* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Slide 1
Dynamic Host Configuration Protocol wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Wireless security wikipedia , lookup
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
Distributed firewall wikipedia , lookup
Computer network wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Deep packet inspection wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Internet protocol suite wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
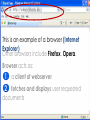
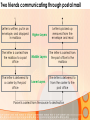
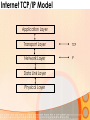
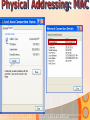
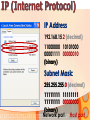
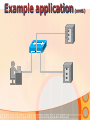
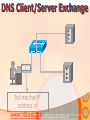
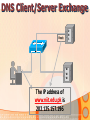
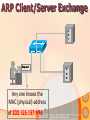
Information and Communication Technology Fundamentals Credits Hours: 2+1 Instructor: Ayesha Bint Saleem HIGHLIGHTS OF LAST LECTURE 3 aspects of a network • Software • Hardware • Medium Software • Application • Protocols • Packet • Payload (Data part) • Header (Control information part) Hardware • Modem • ISDN • DSL • LAN Card • Wireless LAN Card • ATM • Wimax Medium • Wired • Twisted pair cable • Co-axial cable • Fiber optic cable • Wireless Network Topologies • Point 2 Point • Bus • Ring • Mesh • Star Network Linking Devices • Hub • Bridge • Switch • Router • Gateway Classification of Networks according to geographical scope • Wide Area Networks • Metropolitan Area Networks • Campus Area Networks • Local Area Networks • Home Area Networks • Personal Area Networks NETWORKS - II Presentation Credits • “Data Communications and Networking”, Behrouz A. Forouzan • “Computer Networks”, Tanenbaum • Dr Junaid, EE Dept, SEECS Types of communication • According to data direction • Simplex • One-way communication (only send or only receive) • Half-Duplex • Two-way communication (send/receive) but one at a time • Full Duplex • Two-way communication (send/receive) at the same time Types of communication • According to intended recipients • Unicast • Sending data to only one recipient • Multicast • Sending data to multiple recipients • Possibly at different locations • Broadcast • Sending data to everybody • You open a browser e.g. Internet Explorer • Type address on the browser’s address bar NETWORKING SOFTWARE Address Bar Example application http://www.niit.edu.pk This is an example of a browser (Internet Explorer) Other browsers include Firefox, Opera. Browser acts as: 1 a client of webserver 2 fetches and displays user requested documents • The SEECS page is displayed in front of you after some time • A lot of things are happening from your typing the address to getting to see the SEECS home page • Inside your computer AND • On the network • Like • Locating where the SEECS server is located which is hosting the SEECS website • Establishing a connection with the SEECS server • Requesting server to send you the webpage • Receiving data from server in the form of packets • Ensuring packets arriving are free of error • Arranging packets in order to re-create the original webpage • Who is dealing-with/enabling all this? • Network software on your computer • Network software on the NIIT server • Network software on many other devices that you are not aware of • DNS Server • Router • Possibly many others • Network software follows different procedures to have the web-page displayed to you • These procedures are called protocols • Variety of protocols are running on your computer • Each responsible to perform a different task • To reduce design complexity, the functions that a network software provides are organized as a stack of levels or layers • Each layer uses the services of the layer below it • Each layer offers some services to the layer above it • The concept of layering is used in daily life Two friends communicating through postal mail Letter is written, put in an envelope, and dropped in mailbox The letter is carried from the mailbox to a post office The letter is delivered to a carrier by the post office Higher Layers Letter is picked up removed from the envelope and read Middle Layers The letter is carried from the post office to the mailbox Lower Layers The letter is delivered to from the carrier to the post office Parcel is carried from the source to destination Internet Model • The layering structure that internet uses • Consists of five layers Internet TCP/IP Model Application Layer Transport Layer TCP Network Layer IP Data Link Layer Physical Layer • Physical Layer: • Responsible for transmitting raw bits over a communication medium (channel) • Data Link Layer • Source DLL gives a packet to the physical layer in the form of bits • Destination DLL receives bits of the packet from the physical layer • Node to node delivery of a packet • Error control • Use of Acknowledgements • Network Layer • End –to-end delivery of a packet • Transport Layer • Process to process delivery of a packet • May include error control • Application layer • Enable use of network • Provides Interface Addressing in the Internet • Each station must be addressable • Two kinds of addresses: • 1) Physical addressing (MAC addresses) • 2) Logical addressing (IP addresses) Addressing in the Internet • The communicating applications (source/ destination applications) must also be identifiable • Identified through TCP ports • • A socket (IP address + TCP port) identifies both an application and the machine it’s on. Physical Addressing: MAC MAC Address: 48 bits (Ethernet) Flat addressing Usually non-configurable Logical Addressing: IP IP Version 4; Address: 32 bits 4,294,967,296 possible addresses = 2 IP Version 6; Address: 128 bits 32 Hierarchical addressing 2 parts: a network part and a host part. Machines in a LAN have the same network part; they differ in host parts Logical Addressing: IP How is the network part of an IP address defined Subnet mask IP (Internet Protocol) IP Address 192.168.15.2 (decimal) 11000000 10101000 00001111 00000010 (binary) Subnet Mask: 255.255.255.0 (decimal) 11111111 11111111 11111111 00000000 (binary) Network part Host part Applications Identification How to identify source/ destination application communicating The source/ destination applications are identified through TCP ports Common TCP Ports: HTTP: 80; SMTP:25; DNS: 53 Naming Machine addresses are difficult to memorize Solution: Provide recognizable names to numerically addressed Internet resources. Examples: google.com; stanford.edu; niit.edu.pk Naming How to manage address to name 1) A hosts file onmapping? each machine Unix/ Linux: /etc/hosts file Windows: %SystemRoot%\system32\drivers\etc 2) A decentralized domain name server system Scalable solution The name to IP mapping is available at a DNS server Example application D N S W W W (contd.) DNS Client/Server Exchange D N S Reques t Tell me the IP address of www.niit.edu.pk? W W W DNS Client/Server Exchange D N S Reply W W W The IP address of www.niit.edu.pk is 202.125.157.196 ARP Client/Server Exchange D N S Request Any one knows the MAC (physical) address of 202.125.157.196 ? W W W ARP Client/Server Exchange D N S Reply W W W The MAC address of 202.125.157.196 is 12:34:aa:bb:cc:dd HTTP Client/Server Exchange D N S Request Send me the index.html page for the host www.niit.edu.pk using HTTP version 1.1 W W W