Meyers_CompTIA_4e_PPT_Ch21
... • Put UTP wires into 66- and 110-blocks • Repunch a connection to make sure ...
... • Put UTP wires into 66- and 110-blocks • Repunch a connection to make sure ...
Reorder Notifying TCP (RN-TCP) with Explicit Packet Drop Notification (EPDN)
... IP header by including a new field called the EPDN-TTL (EPDN Time To Live). Adding an EPDN-TTL field to the IP header requires another 8 bits. Every EPDN enabled router, decrements the EPDN-TTL along with the actual TTL (Time To Live) while forwarding the packet. When the receiver receives the packe ...
... IP header by including a new field called the EPDN-TTL (EPDN Time To Live). Adding an EPDN-TTL field to the IP header requires another 8 bits. Every EPDN enabled router, decrements the EPDN-TTL along with the actual TTL (Time To Live) while forwarding the packet. When the receiver receives the packe ...
DMXrfNet II and DMXNet II Card Option
... The M-Class MarkII series of printers are available with several Communication Card options. These cards can be equipped in the following configurations: ...
... The M-Class MarkII series of printers are available with several Communication Card options. These cards can be equipped in the following configurations: ...
SpeedStream - Bell Customer Support Centre
... The following describes your license to use the software (the “Software”) that has been provided with your SSN DSL customer premises equipment (“Hardware”) and the limited warranty that SSN provides on its Software and Hardware. Software License The Software is protected by copyright laws and intern ...
... The following describes your license to use the software (the “Software”) that has been provided with your SSN DSL customer premises equipment (“Hardware”) and the limited warranty that SSN provides on its Software and Hardware. Software License The Software is protected by copyright laws and intern ...
WAP - ICMP - Extra Reading File
... fragmentation is required in order to forward a packet. – Fragmentation is usually necessary when a datagram is forwarded from a Token-Ring network to an Ethernet network. – If the datagram does not allow fragmentation, the packet cannot be forwarded, so a destination unreachable message will be sen ...
... fragmentation is required in order to forward a packet. – Fragmentation is usually necessary when a datagram is forwarded from a Token-Ring network to an Ethernet network. – If the datagram does not allow fragmentation, the packet cannot be forwarded, so a destination unreachable message will be sen ...
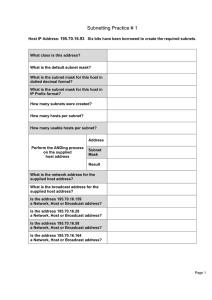
Subnetting Practice # 1
... You are the network administrator for Bunch-A-Hosts Limited in Windsor and are required to subnet the network according to the diagram. You have decided to use the network 172.16.0.0. There are multiple subnets at each site but you are only responsible for providing usable subnetworks with enough IP ...
... You are the network administrator for Bunch-A-Hosts Limited in Windsor and are required to subnet the network according to the diagram. You have decided to use the network 172.16.0.0. There are multiple subnets at each site but you are only responsible for providing usable subnetworks with enough IP ...
WAP - ICMP - Extra Reading File
... fragmentation is required in order to forward a packet. – Fragmentation is usually necessary when a datagram is forwarded from a Token-Ring network to an Ethernet network. – If the datagram does not allow fragmentation, the packet cannot be forwarded, so a destination unreachable message will be sen ...
... fragmentation is required in order to forward a packet. – Fragmentation is usually necessary when a datagram is forwarded from a Token-Ring network to an Ethernet network. – If the datagram does not allow fragmentation, the packet cannot be forwarded, so a destination unreachable message will be sen ...
User Manual for RCC Series Controller
... shall HE-APG or its suppliers be liable of any special, consequential, incidental or penal damages including, but not limited to, loss of profit or revenues, loss of use of the products or any associated equipment, damage to associated equipment, cost of capital, cost of substitute products, facilit ...
... shall HE-APG or its suppliers be liable of any special, consequential, incidental or penal damages including, but not limited to, loss of profit or revenues, loss of use of the products or any associated equipment, damage to associated equipment, cost of capital, cost of substitute products, facilit ...
Supporting Packet-Data QoS in Next
... for supporting real-time tranffic – For a given PDP address, only one QoS profile can be used: all application flows share same PDP context, and no per-flow prioritization is possible – do not allow QoS re-negotiation – QoS parameters are too vague and ambiguous in interpreting implementations, thus ...
... for supporting real-time tranffic – For a given PDP address, only one QoS profile can be used: all application flows share same PDP context, and no per-flow prioritization is possible – do not allow QoS re-negotiation – QoS parameters are too vague and ambiguous in interpreting implementations, thus ...
www.comcom.govt.nz
... transmission system to carry many calls (known as trunking). The telephone exchange becomes a collection point, which aggregates tens, hundreds, or thousands of calls onto a single transmission link between exchanges. The same need exists for data networks like the Internet. Customer traffic is aggr ...
... transmission system to carry many calls (known as trunking). The telephone exchange becomes a collection point, which aggregates tens, hundreds, or thousands of calls onto a single transmission link between exchanges. The same need exists for data networks like the Internet. Customer traffic is aggr ...
Internet Indirection Infrastructure Ion Stoica Daniel Adkins Shelley Zhuang
... more flexible. IP multicast offers a receiver a binary decision of whether or not to receive packets sent to that group (this can be indicated on a per-source basis). It is up to the multicast infrastructure to build efficient delivery trees. The i3 equivalent of a join is inserting a trigger. This ...
... more flexible. IP multicast offers a receiver a binary decision of whether or not to receive packets sent to that group (this can be indicated on a per-source basis). It is up to the multicast infrastructure to build efficient delivery trees. The i3 equivalent of a join is inserting a trigger. This ...
