Cisco TrustSec How-To Guide: Segmenting Clients and Servers in
... Virtual server - physical server segmentation using SGFW (Figure 2). For this use case, we will deny all network traffic between the engineering server connected to the Cisco Nexus 7000 distribution switch and the virtual servers hosted behind the Cisco Nexus 7000 end-of-row switch. While SGFW is th ...
... Virtual server - physical server segmentation using SGFW (Figure 2). For this use case, we will deny all network traffic between the engineering server connected to the Cisco Nexus 7000 distribution switch and the virtual servers hosted behind the Cisco Nexus 7000 end-of-row switch. While SGFW is th ...
Slide 1
... RPC connects applications over the network with the familiar abstraction of procedure calls • Stubs package parameters/results into a message • UDP with retransmissions is a low-latency transport ...
... RPC connects applications over the network with the familiar abstraction of procedure calls • Stubs package parameters/results into a message • UDP with retransmissions is a low-latency transport ...
Reference Manual for the 54 Mbps Wireless Router WGR614 v6 202-10099-01, April 2005
... Statement of Conditions In the interest of improving internal design, operational function, and/or reliability, NETGEAR reserves the right to make changes to the products described in this document without notice. NETGEAR does not assume any liability that may occur due to the use or application of ...
... Statement of Conditions In the interest of improving internal design, operational function, and/or reliability, NETGEAR reserves the right to make changes to the products described in this document without notice. NETGEAR does not assume any liability that may occur due to the use or application of ...
IP: Addresses and Forwarding - RPI ECSE
... dedicated T-1 link, but without the expense of multiple dedicated circuits. Frame Relay leverages the underlying telephone network Frame Relay distance-insensitive and average-rate pricing is an ideal, cost-effective solution for networks with bursty traffic ...
... dedicated T-1 link, but without the expense of multiple dedicated circuits. Frame Relay leverages the underlying telephone network Frame Relay distance-insensitive and average-rate pricing is an ideal, cost-effective solution for networks with bursty traffic ...
BSCI 2.0 - Information Systems Technology
... –Purpose is to encrypt & authenticate routing information –This is an interface specific configuration –Routers will only accept routing information from other routers that have been configured with the same password or authentication information ...
... –Purpose is to encrypt & authenticate routing information –This is an interface specific configuration –Routers will only accept routing information from other routers that have been configured with the same password or authentication information ...
Compatible Systems Reference Guides
... The Device View displays a list of configurations. These configurations may be generic configuration files which are not associated with a particular device, or they may be a specific device’s configuration file. The File menu allows you to add both types of configurations to the Device View. Includ ...
... The Device View displays a list of configurations. These configurations may be generic configuration files which are not associated with a particular device, or they may be a specific device’s configuration file. The File menu allows you to add both types of configurations to the Device View. Includ ...
Seamless Vertical Handoff over Heterogeneous Network
... Horizontal v.s. Vertical Handoff How to achieve seamless vertical handoff ? How to pass NAT gateway ? How to adapt TCP behavior ? How to adapt application behavior ? ...
... Horizontal v.s. Vertical Handoff How to achieve seamless vertical handoff ? How to pass NAT gateway ? How to adapt TCP behavior ? How to adapt application behavior ? ...
What Is a Virtual Private Network?
... The Secure Sockets Layer (SSL)—SSL is a security protocol that was originally developed by Netscape Communications (SSL versions 1, 2, and 3), and it provides secure remote access for mobile users or home users. Functionality may be limited (when compared with L2F, PPTP, L2TPv2, or IPsec) if clientl ...
... The Secure Sockets Layer (SSL)—SSL is a security protocol that was originally developed by Netscape Communications (SSL versions 1, 2, and 3), and it provides secure remote access for mobile users or home users. Functionality may be limited (when compared with L2F, PPTP, L2TPv2, or IPsec) if clientl ...
20070227-P2PSIP
... • Client and server communicate using a well defined protocol • Server stores all the service logic (centralized architecture) • Clients (dumb) ask the server to perform tasks for them • Clients can only use what the server provides and allows • Communication between clients goes through the server ...
... • Client and server communicate using a well defined protocol • Server stores all the service logic (centralized architecture) • Clients (dumb) ask the server to perform tasks for them • Clients can only use what the server provides and allows • Communication between clients goes through the server ...
Slide 1
... •Testing can be applied to two different Diff Serv values at the same time, this allows for VoIP and non VoIP loading to be sent at the same time. •Testing is always full duplex – the Blaster Manager/Sink systems send and receive RTP and RTCP APP frames. Deployment:•The Blaster Managers ...
... •Testing can be applied to two different Diff Serv values at the same time, this allows for VoIP and non VoIP loading to be sent at the same time. •Testing is always full duplex – the Blaster Manager/Sink systems send and receive RTP and RTCP APP frames. Deployment:•The Blaster Managers ...
Wireless Application Development Issues
... from various sources and translate it into information that has value to a consumer. They must handle the technical details of extraction, summarization, transfer, and presentation. They must work within the constraints of the systems, networks, and devices used to process and deliver the informatio ...
... from various sources and translate it into information that has value to a consumer. They must handle the technical details of extraction, summarization, transfer, and presentation. They must work within the constraints of the systems, networks, and devices used to process and deliver the informatio ...
