Protection Mechanisms
... user’s identity by means of a password, passphrase, or other unique code A password is a private word or combination of characters that only the user should know A passphrase is a plain-language phrase, typically longer than a password, from which a virtual password is derived A good rule of t ...
... user’s identity by means of a password, passphrase, or other unique code A password is a private word or combination of characters that only the user should know A passphrase is a plain-language phrase, typically longer than a password, from which a virtual password is derived A good rule of t ...
Computer and Information Security
... • Is the web site I am downloading information from a legitimate one, or a fake? • How do I ensure that the person I just did a financial transaction denies having done it tomorrow or at a later time? • I want to buy some thing online, but I don’t want to let them charge my credit card before they d ...
... • Is the web site I am downloading information from a legitimate one, or a fake? • How do I ensure that the person I just did a financial transaction denies having done it tomorrow or at a later time? • I want to buy some thing online, but I don’t want to let them charge my credit card before they d ...
Document
... (2) In each node, its key is larger than the keys of all vertices in its left subtree and smaller than the keys of all the vertices in its right subtree. ...
... (2) In each node, its key is larger than the keys of all vertices in its left subtree and smaller than the keys of all the vertices in its right subtree. ...
Slides
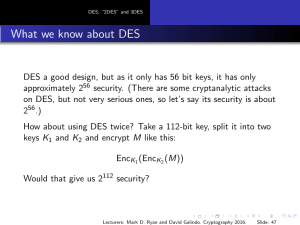
... There is a meet-in-the-middle key recovery attack for AES-128. It requires 2126 operations, so it is only about four times faster than brute-force. There is a “related key” attack on AES-192 and AES-256. This means that if you use two keys that are related in a certain way, the security may be reduc ...
... There is a meet-in-the-middle key recovery attack for AES-128. It requires 2126 operations, so it is only about four times faster than brute-force. There is a “related key” attack on AES-192 and AES-256. This means that if you use two keys that are related in a certain way, the security may be reduc ...
Document
... (4) Write the program for BST of student records (student’s id is used as key). The program must contain the following 5 operations: • Search a node (given a student id), and print the record when it is found. • Insert a node (given a new student record) • Delete a node (given a student id) • Print ...
... (4) Write the program for BST of student records (student’s id is used as key). The program must contain the following 5 operations: • Search a node (given a student id), and print the record when it is found. • Insert a node (given a new student record) • Delete a node (given a student id) • Print ...
CHAPTER FIVE
... not useful in public key cryptography, in public key. We need a special type of one –way function, that is trap-door one-way function, which has a secret door (secret key) used to reverse the other direction .i.e giving f(x) and some secret Value we can deduce. 5.3 PUBLIC KEY CRY TOGRAPHY: ...
... not useful in public key cryptography, in public key. We need a special type of one –way function, that is trap-door one-way function, which has a secret door (secret key) used to reverse the other direction .i.e giving f(x) and some secret Value we can deduce. 5.3 PUBLIC KEY CRY TOGRAPHY: ...
03-WAS Common Threats - Professional Data Management
... • Measure 3: Daily checking of files for viruses and attack programs ...
... • Measure 3: Daily checking of files for viruses and attack programs ...
Factoring and RSA Codes using DERIVE
... One can also see that after increasing the number of Rabin-Miller tests by one the number in question is recognized as composite by PRIME and NEXT_PRIME. (Unfortunately, there is no way to make FACTOR work.) We will be also dealing with the question: What happens if p or q (or even both) are not pri ...
... One can also see that after increasing the number of Rabin-Miller tests by one the number in question is recognized as composite by PRIME and NEXT_PRIME. (Unfortunately, there is no way to make FACTOR work.) We will be also dealing with the question: What happens if p or q (or even both) are not pri ...
Chapter 1 Security Problems in Computing
... Choose a multiplier w and a modulus n, where n > S1 + … + SM and w is relprime to n. Note: Usually n is a prime, which is relprime to any number < n. Example: w = 19 and n = 303. ...
... Choose a multiplier w and a modulus n, where n > S1 + … + SM and w is relprime to n. Note: Usually n is a prime, which is relprime to any number < n. Example: w = 19 and n = 303. ...
