Introduction
... Topology or bandwidth changes, congestion Rapid convergence of routers to consistent set of routes ...
... Topology or bandwidth changes, congestion Rapid convergence of routers to consistent set of routes ...
01.1-Overview
... NOTES: (1) Internet Usage and World Population Statistics are for December 31, 2011. (2) CLICK on each world region name for detailed regional usage information. (3) Demographic (Population) numbers are based on data from the US Census Bureau and local census agencies. (4) Internet usage information ...
... NOTES: (1) Internet Usage and World Population Statistics are for December 31, 2011. (2) CLICK on each world region name for detailed regional usage information. (3) Demographic (Population) numbers are based on data from the US Census Bureau and local census agencies. (4) Internet usage information ...
Chapter 2 Networking Standards and the OSI Model
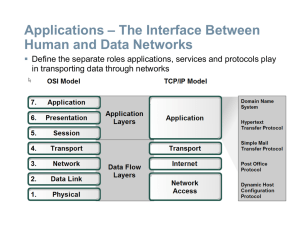
... converting the packets/datagrams into frames, the MAC sublayer converts the frames into bits, which the Physical layer can put on the wire. These steps are known as data encapsulation. When the bits stream arrives at the destination, the process is reversed and each layer will remove their correspon ...
... converting the packets/datagrams into frames, the MAC sublayer converts the frames into bits, which the Physical layer can put on the wire. These steps are known as data encapsulation. When the bits stream arrives at the destination, the process is reversed and each layer will remove their correspon ...
Mobile Health Communication Infrastructure
... How to deal with traffic management in the MobiHealth infrastructure? ...
... How to deal with traffic management in the MobiHealth infrastructure? ...
View
... means delivery not only from one computer to the next but also from a specific running program to specific running program. The transport layer header must therefore include a type of address called a service-point address (or port address). The network layer gets each packet to the correct computer ...
... means delivery not only from one computer to the next but also from a specific running program to specific running program. The transport layer header must therefore include a type of address called a service-point address (or port address). The network layer gets each packet to the correct computer ...
Chapter 2 Network Models 2.1
... Physical Layer Data Link Layer Network Layer Transport Layer Session Layer Presentation Layer Application Layer ...
... Physical Layer Data Link Layer Network Layer Transport Layer Session Layer Presentation Layer Application Layer ...
ppt
... If channel sensed idle: transmit entire frame If channel sensed busy, defer transmission ...
... If channel sensed idle: transmit entire frame If channel sensed busy, defer transmission ...
Expanded Notes: Network Monitoring Parts 1 and 2
... information to system administrators. This permits there to be separation between the software that generates the message, the storage of that message, and the software that analyzes the generated message. This separation of function allows Syslog to be highly configurable and has also allowed it to ...
... information to system administrators. This permits there to be separation between the software that generates the message, the storage of that message, and the software that analyzes the generated message. This separation of function allows Syslog to be highly configurable and has also allowed it to ...
United States Department of the Army Cisco Past Performance
... This proposal includes data that shall not be disclosed outside of FTC and shall not be duplicated, used, or disclosed, in whole or in part, for any purpose other than to evaluate this proposal. If, however, a contract is awarded to Exalt, FTC shall have the right to duplicate, use, or disclose the ...
... This proposal includes data that shall not be disclosed outside of FTC and shall not be duplicated, used, or disclosed, in whole or in part, for any purpose other than to evaluate this proposal. If, however, a contract is awarded to Exalt, FTC shall have the right to duplicate, use, or disclose the ...
A Summary of the Publications Which Use the Data from SUVnet
... for Localization in Mobile Networks – Con’d • A general framework and Three novel localization schemes were developed then for mobile networks. – For mobile sensors have no built-in GPS and need to be localized by the algorithms. There are anchor nodes that are equipped with built-in GPS and known l ...
... for Localization in Mobile Networks – Con’d • A general framework and Three novel localization schemes were developed then for mobile networks. – For mobile sensors have no built-in GPS and need to be localized by the algorithms. There are anchor nodes that are equipped with built-in GPS and known l ...
Computer Network Security Protocols and Standards
... applications requiring secure communications. On the other hand, S-HTTP has its data passed in named text fields in the HTTP header. – Finally in terms of distribution and acceptance, history has not been so good to S-HTTP. While SSL was released in a free mass circulating browser, the Netscape Navi ...
... applications requiring secure communications. On the other hand, S-HTTP has its data passed in named text fields in the HTTP header. – Finally in terms of distribution and acceptance, history has not been so good to S-HTTP. While SSL was released in a free mass circulating browser, the Netscape Navi ...
