Configuring Network Address Translation: Getting Started
... Overlapping networks result when you assign IP addresses to internal devices that are already being used by other devices within the internet. Overlapping networks also result when two companies, both of whom use RFC 1918 IP addresses in their networks, merge. These two networks need to communicate, ...
... Overlapping networks result when you assign IP addresses to internal devices that are already being used by other devices within the internet. Overlapping networks also result when two companies, both of whom use RFC 1918 IP addresses in their networks, merge. These two networks need to communicate, ...
PCC: Re-architecting Congestion Control for Consistent High Performance
... scenarios above. Fundamentally, picking an optimal predefined and hardwired control response is hard because for the same packet-level events, a control response optimal under one network scenario can decimate performance in even a slightly different scenario. The approach taken by a large number of ...
... scenarios above. Fundamentally, picking an optimal predefined and hardwired control response is hard because for the same packet-level events, a control response optimal under one network scenario can decimate performance in even a slightly different scenario. The approach taken by a large number of ...
International Technical Support Organization Asynchronous
... When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. Copyright International Business Machines Corporation 1995. All rights reserved. Note to U.S. Government Users — Do ...
... When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. Copyright International Business Machines Corporation 1995. All rights reserved. Note to U.S. Government Users — Do ...
Cloud and Network Services
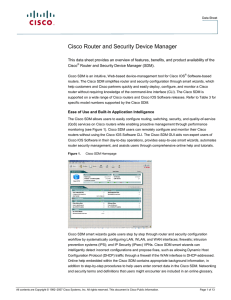
... fast integration of NAC and client security posture management into an existing network infrastructure. Figure 3. ...
... fast integration of NAC and client security posture management into an existing network infrastructure. Figure 3. ...
Annex B – Routing Area Reorganization in IETF (as of Nov
... The transmission of information over optical media in a systematic manner is an optical transport network. The optical transport network consists of the networking capabilities/functionalities and the technologies required to support them. For the purposes of this standardization and work plan, all ...
... The transmission of information over optical media in a systematic manner is an optical transport network. The optical transport network consists of the networking capabilities/functionalities and the technologies required to support them. For the purposes of this standardization and work plan, all ...
Ch05 ver 1.1
... Example 5.19 Figure 5.24 shows the same network in Figure 5.23 after subnetting. The whole network is still connected to the Internet through the same router. However, the network has used a private router to divide the network into four subnetworks. The rest of the Internet still sees only one net ...
... Example 5.19 Figure 5.24 shows the same network in Figure 5.23 after subnetting. The whole network is still connected to the Internet through the same router. However, the network has used a private router to divide the network into four subnetworks. The rest of the Internet still sees only one net ...
BIG-IP Global Traffic Manager | F5 Datasheet
... BIG‑IP instances, removing repeat configurations across devices. • Data center and sync groups—Create logical groups of network equipment to ensure efficient use of monitoring and metrics collection for intelligently sharing with members in the logical group. • Distributed application management—Y ...
... BIG‑IP instances, removing repeat configurations across devices. • Data center and sync groups—Create logical groups of network equipment to ensure efficient use of monitoring and metrics collection for intelligently sharing with members in the logical group. • Distributed application management—Y ...
IP Multicast
... 1. Link-layer (Ethernet) broadcast •IP multicast packet is encapsulated in an Ethernet broadcast frame and transmitted on the bus. •Every host picks up the Ethernet frame and does filtering at the IP layer to decide whether to keep or discard the frame. •Redundant reception by many hosts. 2. Link-la ...
... 1. Link-layer (Ethernet) broadcast •IP multicast packet is encapsulated in an Ethernet broadcast frame and transmitted on the bus. •Every host picks up the Ethernet frame and does filtering at the IP layer to decide whether to keep or discard the frame. •Redundant reception by many hosts. 2. Link-la ...
project report
... "The beauty of the Internet and the IETF lies in a simple idea - that the only standards under consideration are those already in use on the Net. Ready, fire, aim!" -Robert X. Cringely ...
... "The beauty of the Internet and the IETF lies in a simple idea - that the only standards under consideration are those already in use on the Net. Ready, fire, aim!" -Robert X. Cringely ...
Repeaters, Switches and Routers
... broadcast goes around a loop and enters a single switch from two different segments. In that case, switches keep forwarding frames out more than one port, so they are forwarding frames to themselves. ...
... broadcast goes around a loop and enters a single switch from two different segments. In that case, switches keep forwarding frames out more than one port, so they are forwarding frames to themselves. ...
The Gartner Glossary of Information Technology Acronyms and Terms
... enterprise. It provides the information for activity-based management, which focuses on the decisions and actions needed to reduce costs and increase revenue. ABC differs from traditional cost accounting in explicitly recognizing that not all cost objects place an equal demand on support resources. ...
... enterprise. It provides the information for activity-based management, which focuses on the decisions and actions needed to reduce costs and increase revenue. ABC differs from traditional cost accounting in explicitly recognizing that not all cost objects place an equal demand on support resources. ...
Business Roles and Architecture to realize MUSE
... A pool of unallocated quota and the IP addresses of Border Nodes that are allowed to use the pool. IP address of Border Nodes (for requesting quota). Information of quota that is reserved for future use (at a certain time & for a certain time period) and IP addresses of reserving Border Nodes. Quota ...
... A pool of unallocated quota and the IP addresses of Border Nodes that are allowed to use the pool. IP address of Border Nodes (for requesting quota). Information of quota that is reserved for future use (at a certain time & for a certain time period) and IP addresses of reserving Border Nodes. Quota ...
Top-Down Network Design
... Priscilla Oppenheimer has been developing data communications and networking systems since 1980 when she earned her master’s degree in information science from the University of Michigan. After many years as a software developer, she became a technical instructor and training developer and has taugh ...
