Understanding the Methods of Network Attacks
... For example, consider human vulnerabilities. Because most attacks against information systems are launched from people on the “inside,” controls should be set up to prevent the intentional or unintentional misuse of information systems. Social engineering is an example of unintentional misuse. To il ...
... For example, consider human vulnerabilities. Because most attacks against information systems are launched from people on the “inside,” controls should be set up to prevent the intentional or unintentional misuse of information systems. Social engineering is an example of unintentional misuse. To il ...
Document
... Subroutine ? is more efficient. This measure is good for all large input sizes In fact, we will not worry about the exact values, but will look at ``broad classes’ of values, or the growth rates Let there be n inputs. If an algorithm needs n basic operations and another needs 2n basic operations, we ...
... Subroutine ? is more efficient. This measure is good for all large input sizes In fact, we will not worry about the exact values, but will look at ``broad classes’ of values, or the growth rates Let there be n inputs. If an algorithm needs n basic operations and another needs 2n basic operations, we ...
Security Analysis of a Single Sign
... The Single sign-on (SSO) is a new authentication mechanism that enables a legal user with a single credential to be authenticated by multiple service providers in a distributed computer network. Recently, Chang and Lee proposed a new SSO scheme and claimed its security by providing well-organized se ...
... The Single sign-on (SSO) is a new authentication mechanism that enables a legal user with a single credential to be authenticated by multiple service providers in a distributed computer network. Recently, Chang and Lee proposed a new SSO scheme and claimed its security by providing well-organized se ...
Optimization_2016_JS
... The mathematical relationships between the objective function, constraints and the decision variables determine what type of an optimization problem one is dealing with, i.e. • how hard it is to solve • the solution methods or algorithms that can be used for optimization • the confidence you can hav ...
... The mathematical relationships between the objective function, constraints and the decision variables determine what type of an optimization problem one is dealing with, i.e. • how hard it is to solve • the solution methods or algorithms that can be used for optimization • the confidence you can hav ...
A Survey of BGP Security: Issues and Solutions
... with ASes that can Originate Addresses ▫ Intrusion Detection: Observe Address Ownership over Time, Flag Unexpected Changes ▫ Prefix Hijacking Alert System: Server Alerts Valid Originator Upon Hijack ▫ Pretty Good BGP: Monitor Historic Routing Data to Flag Unexpected Routes as Suspicious ...
... with ASes that can Originate Addresses ▫ Intrusion Detection: Observe Address Ownership over Time, Flag Unexpected Changes ▫ Prefix Hijacking Alert System: Server Alerts Valid Originator Upon Hijack ▫ Pretty Good BGP: Monitor Historic Routing Data to Flag Unexpected Routes as Suspicious ...
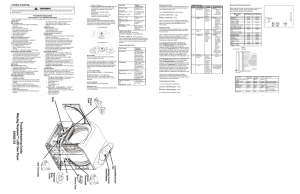
Troubleshooting Guide Maytag Neptune™ LED Gas Dryer 6390 2110
... Test. To exit the test at any point, press the same keys again for 2 seconds or press the OFF key to exit Service Mode. Diagnostic Codes The Diagnostic Codes are identified when the severity level of the abnormality detected is higher and service may be required. When a problem with the dryer is det ...
... Test. To exit the test at any point, press the same keys again for 2 seconds or press the OFF key to exit Service Mode. Diagnostic Codes The Diagnostic Codes are identified when the severity level of the abnormality detected is higher and service may be required. When a problem with the dryer is det ...
CADD LEGACY PCA Model 6300
... ENTER key to change the Demand Dose Lockout. NOTE: if no Demand Dose was programmed, this screen will NOT be displayed. 13. Enter the “Max Doses Per Hour”. The range available will be displayed at the bottom of this programming screen. Use the up/down arrow key to scroll to the desired number and pr ...
... ENTER key to change the Demand Dose Lockout. NOTE: if no Demand Dose was programmed, this screen will NOT be displayed. 13. Enter the “Max Doses Per Hour”. The range available will be displayed at the bottom of this programming screen. Use the up/down arrow key to scroll to the desired number and pr ...
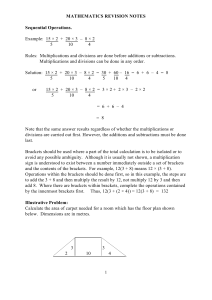
MATHEMATICS REVISION NOTES Sequential Operations. Example
... [See the next section for the proof of this.] ...
... [See the next section for the proof of this.] ...
IPSec
... IPSec is an abbreviation for IP security, which is used to transfer data securely over unprotected networks like “Internet”. It acts at the networks layer and is part of IPv6. The protocol/process is as follows : Sender encrypts packets before sending them on the network. Receiver authenti ...
... IPSec is an abbreviation for IP security, which is used to transfer data securely over unprotected networks like “Internet”. It acts at the networks layer and is part of IPv6. The protocol/process is as follows : Sender encrypts packets before sending them on the network. Receiver authenti ...
Spam and Anti-Spam Measures: A Look at Potential Impacts
... a particular mail server is often used for sending spam it is possible to configure the own mail server such that mails from the suspicious server are no longer accepted. such blocking approaches can use IPs address, domain names and other information provided during the "handshake" between mail ser ...
