INTRODUCTION - mien phi
... Presentation: formats data for presentation to the user, provides data interfaces, data compression and translation between different data formats Session: responsible for initiating, maintaining and terminating each logical session between sender and ...
... Presentation: formats data for presentation to the user, provides data interfaces, data compression and translation between different data formats Session: responsible for initiating, maintaining and terminating each logical session between sender and ...
CCNA cheat sheet - Internetwork Training
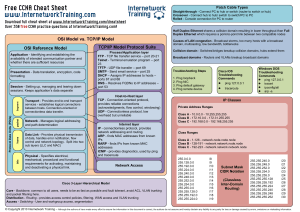
... OSI Model vs. TCP/IP Model OSI Reference Model Application - Identifying and establishing the availability of intended communication partner and whether there are sufficient resources Presentation - Data translation, encryption, code formatting ...
... OSI Model vs. TCP/IP Model OSI Reference Model Application - Identifying and establishing the availability of intended communication partner and whether there are sufficient resources Presentation - Data translation, encryption, code formatting ...
Chapter 20 Transport Protocols
... —Three way handshake —Between pairs of ports —One port can connect to multiple destinations ...
... —Three way handshake —Between pairs of ports —One port can connect to multiple destinations ...
Communication software and protocols
... Session layer • sets up and maintains the communication linkages between two computers during data transmission • It establishes, manages and terminates the connections between the local and remote application. ...
... Session layer • sets up and maintains the communication linkages between two computers during data transmission • It establishes, manages and terminates the connections between the local and remote application. ...
Computer Communication Networks HW8 2009/01/08 39. A network
... Ans: The mask is 20 bits long, so the network part is 20 bits. The remaining 12 bits are for the host, so 4096 host addresses exist. 45. Many companies have a policy of having two (or more) routers connecting the company to the Internet to provide some redundancy in case one of them goes down. Is th ...
... Ans: The mask is 20 bits long, so the network part is 20 bits. The remaining 12 bits are for the host, so 4096 host addresses exist. 45. Many companies have a policy of having two (or more) routers connecting the company to the Internet to provide some redundancy in case one of them goes down. Is th ...
1-ITN-chap-3g
... Application Protocol - Hypertext Transfer Protocol (HTTP) is a protocol that governs the way a web server and a web client interact. Transport Protocol - Transmission Control Protocol (TCP) is the transport protocol that manages the individual conversations between web servers and web clients. ...
... Application Protocol - Hypertext Transfer Protocol (HTTP) is a protocol that governs the way a web server and a web client interact. Transport Protocol - Transmission Control Protocol (TCP) is the transport protocol that manages the individual conversations between web servers and web clients. ...
Slide 1
... • IP address and Port Number: IP address is a 32-bit quantity that uniquely identifies the host. Port number identifies the type of ...
... • IP address and Port Number: IP address is a 32-bit quantity that uniquely identifies the host. Port number identifies the type of ...
Tcp/ip
... passes down through the layers of the protocol and then back up through the layers on the server side, as shown on the previous slide • This means that the last action that takes place in the Link layer on the client computer becomes the first action in the Link layer in the server – this is an exam ...
... passes down through the layers of the protocol and then back up through the layers on the server side, as shown on the previous slide • This means that the last action that takes place in the Link layer on the client computer becomes the first action in the Link layer in the server – this is an exam ...
Data Communication and Networks
... 6. KavethPahlavan, K.Prasanth Krishnamurthy, ‘Principles of Wireless Networks”, Pearson Education Asia, 2002. 7. Jon W. Mark, Weihua Zhuang, ‘Wireless communication and Networking’, Prentice Hall India, ...
... 6. KavethPahlavan, K.Prasanth Krishnamurthy, ‘Principles of Wireless Networks”, Pearson Education Asia, 2002. 7. Jon W. Mark, Weihua Zhuang, ‘Wireless communication and Networking’, Prentice Hall India, ...
Document
... To understand the flow of information on the Internet To understand the levels of activity in network traffic flow To understand the basis for vulnerabilities To understand the basis for security tools and how they work ...
... To understand the flow of information on the Internet To understand the levels of activity in network traffic flow To understand the basis for vulnerabilities To understand the basis for security tools and how they work ...
ASSIGNMENT #3
... A Bridge is a combination of hardware and software. It has its own operating system. It helps to conserve the bandwidth of a network. Bandwidth is the speed of a network. It indicates how many bits can be transmitted across a network in a given time. In case of a bridge, the larger network is physic ...
... A Bridge is a combination of hardware and software. It has its own operating system. It helps to conserve the bandwidth of a network. Bandwidth is the speed of a network. It indicates how many bits can be transmitted across a network in a given time. In case of a bridge, the larger network is physic ...
Business Data Communications and Networking
... Service Point Address (more often called a port) used to track multiple sessions between the same systems. SPA’s are used to allow a node to offer more than one service (i.e. it could offer both mail and web services) This layer is why you have to specify TCP or UDP when dealing with TCP/IP ...
... Service Point Address (more often called a port) used to track multiple sessions between the same systems. SPA’s are used to allow a node to offer more than one service (i.e. it could offer both mail and web services) This layer is why you have to specify TCP or UDP when dealing with TCP/IP ...
Introduction - Department of Information Technologies
... Office Hour: Open Door Policy Class Schedule:Wednesday 17:00-19:45 ...
... Office Hour: Open Door Policy Class Schedule:Wednesday 17:00-19:45 ...
Effective CAN Controller Design for Highly Secured Applications
... means that messages remain intact after ...
... means that messages remain intact after ...
ppt
... Hubs • Operate as a repeater – Broadcast an incoming frame to all ports, except for the ingress port – Like having a longer Ethernet cable that all the hosts tap into – All ports are on single collision domain! ...
... Hubs • Operate as a repeater – Broadcast an incoming frame to all ports, except for the ingress port – Like having a longer Ethernet cable that all the hosts tap into – All ports are on single collision domain! ...
LAN - Redbrick
... Protocol Hierarchies • Higher layer entities build packets and provide these as a bit\byte stream to lower layer entities. • Wrapping like Russian Dolls. Data Link Layer ...
... Protocol Hierarchies • Higher layer entities build packets and provide these as a bit\byte stream to lower layer entities. • Wrapping like Russian Dolls. Data Link Layer ...
Week One
... • A layer model • Each layer performs a subset of the required communication functions • Each layer relies on the next lower layer to perform more primitive functions • Each layer provides services to the next higher layer • Changes in one layer should not require changes in other layers ...
... • A layer model • Each layer performs a subset of the required communication functions • Each layer relies on the next lower layer to perform more primitive functions • Each layer provides services to the next higher layer • Changes in one layer should not require changes in other layers ...
Chapter 1: Protocols and Layers
... and connectionless but the transport layer often adds a measure of reliability (such as resending missing or errored packet content) and connections to the network layer. The network layer has the network address, while the transport layer focuses on ports and multiplexing application’s traffic on t ...
... and connectionless but the transport layer often adds a measure of reliability (such as resending missing or errored packet content) and connections to the network layer. The network layer has the network address, while the transport layer focuses on ports and multiplexing application’s traffic on t ...