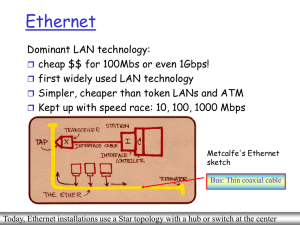
Ethernet Switches
... in shared mode, CSMA/CD is used; short distances between nodes to be efficient uses Star topology with hub, called here ''Buffered Distributor'‘ or switch at center Full-Duplex at 1 Gbps for point-to-point links Serves as a backbone for interconnecting multiple 10Mbps, 100 Mbps Ethernet LANs ...
... in shared mode, CSMA/CD is used; short distances between nodes to be efficient uses Star topology with hub, called here ''Buffered Distributor'‘ or switch at center Full-Duplex at 1 Gbps for point-to-point links Serves as a backbone for interconnecting multiple 10Mbps, 100 Mbps Ethernet LANs ...
J. Sanz-Robinson, W. Rieutort-Louis, N. Verma, S. Wagner, J.C. Sturm, "Frequency dependence of amorphous silicon Schottky diodes for Large-Area rectification applications", Device Research Conference (DRC), 10.1109/DRC.2012.6257001 pp. 135-136 University Park, PA JUN (2012).
... Imm diode drops to 3.2 % at 20 kHz. However, in a full-wave rectifier circuit, undesired capacitive currents in opposite directions through connected diodes can cancel out, and allow the circuit to operate at ...
... Imm diode drops to 3.2 % at 20 kHz. However, in a full-wave rectifier circuit, undesired capacitive currents in opposite directions through connected diodes can cancel out, and allow the circuit to operate at ...
Interceptor Appliance Installation Guide 1.1.2
... A standard electronic environment where the ambient temperature does not exceed 35º C (95º F) and the relative humidity does not exceed 95% (non-condensing). ...
... A standard electronic environment where the ambient temperature does not exceed 35º C (95º F) and the relative humidity does not exceed 95% (non-condensing). ...
DS1856 Dual, Temperature-Controlled Resistors with Inter- nally Calibrated Monitors and Password Protection
... occurred. The signals also have alarm and warning flags that notify the user when the signals go above or below the user-defined value. Interrupts can also be set for each signal. ...
... occurred. The signals also have alarm and warning flags that notify the user when the signals go above or below the user-defined value. Interrupts can also be set for each signal. ...
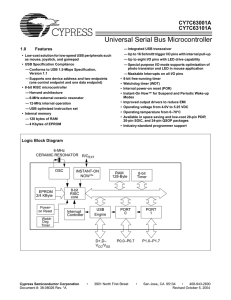
Universal Serial Bus Microcontroller
... The occurrence of a reset is recorded in the Status and Control Register located at I/O address 0xFF (Figure 6-3). Reading and writing this register are supported by the IORD and IOWR instructions. Bits 1, 2, and 7 are reserved and must be written as zeros during a write. During a read, reserved bit ...
... The occurrence of a reset is recorded in the Status and Control Register located at I/O address 0xFF (Figure 6-3). Reading and writing this register are supported by the IORD and IOWR instructions. Bits 1, 2, and 7 are reserved and must be written as zeros during a write. During a read, reserved bit ...
Mid-Term Report (March 20)
... The Transimpedance Amplifier (TIA) amplifies and transfers the current generated by the PD into a voltage. This voltage is then amplified by the post amplifier to generate the output level dictated by the IEEE specifications. The MAX3266 TIA used in this design is optimized for use in 1.25 Gbps LAN ...
... The Transimpedance Amplifier (TIA) amplifies and transfers the current generated by the PD into a voltage. This voltage is then amplified by the post amplifier to generate the output level dictated by the IEEE specifications. The MAX3266 TIA used in this design is optimized for use in 1.25 Gbps LAN ...
II. bicc overview
... APM (if “tunneling to be used” was not indicated in the IAM) specifies that the bearer control tunneling shall not be used. The CSF does not process the Bearer Control Protocol information transported by tunneling mechanism. The unmodified BCP information is tunneled through the CBC protocol toward ...
... APM (if “tunneling to be used” was not indicated in the IAM) specifies that the bearer control tunneling shall not be used. The CSF does not process the Bearer Control Protocol information transported by tunneling mechanism. The unmodified BCP information is tunneled through the CBC protocol toward ...
Spirometer Demo with Freescale Microcontrollers
... 4.2 Freescale USB stack Freescale provides a solution for medical applications developers to have a way to communicate the microcontrollers with a Host PC through a USB interface. That solution is the Freescale’s USB stack with personal healthcare device class (PHDC), which makes possible to connect ...
... 4.2 Freescale USB stack Freescale provides a solution for medical applications developers to have a way to communicate the microcontrollers with a Host PC through a USB interface. That solution is the Freescale’s USB stack with personal healthcare device class (PHDC), which makes possible to connect ...
MAX7032 Low-Cost, Crystal-Based, Programmable, ASK/FSK Transceiver with Fractional-N PLL General Description
... ASK/FSK Transceiver with Fractional-N PLL The MAX7032 crystal-based, fractional-N transceiver is designed to transmit and receive ASK/OOK or FSK data in the 300MHz to 450MHz frequency range with data rates up to 33kbps (Manchester encoded) or 66kbps (NRZ encoded). This device generates a typical out ...