Reading questions for each topic
... Section 7.2, focus on the first few pages, up to and including the first three paragraphs of page 98 (before the part about the speed of encryption/decryption algorithms.) Reading Questions 1. Explain why using asymmetric ciphers greatly reduces the number of keys required to maintain a communicatio ...
... Section 7.2, focus on the first few pages, up to and including the first three paragraphs of page 98 (before the part about the speed of encryption/decryption algorithms.) Reading Questions 1. Explain why using asymmetric ciphers greatly reduces the number of keys required to maintain a communicatio ...
Chapter 19: Security
... • Buffer overflow attacks – Occurs when an application sends more data to a buffer than it can hold – Can push the additional data into adjacent buffers, corrupting or overwriting existing data – A well-designed buffer overflow attack can replace executable code in an application’s stack to alter it ...
... • Buffer overflow attacks – Occurs when an application sends more data to a buffer than it can hold – Can push the additional data into adjacent buffers, corrupting or overwriting existing data – A well-designed buffer overflow attack can replace executable code in an application’s stack to alter it ...
Chapter 19: Security
... • Buffer overflow attacks – Occurs when an application sends more data to a buffer than it can hold – Can push the additional data into adjacent buffers, corrupting or overwriting existing data – A well-designed buffer overflow attack can replace executable code in an application’s stack to alter it ...
... • Buffer overflow attacks – Occurs when an application sends more data to a buffer than it can hold – Can push the additional data into adjacent buffers, corrupting or overwriting existing data – A well-designed buffer overflow attack can replace executable code in an application’s stack to alter it ...
Chapter 19: Security - Murray State University
... • Buffer overflow attacks – Occurs when an application sends more data to a buffer than it can hold – Can push the additional data into adjacent buffers, corrupting or overwriting existing data – A well-designed buffer overflow attack can replace executable code in an application’s stack to alter it ...
... • Buffer overflow attacks – Occurs when an application sends more data to a buffer than it can hold – Can push the additional data into adjacent buffers, corrupting or overwriting existing data – A well-designed buffer overflow attack can replace executable code in an application’s stack to alter it ...
WHAT IS EC SECURITY? - Joseph H. Schuessler, PhD
... message digest (MD) A summary of a message converted into a string of digits after the hash has been applied ...
... message digest (MD) A summary of a message converted into a string of digits after the hash has been applied ...
Secure Email
... privacy (only the intended recipient can read the message) and authentication (the recipient can be assured of the identity of the sender). The technical capabilities for these functions has been known for many years, but they have only been applied to Internet mail recently. – Reality Check: Securi ...
... privacy (only the intended recipient can read the message) and authentication (the recipient can be assured of the identity of the sender). The technical capabilities for these functions has been known for many years, but they have only been applied to Internet mail recently. – Reality Check: Securi ...
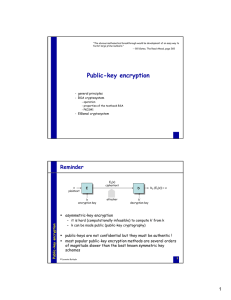
Public-key encryption
... recovering m given p, g, A, R, and C is equivalent to solving the Diffie-Hellman problem given the latest progress on the discrete logarithm problem, the size of the modulus p should at least be 1024 bits ...
... recovering m given p, g, A, R, and C is equivalent to solving the Diffie-Hellman problem given the latest progress on the discrete logarithm problem, the size of the modulus p should at least be 1024 bits ...
Still Image Compression
... She chooses a number e such that e is relatively prime to (n) and computes d, the inverse of e in Z (n ) (i.e., ed =1 mod \phi(n)) She publicizes the pair (e,n) as her public key.(e is called RSA exponent, n is called RSA modulus)She keeps d secret and destroys p, q, and (n) Plaintext and ciph ...
... She chooses a number e such that e is relatively prime to (n) and computes d, the inverse of e in Z (n ) (i.e., ed =1 mod \phi(n)) She publicizes the pair (e,n) as her public key.(e is called RSA exponent, n is called RSA modulus)She keeps d secret and destroys p, q, and (n) Plaintext and ciph ...
Linear Algebra Review
... guarantee that the multiplicative inverse a 1 mod 26 will exist. For an affine cipher, verifying that gcd(a, 26) = 1 was done by inspection and we will able to display all of the positive integers less than 26 that have multiplicative inverses in a table because the modulus 26 is so small. For an R ...