Institutionen f r systemteknik ö
... A Tactical Data Link (TDL) system has been deployed in many military missions as a winning strategy. The performance of a TDL system is governed by the MAC protocol. The MAC protocol that is able to provide more flexibility and high quality of services is more desirable. However, most MAC protocols ...
... A Tactical Data Link (TDL) system has been deployed in many military missions as a winning strategy. The performance of a TDL system is governed by the MAC protocol. The MAC protocol that is able to provide more flexibility and high quality of services is more desirable. However, most MAC protocols ...
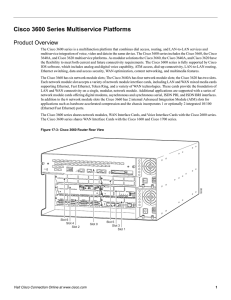
Cisco 3600 Series Multiservice Platforms
... The Cisco 3600 series is a multifunction platform that combines dial access, routing, and LAN-to-LAN services and multiservice integration of voice, video and data in the same device. The Cisco 3600 series includes the Cisco 3660, the Cisco 3640A, and Cisco 3620 multiservice platforms. As modular so ...
... The Cisco 3600 series is a multifunction platform that combines dial access, routing, and LAN-to-LAN services and multiservice integration of voice, video and data in the same device. The Cisco 3600 series includes the Cisco 3660, the Cisco 3640A, and Cisco 3620 multiservice platforms. As modular so ...
IP Multicasting: Concepts, Algorithms, and Protocols
... which a host needs to find out whether a certain type of service is available or not. Internet protocols such as Bootstrap Protocol (BOOTP) and Open Shortest path First (OSPF) protocol are among these applications. Using multicast messages and sending the query to those hosts which are potentially c ...
... which a host needs to find out whether a certain type of service is available or not. Internet protocols such as Bootstrap Protocol (BOOTP) and Open Shortest path First (OSPF) protocol are among these applications. Using multicast messages and sending the query to those hosts which are potentially c ...
L_06_ch_13_DLL_LAN_Ethernet
... The 10-Mbps capacity in each segment is now shared between 6 stations (actually 7 because the bridge acts as a station in each segment), not 12 stations. In a network with a heavy load, each station theoretically is offered 10/6 Mbps instead of 10/12 Mbps, assuming that the traffic is not going thro ...
... The 10-Mbps capacity in each segment is now shared between 6 stations (actually 7 because the bridge acts as a station in each segment), not 12 stations. In a network with a heavy load, each station theoretically is offered 10/6 Mbps instead of 10/12 Mbps, assuming that the traffic is not going thro ...
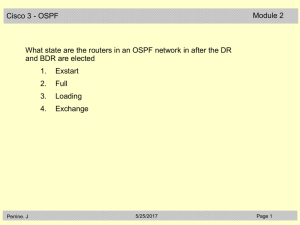
20088-2 CCNA3 3.1-02 Questions OSPF
... The link-state database is stored in a designated router and is accessed by each router in the area as needed. ...
... The link-state database is stored in a designated router and is accessed by each router in the area as needed. ...
Lecture PowerPoint Chapter 2
... 2-4 TCP/IP PROTOCOL SUITE The layers in the TCP/IP protocol suite do not exactly match those in the OSI model. The original TCP/IP protocol suite was defined as having four layers: host-tonetwork, internet, transport, and application. However, when TCP/IP is compared to OSI, we can say that the TCP ...
... 2-4 TCP/IP PROTOCOL SUITE The layers in the TCP/IP protocol suite do not exactly match those in the OSI model. The original TCP/IP protocol suite was defined as having four layers: host-tonetwork, internet, transport, and application. However, when TCP/IP is compared to OSI, we can say that the TCP ...
MPLS Basic Lab
... is routed through the network according to a management view of the availability of resources and the current and expected traffic – The class of service and quality of service required for the data can also be factored into this process Copyright 2011 Kenneth M. Chipps Ph.D. www.chipps.com ...
... is routed through the network according to a management view of the availability of resources and the current and expected traffic – The class of service and quality of service required for the data can also be factored into this process Copyright 2011 Kenneth M. Chipps Ph.D. www.chipps.com ...
ESnet - Indico
... • ESnet provides network and collaboration services to Office of Science laboratories and to sites of other DOE programs in cases where this increases cost ...
... • ESnet provides network and collaboration services to Office of Science laboratories and to sites of other DOE programs in cases where this increases cost ...
Q1 on FINAL
... What is important to remember about the data link layer of the OSI model when considering Peer to Peer communication? (Choose three.) ...
... What is important to remember about the data link layer of the OSI model when considering Peer to Peer communication? (Choose three.) ...
Comparative firewall study - Torsten Hoefler - Qucosa
... Imagine you would have to administer the network of a company. It should be used for sending emails and storing business data centrally. The company plans also to provide access to the world wide web and many other patterns of utilisation. Therefore the private network will be connected to the Inter ...
... Imagine you would have to administer the network of a company. It should be used for sending emails and storing business data centrally. The company plans also to provide access to the world wide web and many other patterns of utilisation. Therefore the private network will be connected to the Inter ...
Multicast Virtual Private Networks
... Every day more technology is utilizing digital methods of communication. The popular example of this is television, where a handful of channels were sent using analog radio waves directly to an antenna on a house. There was nothing in between. Today television content is created digitally then packa ...
... Every day more technology is utilizing digital methods of communication. The popular example of this is television, where a handful of channels were sent using analog radio waves directly to an antenna on a house. There was nothing in between. Today television content is created digitally then packa ...