The last block is properly length padded ...
... How Do We Know It Works? • Basically because very smart people say it does. In general Hash Functions should have the following qualities: – The block cipher is secure. – The resulting hash size is big enough. 64-bit is too small, 128-bit might be enough. – The last block is properly length padded ...
Data Structures 1
... “Every program depends on algorithms and data structures, but few programs depend on the invention of brand new ones.” ...
... “Every program depends on algorithms and data structures, but few programs depend on the invention of brand new ones.” ...
CS 130 A: Data Structures and Algorithms
... Consider any x in S. For any other y, the prob. that h(y) = h(x) is at most 1/M (by universal hashing) By linearity of expectation, the number of keys mapping to h(x) is at most (n-1)/M. Corollary. By using a random hash function (from a universal family), we get expected search time O(1 + n/M). ...
... Consider any x in S. For any other y, the prob. that h(y) = h(x) is at most 1/M (by universal hashing) By linearity of expectation, the number of keys mapping to h(x) is at most (n-1)/M. Corollary. By using a random hash function (from a universal family), we get expected search time O(1 + n/M). ...
A Comparison of Dictionary Implementations
... Hash tables were first suggested by H. P. Luhn, in an internal IBM memo in 1953 [?]. Hash tables use a hash function h : K → V to compute the location of a given value v in a table. The function is called a ’hash function’ because it ’mixes’ the data of its input, so that the output for similar inpu ...
... Hash tables were first suggested by H. P. Luhn, in an internal IBM memo in 1953 [?]. Hash tables use a hash function h : K → V to compute the location of a given value v in a table. The function is called a ’hash function’ because it ’mixes’ the data of its input, so that the output for similar inpu ...
**** 1 - Postech
... while B.hasNext() do p B.next() if p.element().getKey() = k then t p.element().getValue() S.set(p,(k,v)) return t // Return the old value S.addLast((k,v)) nn+1 // increment variable storing number of entries return null // There was no entry with key equal to k ...
... while B.hasNext() do p B.next() if p.element().getKey() = k then t p.element().getValue() S.set(p,(k,v)) return t // Return the old value S.addLast((k,v)) nn+1 // increment variable storing number of entries return null // There was no entry with key equal to k ...
String-Matching Problem
... If we choose q ≥ m and have only a constant number of hits, then the expected run time of Rabin-Karp is O(n + m). ...
... If we choose q ≥ m and have only a constant number of hits, then the expected run time of Rabin-Karp is O(n + m). ...
Jensen3
... • Conditions required to be met by the hash function for an effective traitor tracing algorithm, as specified by Chor et al., are not mentioned. – Traitor tracing algorithm needs to identify at least one traitor and reduce possibilities of a false positives. – For a k-resilient open user scheme the ...
... • Conditions required to be met by the hash function for an effective traitor tracing algorithm, as specified by Chor et al., are not mentioned. – Traitor tracing algorithm needs to identify at least one traitor and reduce possibilities of a false positives. – For a k-resilient open user scheme the ...
Rainbow table
A rainbow table is a precomputed table for reversing cryptographic hash functions, usually for cracking password hashes. Tables are usually used in recovering a plaintext password up to a certain length consisting of a limited set of characters. It is a practical example of a space/time trade-off, using less computer processing time and more storage than a brute-force attack which calculates a hash on every attempt, but more processing time and less storage than a simple lookup table with one entry per hash. Use of a key derivation function that employs a salt makes this attack infeasible.Rainbow tables are an application of an earlier, simpler algorithm by Martin Hellman.