... guarantee that the multiplicative inverse a 1 mod 26 will exist. For an affine cipher, verifying that gcd(a, 26) = 1 was done by inspection and we will able to display all of the positive integers less than 26 that have multiplicative inverses in a table because the modulus 26 is so small. For an R ...
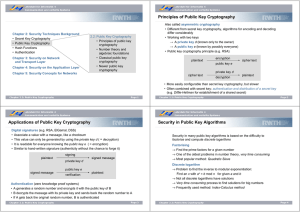
Principles of Public Key Cryptography Applications of
... a.) by choosing e at random and test if it is relatively prime to (p - 1) · (q - 1) b.) by choosing e first and then determine matching p and q → RSA is not less secure if always the same e is chosen → If e is small or its binary representation has few '1's, the operations for encryption and signatu ...
... a.) by choosing e at random and test if it is relatively prime to (p - 1) · (q - 1) b.) by choosing e first and then determine matching p and q → RSA is not less secure if always the same e is chosen → If e is small or its binary representation has few '1's, the operations for encryption and signatu ...
Jensen3
... • Conditions required to be met by the hash function for an effective traitor tracing algorithm, as specified by Chor et al., are not mentioned. – Traitor tracing algorithm needs to identify at least one traitor and reduce possibilities of a false positives. – For a k-resilient open user scheme the ...
... • Conditions required to be met by the hash function for an effective traitor tracing algorithm, as specified by Chor et al., are not mentioned. – Traitor tracing algorithm needs to identify at least one traitor and reduce possibilities of a false positives. – For a k-resilient open user scheme the ...
Apply encryption to network and system security
... Encryption is the process of taking some information or data, manipulating or changing its format in a way that stops it from being used or read by unauthorized people or systems. Encryption involves scrambling data so that it needs to be unscrambled, or decrypted, to be read. Encryption can be appl ...
... Encryption is the process of taking some information or data, manipulating or changing its format in a way that stops it from being used or read by unauthorized people or systems. Encryption involves scrambling data so that it needs to be unscrambled, or decrypted, to be read. Encryption can be appl ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... packets to each other .In MANET, [AODV] Adhoc on Demand Distance Vector routing protocol is frequently used. Popularity, on networking motivated the development of adhoc mobile networks .Adhoc mobile network is a continuously self-configuring ,infrastructure-less network connected to mobile devices ...
... packets to each other .In MANET, [AODV] Adhoc on Demand Distance Vector routing protocol is frequently used. Popularity, on networking motivated the development of adhoc mobile networks .Adhoc mobile network is a continuously self-configuring ,infrastructure-less network connected to mobile devices ...
Z Notation
... 1. Formal methods can guarantee that software is perfect. Rather: they are very helpful at finding errors early on and can nearly eliminate some classes of error. 2. They are all about program proving. Rather: they work largely by making you think very hard about the system you propose to build. 3. ...
... 1. Formal methods can guarantee that software is perfect. Rather: they are very helpful at finding errors early on and can nearly eliminate some classes of error. 2. They are all about program proving. Rather: they work largely by making you think very hard about the system you propose to build. 3. ...
Cryptanalysis

Cryptanalysis (from the Greek kryptós, ""hidden"", and analýein, ""to loosen"" or ""to untie"") is the study of analyzing information systems in order to study the hidden aspects of the systems. Cryptanalysis is used to breach cryptographic security systems and gain access to the contents of encrypted messages, even if the cryptographic key is unknown.In addition to mathematical analysis of cryptographic algorithms, cryptanalysis includes the study of side-channel attacks that do not target weaknesses in the cryptographic algorithms themselves, but instead exploit weaknesses in their implementation.Even though the goal has been the same, the methods and techniques of cryptanalysis have changed drastically through the history of cryptography, adapting to increasing cryptographic complexity, ranging from the pen-and-paper methods of the past, through machines like the British Bombes and Colossus computers at Bletchley Park in World War II, to the mathematically advanced computerized schemes of the present. Methods for breaking modern cryptosystems often involve solving carefully constructed problems in pure mathematics, the best-known being integer factorization.