CS-TR-05-02 - Michigan Technological University
... performed by the encryption key of the path’s last hop, while the outermost layer uses the encryption key of the path’s first hop. The onion routers co-operate and forward the onion from the sender to the destination. Tor [12] is the second generation Onion Routing [25] protocol. It uses a modified ...
... performed by the encryption key of the path’s last hop, while the outermost layer uses the encryption key of the path’s first hop. The onion routers co-operate and forward the onion from the sender to the destination. Tor [12] is the second generation Onion Routing [25] protocol. It uses a modified ...
Networks and Network Security - Nicolas T. COURTOIS` research in
... • Stateful filter: change filtering rules based on previously seen packets… – no limit to how complex they can be… ...
... • Stateful filter: change filtering rules based on previously seen packets… – no limit to how complex they can be… ...
WRC-1000 Wireless Routing Center
... Information" This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses an ...
... Information" This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses an ...
Cisco Nexus 1000V Series Switches
... Nexus 1000V offers support for VXLAN based overlay segments in addition to vlan based segments. Virtual eXtensible LAN (VXLAN) is an IETF proposed draft from Cisco and other industry vendors, to address new requirements for scalable LAN segmentation and stretching L2 segments across physical topolog ...
... Nexus 1000V offers support for VXLAN based overlay segments in addition to vlan based segments. Virtual eXtensible LAN (VXLAN) is an IETF proposed draft from Cisco and other industry vendors, to address new requirements for scalable LAN segmentation and stretching L2 segments across physical topolog ...
XM-500 XM to Ethernet Gateway Module Users Guide
... In no event will Rockwell Automation, Inc. be responsible or liable for indirect or consequential damages resulting from the use or application of this equipment. The examples and diagrams in this manual are included solely for illustrative purposes. Because of the many variables and requirements as ...
... In no event will Rockwell Automation, Inc. be responsible or liable for indirect or consequential damages resulting from the use or application of this equipment. The examples and diagrams in this manual are included solely for illustrative purposes. Because of the many variables and requirements as ...
Chapter 5 Advanced Configuration
... to recognize some of these applications and to work properly with them, but there are other applications that may not function well. In some cases, one local computer can run the application properly if that computer’s IP address is entered as the default DMZ server. Incoming traffic from the Intern ...
... to recognize some of these applications and to work properly with them, but there are other applications that may not function well. In some cases, one local computer can run the application properly if that computer’s IP address is entered as the default DMZ server. Incoming traffic from the Intern ...
A Novel Power Efficient Location-Based Cooperative Routing with
... Cooperative routing has been identified as an effective and useful method of reducing the negative effects of fading in Wireless Sensor Networks (WSNs). WSNs have numerous potential applications, e.g., environmental monitoring, mineral survey, traffic control and disaster response. In practical appl ...
... Cooperative routing has been identified as an effective and useful method of reducing the negative effects of fading in Wireless Sensor Networks (WSNs). WSNs have numerous potential applications, e.g., environmental monitoring, mineral survey, traffic control and disaster response. In practical appl ...
RAD Katalog 2016
... RAD is the anchor of the RAD Group, an affiliation of ICT manufacturing companies often cited as one of the world’s premier generators of hi-tech innovation. A unique business philosophy distinguishes the RAD Group, which has no holding company but is strategically guided by its founders. Each compan ...
... RAD is the anchor of the RAD Group, an affiliation of ICT manufacturing companies often cited as one of the world’s premier generators of hi-tech innovation. A unique business philosophy distinguishes the RAD Group, which has no holding company but is strategically guided by its founders. Each compan ...
SwitchBlade® x908 [Rev ZJ]
... enables powerful centralized management and zerotouch device installation and recovery »»Console management port on the front panel for ease of access »» Eco-friendly mode allows ports and LEDs to be disabled to save power »»Web-based Graphical User Interface (GUI) »» Industry-standard CLI with cont ...
... enables powerful centralized management and zerotouch device installation and recovery »»Console management port on the front panel for ease of access »» Eco-friendly mode allows ports and LEDs to be disabled to save power »»Web-based Graphical User Interface (GUI) »» Industry-standard CLI with cont ...
20110310-OSG-NPW-Diagnostics
... • Internet2/ESnet engineers will help members and customers debug problems if they are escalated to us – Goal is to solve the entire problem – end to end – Involves many parties (typical: End users as well as Campus, ...
... • Internet2/ESnet engineers will help members and customers debug problems if they are escalated to us – Goal is to solve the entire problem – end to end – Involves many parties (typical: End users as well as Campus, ...
A Performance Comparison of Wireless Ad Hoc Network
... IP prefix: block of destination IP addresses AS path: sequence of ASes along the path ...
... IP prefix: block of destination IP addresses AS path: sequence of ASes along the path ...
VLSM and CIDR
... Internet is a collection of autonomous systems (AS) • Each AS is administered by a single entity • Each AS has its own routing technology Routing protocol used within AS is Interior Gateway Protocol Routing protocol used between Autonomous Systems is an Exterior Gateway ...
... Internet is a collection of autonomous systems (AS) • Each AS is administered by a single entity • Each AS has its own routing technology Routing protocol used within AS is Interior Gateway Protocol Routing protocol used between Autonomous Systems is an Exterior Gateway ...














![SwitchBlade® x908 [Rev ZJ]](http://s1.studyres.com/store/data/008053519_1-53b0e3770fa5647be537fdbf48703248-300x300.png)