1 - Portal UniMAP
... packets. 3. How does information get passed from one layer to next in the Internet model? Each layer calls upon the services of the layer just below it using interfaces between each pair of adjacent layers. 4. What are headers and trailers, and how do they get added and removed Headers and trailers ...
... packets. 3. How does information get passed from one layer to next in the Internet model? Each layer calls upon the services of the layer just below it using interfaces between each pair of adjacent layers. 4. What are headers and trailers, and how do they get added and removed Headers and trailers ...
(M1) why are protocols important
... There are literally dozens of protocols all designed to perform specific tasks from the principle WAN essential ones such as TCP/IP, POP3, FTP to the less well know ones ...
... There are literally dozens of protocols all designed to perform specific tasks from the principle WAN essential ones such as TCP/IP, POP3, FTP to the less well know ones ...
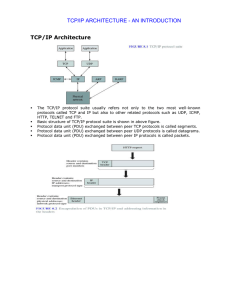
TCP/IP Architecture TCP/IP ARCHITECTURE
... Example: Ethernet uses 48-bit addresses o Each Ethernet network interface card (NIC) has globally unique Medium Access Control (MAC) or physical address o First 24 bits identify NIC manufacturer; second 24 bits are serial number o 00:90:27:96:68:07 12 hex numbers ...
... Example: Ethernet uses 48-bit addresses o Each Ethernet network interface card (NIC) has globally unique Medium Access Control (MAC) or physical address o First 24 bits identify NIC manufacturer; second 24 bits are serial number o 00:90:27:96:68:07 12 hex numbers ...
The Next Generation of IP
... The Next Generation of IP Router: This router can store and manage the state information of data flows. ...
... The Next Generation of IP Router: This router can store and manage the state information of data flows. ...
PH19510 Lecture 12
... RFC mechanism came out of ARPA Serve as mechanism for dissemination for information Some become adopted as standards ...
... RFC mechanism came out of ARPA Serve as mechanism for dissemination for information Some become adopted as standards ...
Basic Network Concepts
... layer in packets called datagrams. • Each IP datagram contains a header between 20 and 60 bytes long and a payload that contains up to 65,515 bytes of data. ...
... layer in packets called datagrams. • Each IP datagram contains a header between 20 and 60 bytes long and a payload that contains up to 65,515 bytes of data. ...
ITEC 370 Midterm
... a. LAN c. peer-to-peer b. internetwork d. client/server 2. In most situations, wireless LANs use a central device, called a(n) ____, to control communications. a. hub c. concentrator b. switch d. access point 3. A ____ network topology is the most fault tolerant one. a. ring c. bus b. mesh d. star 4 ...
... a. LAN c. peer-to-peer b. internetwork d. client/server 2. In most situations, wireless LANs use a central device, called a(n) ____, to control communications. a. hub c. concentrator b. switch d. access point 3. A ____ network topology is the most fault tolerant one. a. ring c. bus b. mesh d. star 4 ...
2007_1127PNAMP Data Mgmt Tasks crude summary
... DRAFT PNAMP Data Mgmt Tasks – summary for discussion TASKS lead PNAMP Data Management Workgroup (?) interact with each PNAMP technical WG to understand their goals and to communicate to them DM processes, tools available, etc understand data management activities that need to be brought to PNA ...
... DRAFT PNAMP Data Mgmt Tasks – summary for discussion TASKS lead PNAMP Data Management Workgroup (?) interact with each PNAMP technical WG to understand their goals and to communicate to them DM processes, tools available, etc understand data management activities that need to be brought to PNA ...
1-Introduction :
... • Header - Contains control information, such addressing, and is located at the beginning of the PDU • Trailer - Contains control information added to the end of the PDU Framing breaks the stream into decipherable groupings, with control information inserted in the header and trailer as values in di ...
... • Header - Contains control information, such addressing, and is located at the beginning of the PDU • Trailer - Contains control information added to the end of the PDU Framing breaks the stream into decipherable groupings, with control information inserted in the header and trailer as values in di ...