Backbone Networks, MAN, WAN
... voice and data traffic over WANs. It is also used in backbone networks. In the WAN, ATM almost always uses SONET as its hardware layer. An ATM gateway is needed to convert TCP/IP and Ethernet frames into ATM cells and then converts them back once they have reached their destination network. The tran ...
... voice and data traffic over WANs. It is also used in backbone networks. In the WAN, ATM almost always uses SONET as its hardware layer. An ATM gateway is needed to convert TCP/IP and Ethernet frames into ATM cells and then converts them back once they have reached their destination network. The tran ...
Application Layer Functionality and Protocols
... Describe how a switch can eliminate collisions, backoffs and re- transmissions, the leading factors in reduced throughput on a hub-based Ethernet network ...
... Describe how a switch can eliminate collisions, backoffs and re- transmissions, the leading factors in reduced throughput on a hub-based Ethernet network ...
Document
... How to urbanize networks with autonomous dynamic services ? How to efficiently manage such heterogeneous services for providing efficient solutions inside the network ? ...
... How to urbanize networks with autonomous dynamic services ? How to efficiently manage such heterogeneous services for providing efficient solutions inside the network ? ...
Lecture26 - The University of Texas at Dallas
... Downloader and rootkit component SMTP spamming component Email address harvester Email propagation component DDoS tool ...
... Downloader and rootkit component SMTP spamming component Email address harvester Email propagation component DDoS tool ...
Networking Basics Introducing Basic Network Concepts *In the
... • Most networks have a limitation on the amount of data that can be included in a single PDU. • The Transport layer divides application data into blocks of data that are an appropriate size. • At the destination, the Transport layer reassembles the data before sending it to the destination applicati ...
... • Most networks have a limitation on the amount of data that can be included in a single PDU. • The Transport layer divides application data into blocks of data that are an appropriate size. • At the destination, the Transport layer reassembles the data before sending it to the destination applicati ...
data sheet
... performance The RFDPI engine is designed from the ground up with an emphasis on providing security scanning at a high level of performance, to match both the inherently parallel and ever-growing nature of network traffic. When combined with 24-, 32-, 48- or 96-core ...
... performance The RFDPI engine is designed from the ground up with an emphasis on providing security scanning at a high level of performance, to match both the inherently parallel and ever-growing nature of network traffic. When combined with 24-, 32-, 48- or 96-core ...
Identifying Security Risks
... • A wide area network (WAN) is one that offers networking services over a long distance, such as between cities, states, or countries • There are several interrelated elements that can be used to determine the intersection of a LAN with a WAN • One element is that the network topology may change bet ...
... • A wide area network (WAN) is one that offers networking services over a long distance, such as between cities, states, or countries • There are several interrelated elements that can be used to determine the intersection of a LAN with a WAN • One element is that the network topology may change bet ...
Selective Bit-error Checking at the MAC Layer for Voice Over Mobile
... (WLAN) wherein mobile nodes can communicate with one other without relying on any pre-existing infrastructure. In a MANET, all the mobile nodes have equal capabilities and operate not only as hosts but also as network routers. Communication links might be broken and a dynamic routing protocol is nee ...
... (WLAN) wherein mobile nodes can communicate with one other without relying on any pre-existing infrastructure. In a MANET, all the mobile nodes have equal capabilities and operate not only as hosts but also as network routers. Communication links might be broken and a dynamic routing protocol is nee ...
group6
... Algorithm: A modified version of the Distance Vector Table is being used which efficiently calculates the shortest path to the host which has the required contents Scalability: The method employed can be extended by using the unused bits of the IP address making the system scalable Latency: The meth ...
... Algorithm: A modified version of the Distance Vector Table is being used which efficiently calculates the shortest path to the host which has the required contents Scalability: The method employed can be extended by using the unused bits of the IP address making the system scalable Latency: The meth ...
Network Security
... • IP spoofing: – IP packets are not authenticated in any way. – An attacker can place any IP address as the source address of an IP datagram, so can be dangerous to base access control decisions on raw IP addresses alone. – An attacker may be able to replay, delay, reorder, modifiy or inject IP data ...
... • IP spoofing: – IP packets are not authenticated in any way. – An attacker can place any IP address as the source address of an IP datagram, so can be dangerous to base access control decisions on raw IP addresses alone. – An attacker may be able to replay, delay, reorder, modifiy or inject IP data ...