... a particular mail server is often used for sending spam it is possible to configure the own mail server such that mails from the suspicious server are no longer accepted. such blocking approaches can use IPs address, domain names and other information provided during the "handshake" between mail ser ...
vasserman_foci12_slides
... against random verify manifest against file manifest by chunks manifest by (hash) (hash) ...
... against random verify manifest against file manifest by chunks manifest by (hash) (hash) ...
PK b
... assuming the PEKS is semantically secure against an adaptive chosen message attack.(once can send a bit?) Building non-interactive public-key searchable encryption is at least as hard as building an IBE system. ...
... assuming the PEKS is semantically secure against an adaptive chosen message attack.(once can send a bit?) Building non-interactive public-key searchable encryption is at least as hard as building an IBE system. ...
EAP
... • Mobile communication technology will continue to grow encouraged by switching to packet-switched 3G cellular phones • Results in natural progression to accessing the internet without wires • Results in requiring more privacy/security ...
... • Mobile communication technology will continue to grow encouraged by switching to packet-switched 3G cellular phones • Results in natural progression to accessing the internet without wires • Results in requiring more privacy/security ...
Electronic Commerce and Information Security
... Main parts of information security: Encryption and authentication ...
... Main parts of information security: Encryption and authentication ...
Data Encryption Standard - gozips.uakron.edu
... Source address – start-point IP address Destination address – end-point IP address ...
... Source address – start-point IP address Destination address – end-point IP address ...
Introduction to Information Security Chapter N
... Algorithm: the mathematical formula used to convert an unencrypted message into an encrypted message. Cipher: the transformation of the individual components (characters, bytes, or bits) of an unencrypted message into encrypted components. Ciphertext or cryptogram: the unintelligible encrypted ...
... Algorithm: the mathematical formula used to convert an unencrypted message into an encrypted message. Cipher: the transformation of the individual components (characters, bytes, or bits) of an unencrypted message into encrypted components. Ciphertext or cryptogram: the unintelligible encrypted ...
(FIPS) 140-2 - Aviat Networks
... • Mandates identity-based authentication, tamper evidence, etc) • Level 3 and 4: VERY STRONG • Must be pick-resistant, tamper-proof. Adds large cost and complexity to product to ...
... • Mandates identity-based authentication, tamper evidence, etc) • Level 3 and 4: VERY STRONG • Must be pick-resistant, tamper-proof. Adds large cost and complexity to product to ...
HumanAut (or SecHCI: Secure Human
... The responses to challenges should be designed to be almost impossible (i.e., very very difficult) for kids (even teaching them how to use the protocols is difficult), but capable for most adults (usability can be relaxed, for example, it is still OK if some training is needed). ...
... The responses to challenges should be designed to be almost impossible (i.e., very very difficult) for kids (even teaching them how to use the protocols is difficult), but capable for most adults (usability can be relaxed, for example, it is still OK if some training is needed). ...
Guide to Operating System Security
... encryption permitted by OS Use longest encryption keys possible Inventory encryption and authentication methods used by OS; close any holes Have administrators use personal accounts with administrative privileges (rather than use ...
... encryption permitted by OS Use longest encryption keys possible Inventory encryption and authentication methods used by OS; close any holes Have administrators use personal accounts with administrative privileges (rather than use ...
CIS 4362
... can recover using cube root Smooth number threat – product of small primes Need to pad properly ...
... can recover using cube root Smooth number threat – product of small primes Need to pad properly ...
Systeemanalyse in Ontwerpprojecten
... Framework of Thinking, cont. • Security Services (SSs) are functions that enhance the security requirements of an information system (i.e., the probability that an IS is in a secure state) • Example SSs are identification, authentication, authorization, (role-based) access control, certification, d ...
... Framework of Thinking, cont. • Security Services (SSs) are functions that enhance the security requirements of an information system (i.e., the probability that an IS is in a secure state) • Example SSs are identification, authentication, authorization, (role-based) access control, certification, d ...
Net+ Chapter 1
... encrypted and decrypted during transmission. • Also, all of the data transmitted across the connection contains a mechanism to detect tampering, so the data can be checked to see if it was altered during the transfer process. ...
... encrypted and decrypted during transmission. • Also, all of the data transmitted across the connection contains a mechanism to detect tampering, so the data can be checked to see if it was altered during the transfer process. ...
Cryptanalysis

Cryptanalysis (from the Greek kryptós, ""hidden"", and analýein, ""to loosen"" or ""to untie"") is the study of analyzing information systems in order to study the hidden aspects of the systems. Cryptanalysis is used to breach cryptographic security systems and gain access to the contents of encrypted messages, even if the cryptographic key is unknown.In addition to mathematical analysis of cryptographic algorithms, cryptanalysis includes the study of side-channel attacks that do not target weaknesses in the cryptographic algorithms themselves, but instead exploit weaknesses in their implementation.Even though the goal has been the same, the methods and techniques of cryptanalysis have changed drastically through the history of cryptography, adapting to increasing cryptographic complexity, ranging from the pen-and-paper methods of the past, through machines like the British Bombes and Colossus computers at Bletchley Park in World War II, to the mathematically advanced computerized schemes of the present. Methods for breaking modern cryptosystems often involve solving carefully constructed problems in pure mathematics, the best-known being integer factorization.