Network hunt - Barefoot Computing
... software, such as Scratch or Kodu, or word processing software. Most of the time we have to log in to the network on these computers before we can use them. ...
... software, such as Scratch or Kodu, or word processing software. Most of the time we have to log in to the network on these computers before we can use them. ...
Troubleshooting your PC - Hill City SD 51-2
... Allow sharing of data, peripherals, software, and storage ...
... Allow sharing of data, peripherals, software, and storage ...
Review of Underlying Network Technologies
... Want user to see only one network to which all machines are connected Network level interconnections means: ...
... Want user to see only one network to which all machines are connected Network level interconnections means: ...
Introduction to Computers
... Network Communication • Protocol – common language that allows devices to talk to each other – Internet protocol (IP), file transfer protocol (FTP), hypertext transfer protocol (FTP) ...
... Network Communication • Protocol – common language that allows devices to talk to each other – Internet protocol (IP), file transfer protocol (FTP), hypertext transfer protocol (FTP) ...
Review Questions
... 12. A honeypot is used for each of the following except ____________. A. Deflect attention away from real servers B. Filter packets before they reach the network C. Provide early warning of new attacks D. Examine attacker techniques 13. A(n) _____ watches for attacks but only takes limited action wh ...
... 12. A honeypot is used for each of the following except ____________. A. Deflect attention away from real servers B. Filter packets before they reach the network C. Provide early warning of new attacks D. Examine attacker techniques 13. A(n) _____ watches for attacks but only takes limited action wh ...
Certification Exercise 2
... 8. Which network device provides public to private network security and may use Network Address Translation (NAT)? a) Hub b) Bridge c) Switch d) Firewall 9. Which device connects multiple computers to create a single logical network segment? a) Hub b) NIC c) Router d) Bridge 10. Devices on a Token ...
... 8. Which network device provides public to private network security and may use Network Address Translation (NAT)? a) Hub b) Bridge c) Switch d) Firewall 9. Which device connects multiple computers to create a single logical network segment? a) Hub b) NIC c) Router d) Bridge 10. Devices on a Token ...
A Big Test Result - Knowledge Systems Institute
... interface cards (NICs) and how they are installed. ...
... interface cards (NICs) and how they are installed. ...
Class_3_-_Subarea_V
... • Sever – A computer or computer program which serves the needs of another program. File servers enable other programs to locate and extract files from databases • Port – A physical or virtual interface or connection between two pieces of hardware. USB is one of the most recognizable port protocols ...
... • Sever – A computer or computer program which serves the needs of another program. File servers enable other programs to locate and extract files from databases • Port – A physical or virtual interface or connection between two pieces of hardware. USB is one of the most recognizable port protocols ...
New Bulgarian University
... which the packet is to be sent on the way to its final destination Depending on the application and implementation, it can also contain additional values that refine path selection: ...
... which the packet is to be sent on the way to its final destination Depending on the application and implementation, it can also contain additional values that refine path selection: ...
Network Interface Card Specifications
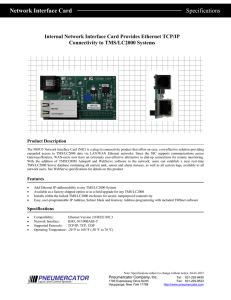
... expanded access to TMS/LC2000 data via LAN/WAN Ethernet networks. Since the NIC supports communications across Gateways/Routers, WAN-users now have an extremely cost-effective alternative to dial-up connections for remote monitoring. With the addition of TMSCOMM Autopoll and WebServe software to the ...
... expanded access to TMS/LC2000 data via LAN/WAN Ethernet networks. Since the NIC supports communications across Gateways/Routers, WAN-users now have an extremely cost-effective alternative to dial-up connections for remote monitoring. With the addition of TMSCOMM Autopoll and WebServe software to the ...
Computer Networks - Texas State Department of Computer Science
... usually while still allowing traffic between the ...
... usually while still allowing traffic between the ...
Chapter 6
... sufficient resources at each router on its path before transmitting data A session must: declare its QoS requirement using R-spec characterize traffic it will send into network using T-spec A signaling protocol is needed to carry R-spec and T-spec to routers Router must determine whether or not ...
... sufficient resources at each router on its path before transmitting data A session must: declare its QoS requirement using R-spec characterize traffic it will send into network using T-spec A signaling protocol is needed to carry R-spec and T-spec to routers Router must determine whether or not ...
Review Questions on Documentary – The Internet Behind the Web
... Who built the first experimental connection between two computers and where did he built it? What is(are) the function(s) of interface message processors (IMP)? Which firm built the first IMP? For the APRANET project, four universities are initially involved in setting up the experimental network. W ...
... Who built the first experimental connection between two computers and where did he built it? What is(are) the function(s) of interface message processors (IMP)? Which firm built the first IMP? For the APRANET project, four universities are initially involved in setting up the experimental network. W ...
Foundations of Networking Networking CS 3470, Section 1 Sarah Diesburg
... Nodes on the inside of the cloud implement the network [switches] Nodes on the outside of the cloud use the ...
... Nodes on the inside of the cloud implement the network [switches] Nodes on the outside of the cloud use the ...
Peer-to-Peer Networks 13 Internet – The Underlay Network
... - IP packet (datagram) contains start IP address and destination IP address • if destination = my address then hand over to higher layer • if destination in routing table then forward packet to corresponding gateway • if destination IP subnet in routing table then forward packet to corresponding gat ...
... - IP packet (datagram) contains start IP address and destination IP address • if destination = my address then hand over to higher layer • if destination in routing table then forward packet to corresponding gateway • if destination IP subnet in routing table then forward packet to corresponding gat ...
Optical Burst Switching.pdf
... Internet. A router is connected to two or more data lines from different networks. When data comes in on one of the lines, the router reads the address information in the packet to determine its ultimate destination. Then, using information in its routing table, it directs the packet to the next net ...
... Internet. A router is connected to two or more data lines from different networks. When data comes in on one of the lines, the router reads the address information in the packet to determine its ultimate destination. Then, using information in its routing table, it directs the packet to the next net ...
Welcome to CS 444/544!
... • The Internet’s primary network-level services (used by network programmers): – Connectionless packet delivery • Break messages up into small chunks (called packets) • Route each packet separately through the network • Reassemble message when all packets reach destination ...
... • The Internet’s primary network-level services (used by network programmers): – Connectionless packet delivery • Break messages up into small chunks (called packets) • Route each packet separately through the network • Reassemble message when all packets reach destination ...
cut-through
... Mary investigates the problem and notices that her co-worker John has been hosting an online video conference. What is the network ...
... Mary investigates the problem and notices that her co-worker John has been hosting an online video conference. What is the network ...
Internetworking - University of Maine System
... Universal Service is the concept that any device on any network can communicate with any arbitrary device on another network. The Internet is a heterogeneous environment, with multiple, independent network topologies. In LANs, we have seen that heterogeneous technologies cannot interconnect without ...
... Universal Service is the concept that any device on any network can communicate with any arbitrary device on another network. The Internet is a heterogeneous environment, with multiple, independent network topologies. In LANs, we have seen that heterogeneous technologies cannot interconnect without ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.















![Computer Networks [Opens in New Window]](http://s1.studyres.com/store/data/001432217_1-c782ef807e718d5ed80f4e9484b1006a-300x300.png)