... ASK/FSK Transceiver with Fractional-N PLL The MAX7032 crystal-based, fractional-N transceiver is designed to transmit and receive ASK/OOK or FSK data in the 300MHz to 450MHz frequency range with data rates up to 33kbps (Manchester encoded) or 66kbps (NRZ encoded). This device generates a typical out ...
on TCP/IP
... ◦ Data field of a large IP packet is fragmented. ◦ The fragments are sent into a series of smaller IP packets fitting a network’s MTU. ◦ Fragmentation is done by routers. ◦ Fragmentation may be done multiple times along the route. ...
... ◦ Data field of a large IP packet is fragmented. ◦ The fragments are sent into a series of smaller IP packets fitting a network’s MTU. ◦ Fragmentation is done by routers. ◦ Fragmentation may be done multiple times along the route. ...
ds_scg.pdf
... begins after the CONF_DONE goes high and completes within 136 clock cycles. After initialization, the Cyclone FPGA enters user mode. ...
... begins after the CONF_DONE goes high and completes within 136 clock cycles. After initialization, the Cyclone FPGA enters user mode. ...
What are the advantages to organizations of using computer networks
... 77) The personal dictation software is classed as _________________ recognition system a) Continuous-speech b) Speaker-independent c) Isolated-word d) Both A and B e) None of the above 78) The personal dictation software is classed as an ___________________________ recognition system a) Speaker-enro ...
... 77) The personal dictation software is classed as _________________ recognition system a) Continuous-speech b) Speaker-independent c) Isolated-word d) Both A and B e) None of the above 78) The personal dictation software is classed as an ___________________________ recognition system a) Speaker-enro ...
DN1035 - Measuring 18 2-Wire RTDs with the
... A single LTC ®2983 temperature measurement device can support up to 18 2-wire RTD probes, as shown in Figure 1. Each RTD measurement involves simultaneous sensing of two voltages developed across RSENSE and the RTD probe RTDx due to the current IS. Each voltage is sensed differentially, and given th ...
... A single LTC ®2983 temperature measurement device can support up to 18 2-wire RTD probes, as shown in Figure 1. Each RTD measurement involves simultaneous sensing of two voltages developed across RSENSE and the RTD probe RTDx due to the current IS. Each voltage is sensed differentially, and given th ...
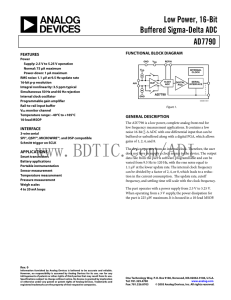
Low Power, 16-Bit Buffered Sigma-Delta ADC AD7790
... The DOUT/RDY falling edge can be used as an interrupt to a processor, indicating that valid data is available. With an external serial clock, the data can be read using the DOUT/RDY pin. With CS low, the data/control word information is placed on the DOUT/RDY pin on the SCLK falling edge and is vali ...
... The DOUT/RDY falling edge can be used as an interrupt to a processor, indicating that valid data is available. With an external serial clock, the data can be read using the DOUT/RDY pin. With CS low, the data/control word information is placed on the DOUT/RDY pin on the SCLK falling edge and is vali ...
Truth tables and Resistors ion series and parallel
... If there is not a closed path that allows the charge to get back to where it started (without retracing its steps), the circuit is said to be “open” or “broken.” The path doesn’t have to be unique; there may be more than one path. ...
... If there is not a closed path that allows the charge to get back to where it started (without retracing its steps), the circuit is said to be “open” or “broken.” The path doesn’t have to be unique; there may be more than one path. ...
GTL2008PW
... the exception of 11BO because its normal state is LOW, so it is forced LOW. EN1 and EN2 will remain LOW until VCC is at normal voltage, the other inputs are in valid states and VREF is at its proper voltage to assure that the outputs will remain high-impedance through power-up. The GTL2008 has the e ...
... the exception of 11BO because its normal state is LOW, so it is forced LOW. EN1 and EN2 will remain LOW until VCC is at normal voltage, the other inputs are in valid states and VREF is at its proper voltage to assure that the outputs will remain high-impedance through power-up. The GTL2008 has the e ...
Introduction
... Case 2 : No Physical Multicast Support Most WANs do not support physical multicast addressing . To send a multicast packet through these networks, a process called tunneling is used. In tunneling , the multicast packet is encapsulated in a unicast packet and sent through the network, where it emer ...
... Case 2 : No Physical Multicast Support Most WANs do not support physical multicast addressing . To send a multicast packet through these networks, a process called tunneling is used. In tunneling , the multicast packet is encapsulated in a unicast packet and sent through the network, where it emer ...
DS2782 Stand-Alone Fuel Gauge IC GENERAL DESCRIPTION
... estimation functions, but preserves register contents. SLEEP mode is entered under two different conditions and an enable bit for each condition makes entry into SLEEP optional. SLEEP mode can be enabled using the Power Mode (PMOD) bit or the Under Voltage Enable (UVEN) bit. The PMOD type SLEEP is e ...
... estimation functions, but preserves register contents. SLEEP mode is entered under two different conditions and an enable bit for each condition makes entry into SLEEP optional. SLEEP mode can be enabled using the Power Mode (PMOD) bit or the Under Voltage Enable (UVEN) bit. The PMOD type SLEEP is e ...
slides - network systems lab @ sfu
... Data structure of TCP endpoint Transmission control block: Stores the connection state and related variables Transmit queue: Buffers containing outstanding data Receiver queue: Buffers for received data (but not yet forwarded to higher layer) ...
... Data structure of TCP endpoint Transmission control block: Stores the connection state and related variables Transmit queue: Buffers containing outstanding data Receiver queue: Buffers for received data (but not yet forwarded to higher layer) ...