... Priscilla Oppenheimer has been developing data communications and networking systems since 1980 when she earned her master’s degree in information science from the University of Michigan. After many years as a software developer, she became a technical instructor and training developer and has taugh ...
Defense
... Next it allocates a new request data structure and adds the tunneled attributes to the request. It then calls the rad_authenticate () function with the new request packet as the parameter to handle the tunneled EAP-Type MS-CHAPv2. ...
... Next it allocates a new request data structure and adds the tunneled attributes to the request. It then calls the rad_authenticate () function with the new request packet as the parameter to handle the tunneled EAP-Type MS-CHAPv2. ...
CCNA5.0 Instructor PPT - Bina Darma e
... Main components of dynamic routing protocols include: Data structures - Routing protocols typically use tables or databases for its operations. This information is kept in RAM. Routing protocol messages - Routing protocols use various types of messages to discover neighboring routers, exchange r ...
... Main components of dynamic routing protocols include: Data structures - Routing protocols typically use tables or databases for its operations. This information is kept in RAM. Routing protocol messages - Routing protocols use various types of messages to discover neighboring routers, exchange r ...
TCP - Rudra Dutta
... Until avoidance algorithm allows window advertisement May result in delaying ACK until there is data to send, so can “piggyback” ACK with data May result in single ACK for multiple segments ...
... Until avoidance algorithm allows window advertisement May result in delaying ACK until there is data to send, so can “piggyback” ACK with data May result in single ACK for multiple segments ...
ATM End User
... • Signaling performed through dedicated Virtual Channels. - UNI signaling VC: VPI=0, VCI =5 ...
... • Signaling performed through dedicated Virtual Channels. - UNI signaling VC: VPI=0, VCI =5 ...
D1.1: Functional Architecture Definition and Top Level
... blocks, enabling him to implement relative packet differentiation. However, it is not clear yet how “real” customer services, such as interactive multimedia including voice over IP, can be build on top of this. The DiffServ architecture has some shortcomings at this time. Deploying QoS sensitive cus ...
... blocks, enabling him to implement relative packet differentiation. However, it is not clear yet how “real” customer services, such as interactive multimedia including voice over IP, can be build on top of this. The DiffServ architecture has some shortcomings at this time. Deploying QoS sensitive cus ...
LABEL SPACE REDUCTION IN GMPLS AND ALL-OPTICAL LABEL SWAPPING NETWORKS
... The evolution of computer networks in the Internet has propelled Optical Transport Networks (OTN) in recent years. While the optical switching granularity has evolved from fibers to wavelengths to bursts to packets with very promising designs, fully-optical forwarding functions are still a newly bor ...
... The evolution of computer networks in the Internet has propelled Optical Transport Networks (OTN) in recent years. While the optical switching granularity has evolved from fibers to wavelengths to bursts to packets with very promising designs, fully-optical forwarding functions are still a newly bor ...
Presentation
... multiple replicas of data at remote sites Caching (obviously) to reducing latency Replication: multiple requests to multiple copies and just use the quickest reply Prefetching to reduce latency Large block sizes for disk and memory Protocol: few very large messages – vs. chatty protocol with lots sm ...
... multiple replicas of data at remote sites Caching (obviously) to reducing latency Replication: multiple requests to multiple copies and just use the quickest reply Prefetching to reduce latency Large block sizes for disk and memory Protocol: few very large messages – vs. chatty protocol with lots sm ...
Reputation based Trust in Service-Oriented Network Environments by
... as a denial-of-service attack on the victim router and results in the inability of a victim router to provide routing services as it should. An example of this type of attack is evidenced in an incident that diverted traffic away from YouTube’s [11] network [72, 27, 67]. “Routers” and “Routing devic ...
... as a denial-of-service attack on the victim router and results in the inability of a victim router to provide routing services as it should. An example of this type of attack is evidenced in an incident that diverted traffic away from YouTube’s [11] network [72, 27, 67]. “Routers” and “Routing devic ...
Why Latency Lags Bandwidth, and What it Means to Computing
... multiple replicas of data at remote sites Caching (obviously) to reducing latency Replication: multiple requests to multiple copies and just use the quickest reply Prefetching to reduce latency Large block sizes for disk and memory Protocol: few very large messages – vs. chatty protocol with lots sm ...
... multiple replicas of data at remote sites Caching (obviously) to reducing latency Replication: multiple requests to multiple copies and just use the quickest reply Prefetching to reduce latency Large block sizes for disk and memory Protocol: few very large messages – vs. chatty protocol with lots sm ...
TTAS tandard - TTA표준화 위원회
... operator to offload some traffic(e.g. best effort) to the WLAN access. At the same time it may be beneficial to still keep some traffic(e.g. VoIP flow) in the cellular access. With this IP flow mobility solution the operator can lower it data access costs while the subscriber just experiences maximi ...
... operator to offload some traffic(e.g. best effort) to the WLAN access. At the same time it may be beneficial to still keep some traffic(e.g. VoIP flow) in the cellular access. With this IP flow mobility solution the operator can lower it data access costs while the subscriber just experiences maximi ...
The OAM Jigsaw Puzzle
... Programmable OAM Flow Classification: All incoming traffic is snooped by this block. OAM messages are subject to flow classification. The flow classification engine is programmable, providing the flexibility to classify flows of any OAM protocols, including tunnel-encapsulated packets and future pac ...
... Programmable OAM Flow Classification: All incoming traffic is snooped by this block. OAM messages are subject to flow classification. The flow classification engine is programmable, providing the flexibility to classify flows of any OAM protocols, including tunnel-encapsulated packets and future pac ...