Chapter 16
... Software implementing layer N at the destination receives exactly the message sent by software implementing layer N at the source ...
... Software implementing layer N at the destination receives exactly the message sent by software implementing layer N at the source ...
Networking and communication
... transport layer The OS adds a TCP header that identify the source and destination ports, forming a TCP segment, and sends that to the network layer In the network layer, an IP header identifying the source and destination systems are added, which gets sent to the link layer The link layer appe ...
... transport layer The OS adds a TCP header that identify the source and destination ports, forming a TCP segment, and sends that to the network layer In the network layer, an IP header identifying the source and destination systems are added, which gets sent to the link layer The link layer appe ...
cut-through
... What will a bridge do if it receives a frame with a MAC address that is not within the table? • send frame to all ports except source port ...
... What will a bridge do if it receives a frame with a MAC address that is not within the table? • send frame to all ports except source port ...
Week 1 - cda college
... The idea behind the model: Break up the design to make implementation simpler. Each layer has a well-defined function. Layers pass to one another only the information that is relevant at each level. Communication happens only between adjacent layers. ...
... The idea behind the model: Break up the design to make implementation simpler. Each layer has a well-defined function. Layers pass to one another only the information that is relevant at each level. Communication happens only between adjacent layers. ...
Introduction to Distributed Systems & Networking
... • A message is generated at the highest level, and is passed down the levels, encapsulated by lower levels, until it is sent over the wire. • On the destination, it makes its way up the layers,until the high-level msg reaches its high-level destination. ...
... • A message is generated at the highest level, and is passed down the levels, encapsulated by lower levels, until it is sent over the wire. • On the destination, it makes its way up the layers,until the high-level msg reaches its high-level destination. ...
Fundamentals of Computer Networks ECE 478/578
... Layers of the OSI model Physical Layer: Transmission/reception of raw bits Data Link Layer: Maps bits into frames, dictates sharing of common medium, corrects/detects errors , re-orders frames Network Layer: Routes packets to destination, may perform fragmentation and re-assembly. Transport Layer: ...
... Layers of the OSI model Physical Layer: Transmission/reception of raw bits Data Link Layer: Maps bits into frames, dictates sharing of common medium, corrects/detects errors , re-orders frames Network Layer: Routes packets to destination, may perform fragmentation and re-assembly. Transport Layer: ...
OSI 7-Layer Model
... standards for communication in the network across different equipment and applications by different vendors. It is now considered the primary architectural model for intercomputing and internetworking communications. Most of the network communication protocols used today have a structure based on th ...
... standards for communication in the network across different equipment and applications by different vendors. It is now considered the primary architectural model for intercomputing and internetworking communications. Most of the network communication protocols used today have a structure based on th ...
Lecture # 2 CH. 2 Network Models
... 22. Suppose a computer sends a frame to another computer on a bus topology LAN. The physical destination address of the frame is corrupted during the transmission. What happens to the frame? How can the sender be informed about the situation? If the corrupted destination address does not match any s ...
... 22. Suppose a computer sends a frame to another computer on a bus topology LAN. The physical destination address of the frame is corrupted during the transmission. What happens to the frame? How can the sender be informed about the situation? If the corrupted destination address does not match any s ...
Energy Efficient Implementation of IETF Protocols on Constrained
... are customers of the lower layers (PHY, MAC, and Dutycycling). In order to get a better service, the designers of higher layers should know them better. The IETF has developed multiple protocols for constrained networked devices. A lot of implicitly included design principles have been used in the ...
... are customers of the lower layers (PHY, MAC, and Dutycycling). In order to get a better service, the designers of higher layers should know them better. The IETF has developed multiple protocols for constrained networked devices. A lot of implicitly included design principles have been used in the ...
The Data Link Layer
... Only one frame at a time can be in transit. 1. Source transmits frame 2. Destination receives frame and replies with acknowledgement (if it is correct, otherwise send ...
... Only one frame at a time can be in transit. 1. Source transmits frame 2. Destination receives frame and replies with acknowledgement (if it is correct, otherwise send ...