An Incentive Driven Lookup Protocol For Chord-Based Peer-to-Peer (P2P) Networks
... some specific protocol as suggested by the network designer. We believe that such assumptions do not always hold good in large-scale open systems and have to be done away with in order to make P2P systems reliable, robust and realize their true commercial potential. Moreover, it has been pointed out ...
... some specific protocol as suggested by the network designer. We believe that such assumptions do not always hold good in large-scale open systems and have to be done away with in order to make P2P systems reliable, robust and realize their true commercial potential. Moreover, it has been pointed out ...
EDTECH 552, lab 4 Lab 4.1 Convert Numbers among the binary
... first 64 bits, or first four hextets, and the host portion, which is identified by the last 64 bits, or last four hextets. Remember that each number, or character, in an IPv6 address is written in hexadecimal, which is equivalent to four bits. The following is a typical global unicast address: The n ...
... first 64 bits, or first four hextets, and the host portion, which is identified by the last 64 bits, or last four hextets. Remember that each number, or character, in an IPv6 address is written in hexadecimal, which is equivalent to four bits. The following is a typical global unicast address: The n ...
Arctic networking properties
... communicating parties must know each other's public keys in order to be able to authenticate ...
... communicating parties must know each other's public keys in order to be able to authenticate ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... 1.1Ethernet Interconnect In computer networking, Gigabit Ethernet (GbE or 1 GigE) is a term describing various technologies for transmitting Ethernet frames at a rate of a gigabit per second (1,000,000,000 bits per second), as defined by the IEEE 802.3-2008 standard [4]. TCP/IP is a communication pr ...
... 1.1Ethernet Interconnect In computer networking, Gigabit Ethernet (GbE or 1 GigE) is a term describing various technologies for transmitting Ethernet frames at a rate of a gigabit per second (1,000,000,000 bits per second), as defined by the IEEE 802.3-2008 standard [4]. TCP/IP is a communication pr ...
Bluetooth Wireless System
... – provides a common interface between the Bluetooth host and a Bluetooth module • Interfaces in spec 1.0: USB; UART; RS-232 ...
... – provides a common interface between the Bluetooth host and a Bluetooth module • Interfaces in spec 1.0: USB; UART; RS-232 ...
D_UCY_WP4_41_c2, Specification on E2E UMTS simulator
... system level simulation and characterisation of Enhanced UMTS access and core networks. This simulator will enable the evaluation of capacity gain, Radio Resource Management (RRM) mechanisms, Quality of Service (QoS) provisioning, and other parameters associated with the performance of Enhanced UMTS ...
... system level simulation and characterisation of Enhanced UMTS access and core networks. This simulator will enable the evaluation of capacity gain, Radio Resource Management (RRM) mechanisms, Quality of Service (QoS) provisioning, and other parameters associated with the performance of Enhanced UMTS ...
... Local Area Networking (LAN) is the term used when connecting several computers together over a small area such as a building or group of buildings. LAN’s can be connected over large areas. A collection of LAN’s connected over a large area is called a Wide Area Network (WAN). A LAN consists of multip ...
A Scheme for a Guaranteed Minimum Throughput Service
... the different desired throughputs of the flows. Summing up, like the best-effort service, in congestion the Assured Service cannot provide a desired minimum throughput to any flow. Congestion could be avoided using resource overprovisioning, that is, dimensioning network resources so that they are n ...
... the different desired throughputs of the flows. Summing up, like the best-effort service, in congestion the Assured Service cannot provide a desired minimum throughput to any flow. Congestion could be avoided using resource overprovisioning, that is, dimensioning network resources so that they are n ...
ALPINE 3800 SERIES
... scalability, flexibility, security and management features required to build complete enterprisewide networks, including large campuses, branch offices, data centers and wiring closets. The Alpine 3800 series switches enable enterprise networks to adopt new technologies, such as wireless and Voice-o ...
... scalability, flexibility, security and management features required to build complete enterprisewide networks, including large campuses, branch offices, data centers and wiring closets. The Alpine 3800 series switches enable enterprise networks to adopt new technologies, such as wireless and Voice-o ...
Distance Vector Routing Protocols
... Passive interface command – Used to prevent a router from sending updates through an interface – Example: • Router(config-router)#passive-interface interface-type interface-number ...
... Passive interface command – Used to prevent a router from sending updates through an interface – Example: • Router(config-router)#passive-interface interface-type interface-number ...
CCNA5.0 Instructor PPT - Bina Darma e
... routers as sign posts along the path to the final destination. A link-state routing protocol is like having a complete map of the network topology. The sign posts along the way from source to destination are not necessary, because all link-state routers are using an identical map of the network. A l ...
... routers as sign posts along the path to the final destination. A link-state routing protocol is like having a complete map of the network topology. The sign posts along the way from source to destination are not necessary, because all link-state routers are using an identical map of the network. A l ...
21-06-0664-00-0000-QoS_considerations_in_NIHO_v3
... Possibility to reuse the existing primitives in the draft, with some modifications: the network to network communication is not supported by the primitive MIH_Configure_Thresholds. To 21-06-000-00-000-QoSProposal.doc: ...
... Possibility to reuse the existing primitives in the draft, with some modifications: the network to network communication is not supported by the primitive MIH_Configure_Thresholds. To 21-06-000-00-000-QoSProposal.doc: ...
Computer Networks and Internets
... Printed in the United States of America. This publication is protected by Copyright and permission should be obtained from the publisher prior to any prohibited reproduction, storage in a retrieval system, or transmission in any form or by any means, electronic, mechanical, photocopying, recording, ...
... Printed in the United States of America. This publication is protected by Copyright and permission should be obtained from the publisher prior to any prohibited reproduction, storage in a retrieval system, or transmission in any form or by any means, electronic, mechanical, photocopying, recording, ...
TL-WN350G_350GD User Guide - TP-Link
... The TP-LINK TL-WN350G/TL-WN350GD 54M Wireless PCI Adapter will provide you the flexibility to install your PC in the most convenient location available, without the cost of running network cables. The Adapter's auto-sensing capability allows high packet transfer rate of up to 54Mbps for maximum thro ...
... The TP-LINK TL-WN350G/TL-WN350GD 54M Wireless PCI Adapter will provide you the flexibility to install your PC in the most convenient location available, without the cost of running network cables. The Adapter's auto-sensing capability allows high packet transfer rate of up to 54Mbps for maximum thro ...
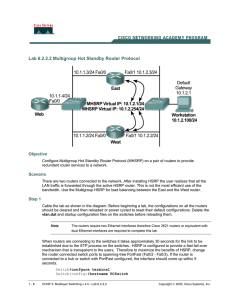
Lab 6.2.2.2 Multigroup Hot Standby Router Protocol
... then ping 10.1.1.4 again. Observe the lights on the routers and switch ports. Repeat this process several times using other valid IP addresses for the workstation. Notice the packets are forwarded over the same router each time. The HSRP active router is sitting idle. ...
... then ping 10.1.1.4 again. Observe the lights on the routers and switch ports. Repeat this process several times using other valid IP addresses for the workstation. Notice the packets are forwarded over the same router each time. The HSRP active router is sitting idle. ...
Metrics for Degree of Reordering in Packet Sequences
... Proceedings of the 27th Annual IEEE Conference on Local Computer Networks (LCN’02) 0742-1303/02 $17.00 © 2002 IEEE ...
... Proceedings of the 27th Annual IEEE Conference on Local Computer Networks (LCN’02) 0742-1303/02 $17.00 © 2002 IEEE ...
SCCP user adaptation layer(SUA)
... would create a DNS message flood in the DNS system as all connectionless msgs use E164/E212 numbers(if numbers gets cached, this problem may be reduced , but raises other issues) the response time from the DNS is unpredictable due to its hierarchical architecture. Would produce a WWW(world wide Wait ...
... would create a DNS message flood in the DNS system as all connectionless msgs use E164/E212 numbers(if numbers gets cached, this problem may be reduced , but raises other issues) the response time from the DNS is unpredictable due to its hierarchical architecture. Would produce a WWW(world wide Wait ...
BayStack LAN Switching
... the tool provides the ability to locate a failing end node and, with one mouse click, you have access to the RMON statistics for the failing Ethernet port supporting that end node. These solutions provide visual and statistical tools necessary to quickly resolve any network event or to manage perfor ...
... the tool provides the ability to locate a failing end node and, with one mouse click, you have access to the RMON statistics for the failing Ethernet port supporting that end node. These solutions provide visual and statistical tools necessary to quickly resolve any network event or to manage perfor ...
Reputation based Trust in Service-Oriented Network Environments by
... Our decisions are based on our estimation of how trustworthy a person is or how reliable a service is. Consequently, there has been a rise in trust systems that model human trust in a virtual or computing environment. These trust systems or trust models help to bridge the gap of human feelings and i ...
... Our decisions are based on our estimation of how trustworthy a person is or how reliable a service is. Consequently, there has been a rise in trust systems that model human trust in a virtual or computing environment. These trust systems or trust models help to bridge the gap of human feelings and i ...
Presentation - Constantia Fibre
... Speed of Deployment – The novel deployment methods enabled by the FOCUS™ technology reduces the need for civil construction methods and greatly accelerates the rate at which infrastructure can be deployed. FOCUS™ Backbone and last-mile networks are deployed five times faster than traditional trenchi ...
... Speed of Deployment – The novel deployment methods enabled by the FOCUS™ technology reduces the need for civil construction methods and greatly accelerates the rate at which infrastructure can be deployed. FOCUS™ Backbone and last-mile networks are deployed five times faster than traditional trenchi ...
CS610 Final term MAGA file.. all paperz are in 1 file..pages 1 to 42
... Answer: Protocol data unit (PDU) is an OSI term that refers generically to a group of information added or removed by a particular layer of the OSI model. In specific terms, an LxPDU implies the data and headers defined by layer x. Each layer uses the PDU to communicate and exchange information. The ...
... Answer: Protocol data unit (PDU) is an OSI term that refers generically to a group of information added or removed by a particular layer of the OSI model. In specific terms, an LxPDU implies the data and headers defined by layer x. Each layer uses the PDU to communicate and exchange information. The ...